AWS for M&E Blog
Deep packet inspection for securing high-value streaming content in the cloud
Today’s streaming platforms handle both high-value media, like premium sports, and confidential information, such as enterprise video communications. This evolution requires that the underlying infrastructure be protected with enterprise-grade security. Streaming is now essential infrastructure for businesses far beyond traditional media. It powers critical operations across industries, including secure financial announcements, HIPAA-compliant telemedicine, global manufacturing collaboration, online education, and sales-driving retail experiences.
For non-media businesses, streaming failures don’t just affect viewer experience—they can result in regulatory violations, competitive disadvantage, operational disruptions, and direct revenue loss.
Why packet inspection matters for live streaming
The global live streaming market has become a critical revenue driver for media companies, broadcasters, and content creators. Live streaming content faces unique security challenges that traditional network security solutions cannot address without compromising performance or creating coverage gaps. In specific scenarios, enterprise compliance, regulatory requirements, corporate IT policies, and security posture demands require deep packet inspection for live video ingestion and streaming workflows.
For security-conscious workload environments, protecting live stream content is essential across networks you don’t control. Unlike web traffic that tolerates security-induced latency, live video streams require consistent, low-latency delivery to maintain viewer experience and prevent revenue loss. A single security bottleneck can cause buffering, quality degradation, or stream interruptions that directly impact viewer engagement and business outcomes.
Important Note: This comprehensive security inspection architecture is designed for specific enterprise use cases with stringent security requirements. Most streaming deployments do not require this level of packet-level inspection.
This solution is primarily relevant for:
- Highly regulated industries (financial services, healthcare, government) with strict compliance requirements.
- High-value content (premium sports, confidential corporate communications) requiring maximum protection.
- Security-conscious enterprises with policies mandating comprehensive traffic inspection.
- Customers handling sensitive data where content integrity and audit trails are critical.
Standard streaming deployments using Amazon Web Services (AWS) Media Services already include robust security features. These features include encryption in transit, access controls, and network isolation that meet most security requirements without additional packet inspection.
The streaming content journey
The complex path that streaming content travels (from the source to the audience) reveals multiple security vulnerabilities that require specialized inspection capabilities. Video content begins at professional cameras, where hardware encoders convert raw footage into Internet-friendly formats using advanced compression like H.265 or AV1. This creates multiple quality levels for different network conditions and viewer devices.
Once encoded, streams get wrapped in specialized transport protocols designed for real-time delivery. Secure Reliable Transport (SRT) is the standard choice for professional broadcasting, because it includes built-in error correction, encryption, and configurable buffering to balance latency against reliability.
These streams traverse multiple network segments: last-mile ISP networks with varying security standards, Internet backbone infrastructure managed by different customers, and content delivery networks before reaching the AWS Global Infrastructure. Each network hop represents a security boundary where content can be intercepted or modified.
Security vulnerabilities in the streaming pipeline
Streaming infrastructure has become a high-value target because of its visibility and business impact. The real-time nature and performance requirements of streaming protocols create attack vectors that don’t exist in traditional web applications, making specialized security inspection essential.
SRT streams can be hijacked when encryption keys are compromised. Real-time Transport Protocol (RTP) streams are vulnerable to packet injection attacks where malicious actors insert unauthorized content, and control protocols, like Real-time Transport Control Protocol (RTCP), are spoofed to disrupt stream quality. The User Datagram Protocol (UDP) transport is susceptible to volumetric flooding attacks that overwhelm streaming infrastructure.
Attackers use streaming servers to amplify distributed denial-of-service (DDoS) attacks, as well as intercept and modify streams during network transit. Attackers also redirect traffic through malicious infrastructure using Border Gateway Protocol (BGP) hijacking techniques. DNS poisoning attacks redirect viewers to fake streaming endpoints designed to steal credentials or distribute malware.
Attackers exploit the real-time nature of streaming to splice unauthorized content, advertisements, or malicious payloads directly into live streams. Quality degradation attacks deliberately corrupt video or audio to damage broadcaster reputation, while sophisticated attackers remove watermarks or inject AI-generated deepfake content into legitimate streams.
Compliance and regulatory requirements
Modern streaming operations must meet stringent regulatory requirements that mandate comprehensive traffic inspection and detailed audit capabilities. To name a few:
- Broadcasting operations need FCC compliance.
- Financial services require SEC-compliant communications.
- Healthcare customers must follow FDA guidelines.
- Government agencies require FISMA and FedRAMP compliance.
Comprehensive packet inspection is essential for meeting these requirements through detailed content handling logs and forensic analysis capabilities for incident response. They also automate compliance reporting and technical validation of content integrity throughout the delivery process.
Technical inspection requirements
Streaming security systems must balance comprehensive inspection capabilities with strict performance constraints. These systems must parse SRT, RTP, RTCP, and WebRTC protocols in real-time, examining video and audio payloads for anomalies while validating stream metadata, timestamps, and quality metrics.
Live streaming applications tolerate only a small, additional amount of latency—far less than traditional security appliances. These systems must support high throughput for 4K content while maintaining consistent packet timing to prevent jitter. They must also scale dynamically to handle thousands of concurrent streams during peak events.
This complex security landscape demonstrates why traditional network security appliances cannot protect streaming workloads without significant performance compromises or security gaps.
The solution
Our solution architecture provides immediate business value through reduced security risk, maintained streaming performance, streamlined compliance reporting, and cost-effective scaling. It helps customers protect their high-value streaming content without sacrificing the viewer experience that drives revenue.
AWS services: The foundation
Following are some of the AWS services that shape the foundation for our solution and why they are important. Media Services on AWS provide the essential building blocks for professional streaming workflows.
AWS Elemental MediaConnect (MediaConnect) serves as the secure ingestion point, handling network variability, automatic error correction, and protocol conversion while maintaining low latency. AWS Elemental MediaLive (MediaLive) processes these streams, providing real-time video encoding, format conversion, and multi-bitrate output generation. Together, they create a robust foundation for professional streaming workflows.
Both services include built-in security features: MediaConnect provides encryption in transit, IP whitelisting, and Amazon Virtual Private Cloud (Amazon VPC) integration, while MediaLive offers input security groups, encrypted outputs, and IAM integration. Services can be integrated through direct connections without VPC routing, RTP/UDP connections for low-latency scenarios, VPC outputs for network isolation, or through intermediate processing layers for enhanced security inspection.
For standard deployments, these native security capabilities provide comprehensive protection. However, customers with specific compliance requirements need additional security layers that analyze traffic content and metadata in real-time without disrupting the streaming workflow.
Gateway Load Balancer eliminates the traditional trade-off between comprehensive security inspection and streaming performance through transparent, scalable architecture that delivers:
- 100 percent traffic inspection without compromising streaming performance through transparent packet-level security that adds low latency, while maintaining full visibility into all streaming traffic.
- Elastic security scaling that automatically adjusts inspection capacity based on streaming demand, verifying consistent performance during peak events, while optimizing costs during low-traffic periods.
- Enterprise-grade reliability with multi-availability zones (AZs) deployment, automatic failover, and health monitoring that maintains streaming availability during security appliance failures.
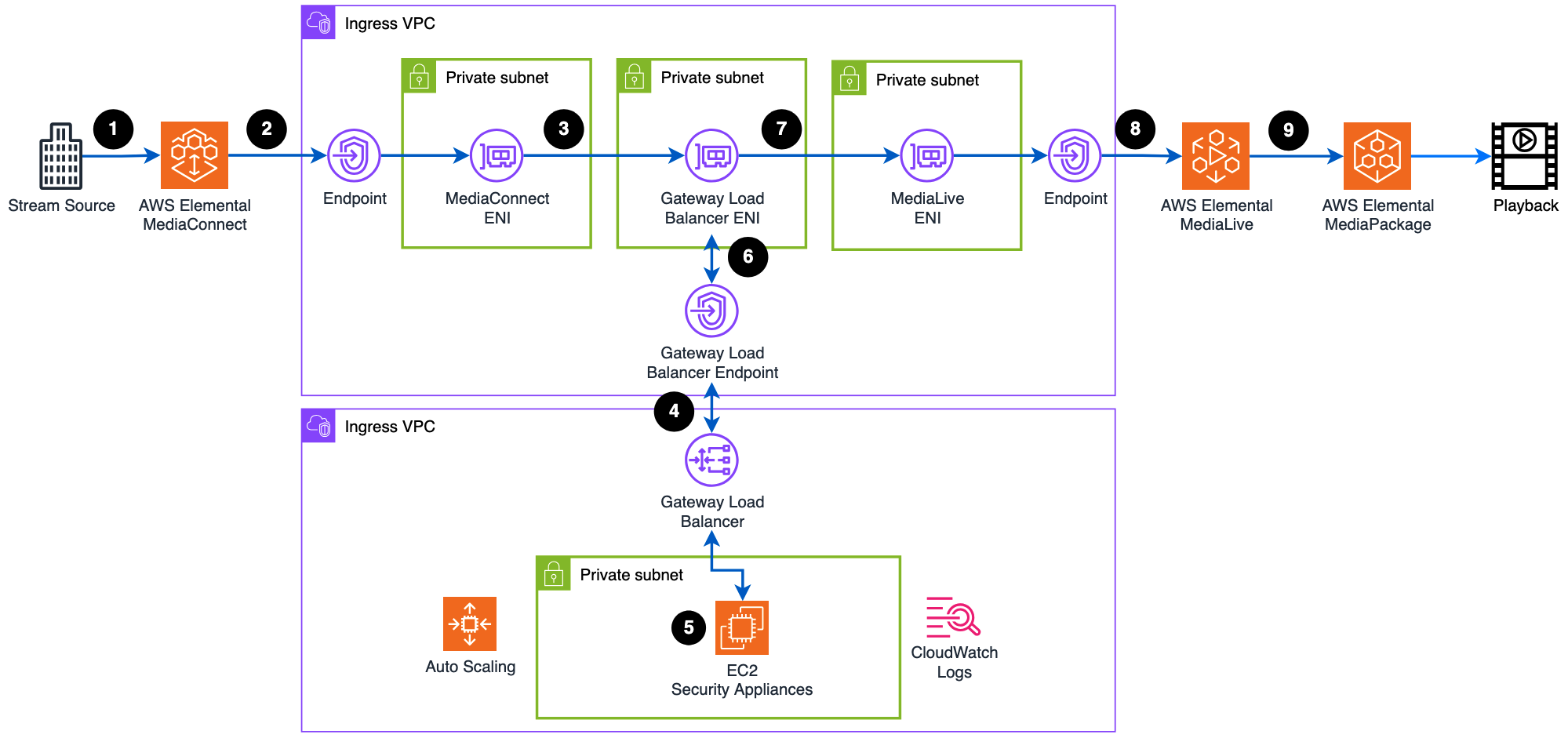
How the solution works: Step-by-step traffic flow
Understanding how video streams flow through the secure inspection architecture reveals the solution’s effectiveness and transparency. The following walkthrough details each step of the process, from the moment a video stream enters the system until it’s ready for distribution.
Step 1: SRT stream arrival. Live video content arrives using the SRT protocol, the industry standard for professional broadcasting. SRT provides built-in error correction and maintains low latency for high-quality streaming. The stream connects to MediaConnect from an allowlist of IP addresses and is encrypted using the built-in encryption capabilities of MediaConnect. Please note that SRT isn’t a must; MediaConnect supports multiple ingestion protocols including RIST, RTP, SRT and Zixi for flexibility across different source equipment.
Step 2: MediaConnect processing. MediaConnect converts SRT input into Real-time Transport Protocol with Forward Error Correction (RTP-FEC), streams and delivers them to a logically isolated Amazon Virtual Private Cloud (Amazon VPC) where traffic is inspected. We chose RTP for our ease of use, however, MediaConnect supports multiple VPC output types including SMPTE 2110 and RIST protocols.
Step 3: Transparent traffic routing. All RTP traffic from MediaConnect is automatically routed through Gateway Load Balancer endpoints using configured VPC route tables. This creates a “bump-in-the-wire” architecture where every packet gets inspected transparently.
Step 4: GENEVE encapsulation. The Gateway Load Balancer receives RTP traffic and wraps it using the Generic Network Virtualization Encapsulation (GENEVE) protocol. GENEVE preserves original packet information while adding metadata needed for inspection. The load balancer distributes traffic across security appliances using intelligent flow hashing for even distribution and session consistency. For more details on this you can read Introducing Gateway Load Balancer and Scaling Threat Prevention on AWS with Suricata.
Step 5: Deep packet inspection. Network-optimized Amazon Elastic Cloud Compute (Amazon EC2) security appliances receive GENEVE-wrapped packets on UDP port 6081. Each appliance may run inspection software that analyzes RTP headers and payload data in real-time, including protocol validation, bitrate monitoring, content scanning, and security threat detection. The appliances are deployed in an AWS Auto Scaling group that automatically adjusts capacity based on traffic load.
Step 6: Inspection decision. Each security appliance makes a forwarding decision, and the traffic is sent back to the Gateway Load Balancer with its GENEVE wrapper, while suspicious or malformed traffic is flagged for further analysis. Every inspection decision is logged to Amazon CloudWatch, giving you complete visibility into what is happening with your streams.
While this implementation demonstrates a custom security appliance, customers can choose from enterprise-grade partner solutions available through the AWS Marketplace. AWS Partners can offer purpose-built security appliances that integrate with Gateway Load Balancer. They help provide advanced threat detection, intrusion prevention, and deep packet inspection with vendor support and proven performance for production streaming workloads.
Step 7: Traffic restoration. The Gateway Load Balancer receives the inspected traffic from security appliances and removes the GENEVE headers, restoring the original RTP packet structure. The traffic continues its journey to MediaLive through the Gateway Load Balancer endpoint. The entire inspection process adds latency.
Step 8: MediaLive input processing. AWS Elemental MediaLive receives the inspected RTP streams across multiple AZs for high availability. MediaLive validates the streams and begins the video and audio processing pipeline, including decoding, format conversion, and preparation for various output formats.
Step 9: Output and distribution. MediaLive processes your inspected streams and generates outputs in the formats you need. Through integration with AWS Elemental MediaPackage, you can receive HTTP Live Streaming (HLS) endpoints ready for distribution to content delivery networks, storage in Amazon Simple Storage Service (Amazon S3), or integration with other AWS media services. All your output streams maintain the quality and integrity that was verified during the inspection phase.
The complete reference implementation, including AWS Cloud Development Kit (AWS CDK) code in TypeScript, security appliance configurations, and deployment automation, is available in our GitHub repository. The repository includes step-by-step deployment guides, configuration examples, and operational utilities for managing the streaming security architecture.
Automatic scaling and stream management coordination
As your streaming traffic increases, the AWS Auto Scaling group automatically launches additional security appliances. New instances are registered with the Gateway Load Balancer target group as soon as they pass their health checks. If instances fail, they’re terminated and replaced without interruption to your traffic flow.
Our solution architecture includes a command-line stream management utility (scripts/operations/stream-control.sh) that coordinate scaling operations with streaming workflows. During stream startup, the management system scales the AWS Auto Scaling group to the desired capacity (two instances for redundancy). It waits for all targets to become healthy in the Gateway Load Balancer target group and then starts MediaConnect flows and MediaLive channels. This sequenced approach verifies that security inspection is operational before streaming traffic begins flowing.
During a stream shutdown the management utility follows the reverse sequence. It stops the MediaLive channels, stops the MediaConnect flows, and scales the AWS Auto Scaling group down to zero instances to minimize costs. This coordinated approach prevents orphaned resources and confirms clean shutdowns, while maintaining cost efficiency. The entire scaling and coordination process is automated through Infrastructure as Code (IaC)—providing consistent and reliable stream lifecycle management.
Network isolation
The solution architecture uses two isolated VPCs: the Stream Processing VPC (10.0.0.0/16) and the Security Inspection VPC (10.1.0.0/16). Security groups implement least-privilege access with port ranges for RTP (5000-5100) and RTCP (5001-5101) traffic. VPC Flow Logs capture all network activity for security analysis and compliance reporting.
Getting started with deployment
For customers ready to implement this streaming security architecture, the reference implementation on GitHub provides automated deployment through AWS CDK with straightforward configuration.
Prerequisites
The following prerequisites need to be in place before implementing our solution:
- AWS Command Line Interface (AWS CLI): Configured with appropriate permissions
- Conda: For initial environment set up and management
- FFmpeg: Install FFmpeg with SRT support across different operating systems
Deployment steps
Following are the steps needed to deploy our solution:
- Clone the reference implementation
git clone https://github.com/aws-samples/sample-stream-inspection-blog
cd sample-stream-inspection-blog
- Create and activate the Conda environment
conda env create -f environment.yml
conda activate stream-inspection
- Install dependencies and build
npm install && npm run build
- Deploy with your current IP (recommended for testing)
npx cdk deploy StreamInspectionBlogStack \
--parameters WhitelistCidr=$(curl -s https://checkip.amazonaws.com)/32
Post-deployment
After deployment, verify the architecture using the included utilities:
- Start streaming infrastructure
npm run stream:start
- Generate test stream
npm run stream:generate
- Stop streaming infrastructure when finished
npm run stream:stop
Production deployment best practice recommendations
The following recommendations are best practices you should consider before deploying this solution in production:
- High availability: Deploy MediaConnect flows and MediaLive channels across multiple AZs with automatic failover. Use dual-path ingestion and priority-based input switching.
- Security hardening: Configure security appliances with hardened OS, with automated patching through AWS Systems Manager and AWS Secrets Manager (for credentials). Add compliance controls for regulated industries.
- Performance optimization: Disable cross-zone load balancing to reduce latency by 2-4 ms. Deploy multiple instances for each AZ, for resiliency while maintaining optimal performance.
Conclusion
Our solution demonstrates how security-focused customers can achieve comprehensive streaming security without compromising performance. By combining Gateway Load Balancer with different AWS media services, customers gain transparent security inspection that scales automatically and integrates seamlessly with existing workflows.
The architecture addresses the core challenge for security-conscious streaming operations: protecting high-value content while maintaining performance standards. However, some streaming deployments may not require this level of inspection. AWS media services already provide robust security features including encryption, access controls, and network isolation for typical applications.
Ready to enhance your streaming security? Start by exploring the complete reference implementation on GitHub, which includes deployment guides, AWS CDK code in TypeScript, and operational utilities. You can also explore the Gateway Load Balancer documentation or contact an AWS representative to discuss whether this architecture addresses your specific requirement.