AWS Cloud Financial Management
Automating Budget Management Across Multi-Account Environments
Managing AWS spending across multiple accounts demands a sophisticated approach to budget control and monitoring. Our custom solution enables centralized budget management with automated email notifications, allowing organizations to set and enforce account-specific budgets from a central management account. This automated system tracks spending across individual accounts and delivers timely alerts when accounts approach or exceed their allocated budgets. The central management account serves as a single source of truth, where finance teams can configure unique budget thresholds for each account and receive notifications about spending patterns across accounts in the entire organization.
Solution Overview
Our solution implements an event-driven architecture that automates budget management across your AWS Organization. The process starts in the management account, where account-specific budgets are defined and stored in an Amazon DynamoDB table. AWS Lambda function automatically propagate these budget configurations to individual accounts through their respective AWS Systems Manager (SSM) Parameter Stores. AWS Budgets monitors spending in real-time, triggering email notifications when accounts approach or exceed their allocated thresholds. This streamlined architecture eliminates manual budget management while providing teams the flexibility to operate within their defined cost constraints.
Solution Architecture
Components of the Solution:
AWS Control Tower Management Account:
- DynamoDB Table stores the budget information for each linked account.
- Lambda Function is triggered by updates to the DynamoDB table and updates the budgets in spoke accounts using AWS Systems Manager.
Linked Account:
- AWS SSM Parameter Store holds the updated budget value.
- Amazon CloudWatch Events trigger automation when the AWS SSM parameter is updated.
- Budgets manages the account’s cost based on these parameters.
- Budgets sends email notifications if the budget threshold is exceeded.
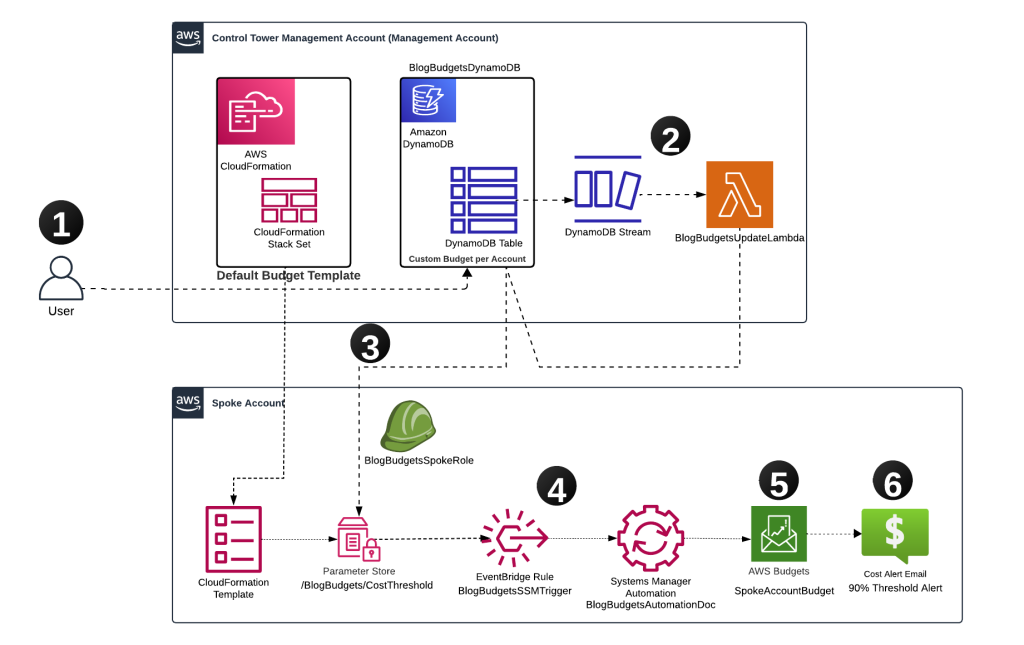
Budget Management Architecture & Flow Diagram
Workflow:
- Update DynamoDB Table: The user updates the budget value for a linked account in the DynamoDB table (BlogBudgetsDynamoDB) located in the management account.
- DynamoDB Stream Trigger: This update triggers an DynamoDB stream, which in turn triggers the Lambda function (BlogBudgetsUpdateLambda) in the management account.
- Lambda Function Updates AWS SSM Parameter: The Lambda function reads the updated budget value from the DynamoDB table, assumes a cross-account role (BlogBudgetsSpokeRole), and updates the SSM Parameter Store (/BlogBudgets/CostThreshold) in the spoke account with the new budget value.
- Amazon EventBridge Rule Trigger: When the SSM Parameter Store in the spoke account is updated, an EventBridge Rule (BlogBudgetsSSMTrigger) triggers the AWS SSM Automation document (BlogBudgetsAutomationDoc) in the spoke account.
- Budgets Update: The AWS SSM Automation document in the spoke account reads the updated budget value from the SSM Parameter Store and updates the Budgets (SpokeAccountBudget ) value accordingly.
- Email Notifications: When spending reaches configured thresholds, the system sends informational notifications to designated stakeholders.
Solution Operation:
- Based on the service behavior, when you update the budget value for an account, the budget limit in Budgets is updated accordingly. However, there are a few important things to keep in mind regarding alerts:
- Even if you update the budget value after an alert has been triggered, the alert status remains in “Exceeded” (or whichever state it was in when triggered). The alert will not reset just because you modified the budget limit.
It can take up to 8 hours for the new budget status to reflect in the alert system, which means that any changes made to the budget may not immediately update the alert’s status.
Example Scenario:
- Suppose you set a monthly budget of $100 with an alert at 100% of actual.
- During the month, you exceed the budget and spend $200.
- The alert will be triggered, and you will receive a notification indicating that the budget has been exceeded.
- Even if you later increase the budget to $250 (to account for additional expenses), the alert will remain in the “Exceeded” state until the end of the month.
This function is because the alert state is based on actual spending and the initial budget limit at the time of the alert, not the updated limit. This behavior ensures that you stay aware of any breaches and prevents automatic resetting of alerts that could miss important spending patterns.
Prerequisites
- AWS Account Setup
- AWS Organizations or AWS Control Tower with multi-account structure
- Management account
- At least one spoke account
- Required access to AWS Services
- AWS Budgets
- AWS Lambda
- Amazon DynamoDB
- AWS Systems Manager
- Amazon CloudWatch
- AWS CloudFormation
- Access Requirements- ensure you have the following minimum least privilege permissions in your AWS accounts:
- Management Account
- AWS CloudFormation deployment permissions
- DynamoDB table management access
- Lambda function and CloudWatch logs monitoring
- Cross-account AWS Identity and Access Management (IAM) role management
- Spoke Accounts
- AWS CloudFormation template deployment permissions
- Read-only access to monitor EventBridge rules, Systems Manager parameters and automations, and Budgets
- Management Account
- Email address for budget notifications
- The detailed deployment steps will be covered in the following sections of the blog.
Solution Deployment
1. Deploy the Management Account Stack (AWS Control Tower Management Account or Master Billing Account)
In the management account, deploy the ‘budget_mgmt_account.yaml’ CloudFormation Stack, click here to download the template.
This template will deploy:
- An DynamoDB table that stores the budget values for each spoke account.
- An Lambda function that will be triggered by the DynamoDB stream to update the SSM Parameter Store (specifically, /BlogBudgets/CostThreshold) in each spoke account with the new budget values.
- AWS IAM roles with the necessary permissions for the Lambda function, including cross-account access.
2. Deploy Spoke Account Stack
You can set up the spoke account stack in one of the following ways:
- Option 1: Deploy the ‘budget_spoke_account.yaml’ AWS CloudFormation Stack directly in the respective spoke account
- Option 2: Alternatively, you can use AWS CloudFormation StackSets from the management account to automatically deploy the template across multiple spoke accounts. This method is ideal if you’re managing many spoke accounts and want to simplify the deployment process.
3.Update the DynamoDB Table
After deploying the solution:
- Access the management account.
- Navigate to the DynamoDB table named ‘BlogBudgetsDynamoDB’.
- For each spoke account, add a new item:
- ‘AccountId’: Enter the 12-digit spoke account ID e.g. 111122223333
- ‘BudgetValue’: Set the desired budget amount (as a number) e.g. 1000
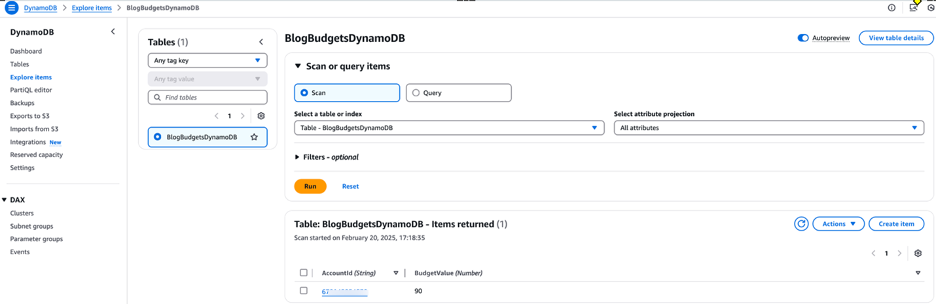
Figure 2: Amazon DynamoDB Table for budgets
Once the DynamoDB table is updated with the account details and budget values, the Lambda function ‘BlogBudgetsUpdateLambda’ will be triggered automatically by the DynamoDB stream to update the SSM Parameter Store in each spoke account with the new budget values.
4. Updating SSM Parameter Store
After assuming the cross-account role, the Lambda function updates the SSM Parameter Store in the spoke account with the new budget value (e.g., /BlogBudgets/CostThreshold). This step ensures that the budget information is reflected in the spoke account and ready for further actions.
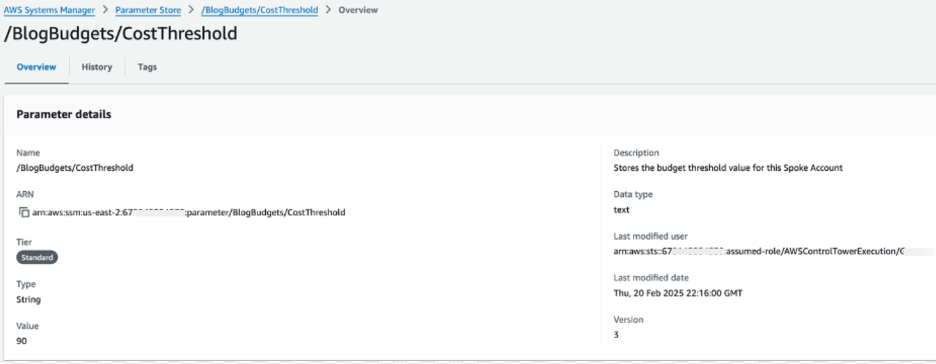
Figure 3: AWS SSM Parameter for Cost Threshold
5. Amazon Event Bridge Rule Triggers
The updated value in the SSM Parameter Store triggers an CloudWatch Event Rule. This rule monitors changes in the AWS SSM parameter and fires off an event whenever the /BlogBudgets/CostThreshold parameter is updated.
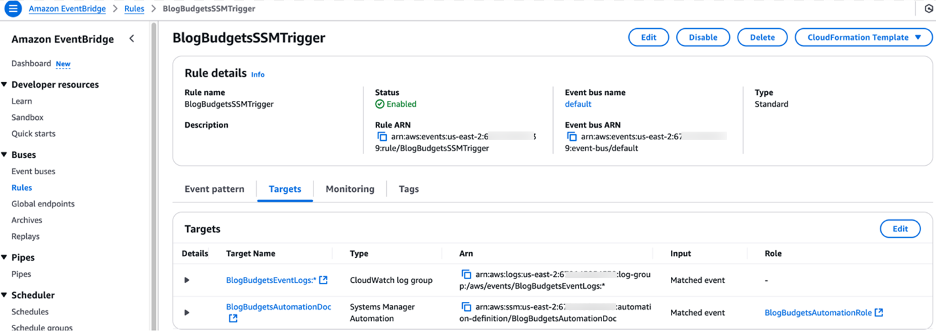
Figure 4: AWS SSM Invocation EventBridge Rule
6. SSM Automation Kicks In
The CloudWatch Event automatically triggers the execution of an SSM Automation document in the spoke account. This document performs the action of updating the Budgets value based on the new budget parameter value stored in the SSM Parameter Store.
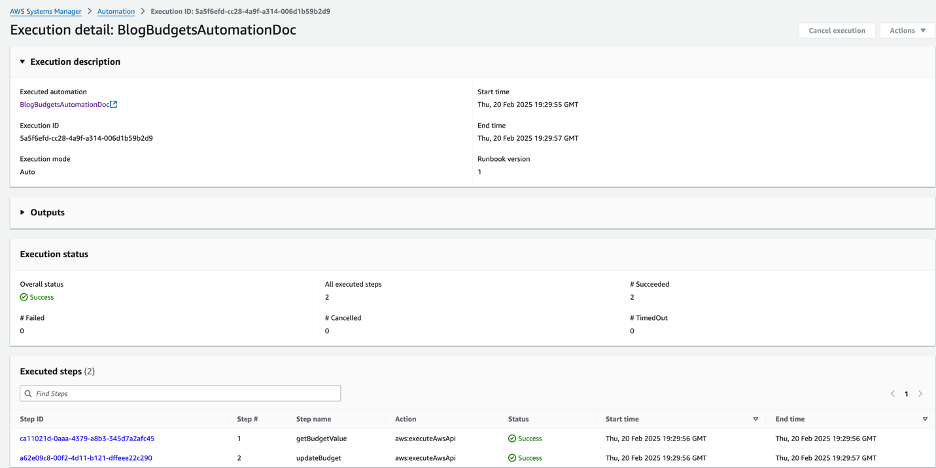
Figure 5: Budget Update AWS SSM Automation
7. Budgets Update
The AWS SSM Automation document updates the Budgets configuration in the spoke account. This ensures that the new budget value is set in Budgets, where it will be used to track and monitor costs.
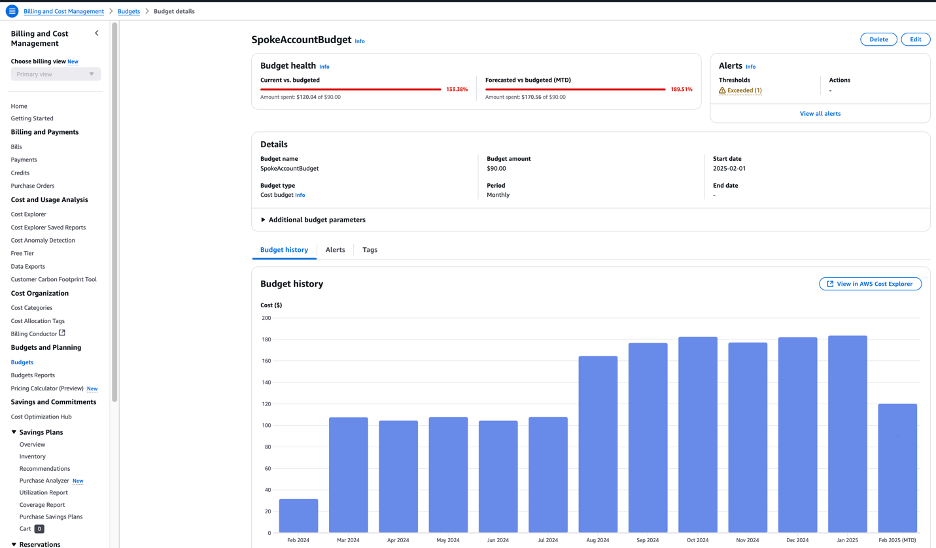
Figure 6: Updated AWS Budgets Configuration
8. Email Alert Notification:
Once the budget value is updated in Budgets, the configured budget alert thresholds are checked. If the current spending exceeds the threshold, an email alert is triggered. This email will notify the designated recipients about the budget breach, ensuring timely action can be taken.
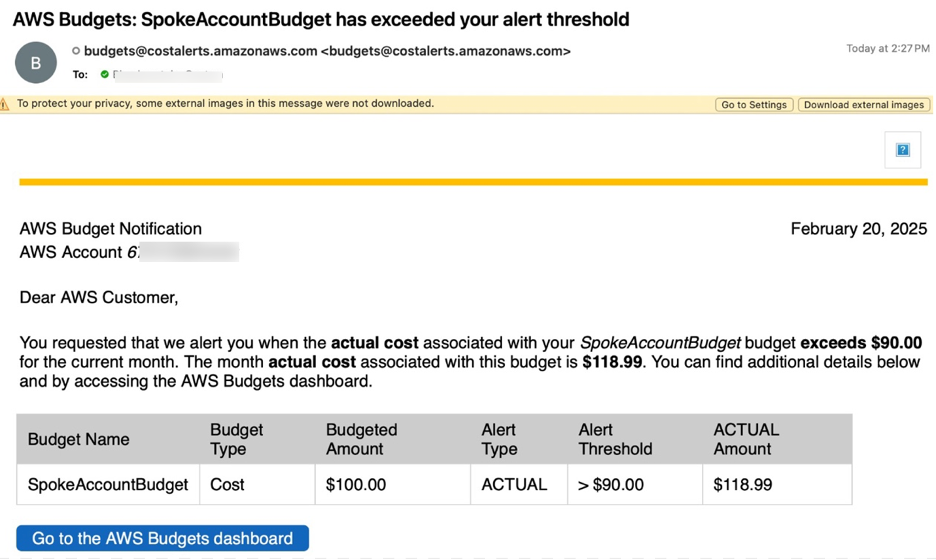
Figure 7: AWS Budgets threshold email notification
Cleaning Up
To avoid incurring future charges, delete the resources deployed for testing the solution in your environment by deleting the AWS CloudFormation stacks deployed.
Future Enhancements
Enable Remediation Actions
To further enhance this solution and ensure tighter control over AWS costs, you can consider implementing remediation actions using AWS Budget Actions. These actions allow you to automatically trigger responses to manage costs when your budget thresholds are exceeded. A Budget Action is a feature in Budgets that enables you to define automated cost-saving responses whenever a predefined budget alert is triggered. This ensures that actions are taken without manual intervention, reinforcing a cost-conscious culture in your organization. You can attach remediation actions to your budget alerts, which can be configured to trigger actions when the budget exceeds a certain threshold (either actual or forecasted spending). This can be particularly useful in avoiding unintentional overspending. For example:
- IAM Policy: You can apply a custom “Deny EC2 Run Instances” IAM policy to a user, group, or role when the EC2 budget is exceeded.
- Target Specific Instances: You can define an action to stop EC2 instances within a certain region when the budget for EC2 usage is breached.
This capability enables organizations to implement automated cost optimization responses based on their defined thresholds, helping maintain alignment with financial objectives.
Integrate with ServiceNow for ITSM Workflow Automation
Another possible future enhancement is integrating this solution with ServiceNow for seamless IT Service Management (ITSM) workflow automation. By integrating Budgets and remediation actions with ServiceNow, organizations can automatically create tickets or incidents when a budget threshold is exceeded. These incidents can then trigger predefined workflows in ServiceNow, such as notifying relevant teams or initiating cost-optimization processes. For example:
- When a budget alert exceeds a certain threshold, an incident could be created in ServiceNow to alert the finance or cloud operations team.
- ServiceNow can automatically escalate the issue to higher-level teams or initiate corrective actions, such as requesting approval to scale down resources or conduct a cost review.
- This integration streamlines communication between financial and operational teams, automating ticketing and ensuring issues are promptly addressed.
Conclusion
This solution provides an automated and scalable way to manage Budgets across multiple accounts, leveraging tools like DynamoDB, SSM Parameter Store, Lambda, and Budgets. It helps organizations monitor costs and receive timely notifications when budgets are exceeded. Future enhancements, such as integrating Budgets Actions for automatic remediation and linking the solution with ServiceNow for ITSM workflow automation, will further streamline cost management and improve response times to budget breaches. By adopting this solution, organizations can maintain better control over their AWS costs and ensure that they stay within budget while optimizing their cloud expenditures.
Solution is available in AWS-SAMPLES-REPO https://github.com/aws-samples/sample-event-driven-budget-management-on-aws