AWS Partner Network (APN) Blog
Enhance Cloud Identity Security with BeyondTrust on AWS
By: John Brunot, Partner Solutions Architect – AWS
By: Brian Hanrahan, VP of Product Management – BeyondTrust
 |
| BeyondTrust |
 |
The AWS cloud provides enhanced security features, scalable infrastructure that enables organizations to modernize applications and respond rapidly to market demands. BeyondTrust complements AWS’s comprehensive security capabilities by offering additional identity and access controls that help customers implement their security requirements and enhance security for sensitive resources. In this guide, discover the power of the joint approach, and how you can unlock the benefits.
Defining Identity Security for the Cloud
Identity security implements protection measures for both human and machine digital identities while managing access to systems, applications, and data. It combines Identity and Access Management (IAM), Privileged Access Management (PAM), Cloud Infrastructure Entitlements Management (CIEM), Identity Detection Threat Response (ITDR), authentication, and continuous monitoring.
Figure 1: An illustration of the importance and complexity of identity security and interconnected systems to corporate environments
6 Essential Identity Security Controls for Cloud Environments
With the above identity security definition in mind, here are six key-ways identity security controls can help take full advantage of the AWS cloud to reach your business outcomes:
1. Just in Time (JIT) Access
JIT access limits elevated permissions to exact moments of need, reducing standing privileges that could be exposed to unauthorized users. When used with AWS Identity and Access Management (IAM), organizations can implement JIT access to manage secrets, elevated permissions to cloud infrastructure, SaaS applications, and enhance security monitoring for remote access.
2. Enhanced Security Features for Remote Access (RA)
Enhanced security features for Remote Access (RA) enables organizations to implement zero trust principles for both human and machine accounts accessing resources from any location. Enhanced security features for RA extends Privileged Access Management (PAM) best practices globally and can complement traditional VPN and VDI technologies.
Organizations using JIT remote access controls gain several benefits:
- Enhanced visibility through comprehensive session monitoring
- Streamlined compliance documentation with AWS CloudTrail integration
- Automated access controls for distributed workforce management
For example, financial services organizations can efficiently manage remote access across regions while maintaining security controls and regulatory compliance. The solution provides detailed audit trails of user activities and system impacts through integrated AWS CloudTrail logs.
3. Password Management
Enterprise password managers provide automated credential lifecycle management, including generation, vaulting, and protection across all account types. Organizations gain centralized visibility and control while reducing manual credential management tasks.
Healthcare organizations using AWS infrastructure can implement automated credential rotation and access controls to help support their HIPAA compliance programs and security requirements.
4. Secrets Management
Secrets management provides DevOps teams with automated tools to protect sensitive information throughout the development lifecycle. This capability supports just-in-time access in code, configuration, and runtime environments, including Amazon Elastic Kubernetes Service (Amazon EKS).
Organizations can centrally manage machine and workload account credentials while maintaining comprehensive audit trails. This approach helps strengthen security controls and supports compliance requirements through automated rotation and access management.
For example, retail organizations managing thousands of machine and workload accounts can implement centralized secrets management that helps ensure:
- Enhanced security features for storing sensitive information
- Automated credential rotation
- Access limited to authorized processes
- Comprehensive audit trails visible to information security and compliance teams
5. Cloud Entitlements Management
Just-in-Time (JIT) entitlements management helps organizations align access permissions with actual usage patterns. This approach is designed to provide necessary permissions when needed and remove them when not in use.
Key benefits of JIT entitlements management include:
- Reduced accumulation of unused permissions over time
- Streamlined periodic entitlements reviews
- Enhanced visibility into access patterns across cloud environments
For example, a manufacturing company can implement continuous monitoring of access permissions across its global AWS infrastructure. This approach helps maintain proper access controls while supporting operational efficiency.
JIT entitlements management supports least privilege principles by:
- Automating temporary elevated access for specific tasks
- Providing detailed audit trails of permission usage
- Enabling fine-grained access controls based on job functions.
6. Identity Threat Detection and Response (ITDR)
Identity Threat Detection and Response (ITDR) solutions offer monitoring capabilities for identity-based activities across cloud, hybrid, and on-premises environments. These solutions typically use graph analysis to map connections among identities, accounts, configurations, and permissions. This approach helps identify potential access paths and detect anomalies that may indicate unauthorized activity.
When used alongside cloud-native security tools like AWS IAM Access Analyzer, ITDR solutions can support least privilege principles. They help organizations verify that only necessary users and devices have access to sensitive resources.
For example, technology companies can implement automated monitoring of access patterns across development, staging, and production environments. This approach helps protect intellectual property while maintaining developer productivity.
When evaluating ITDR vendors, consider those with:
- AWS Security Competency certification
- Technical integrations with AWS services
- Validated AWS solutions
- Alignment with AWS security best practices
BeyondTrust, an AWS Security Competency Partner, offers ITDR capabilities designed to complement AWS security services. This combination can help streamline security and compliance management across your AWS environments.
AWS Security
AWS provides cloud services designed to be secure with established guidelines for security, compliance, access control, and hardening. Through the AWS Competency Program, partners demonstrate expertise in building solutions with enhanced security features. BeyondTrust achieved the AWS Security Competency in April 2024, enabling implementation of AWS security best practices with specialized identity security features.
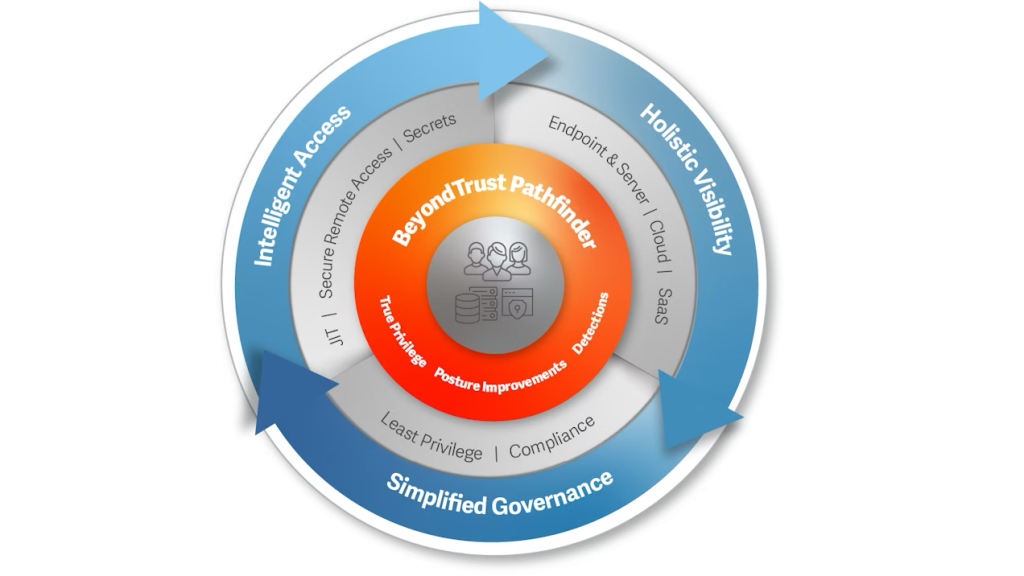
BeyondTrust and the Pathfinder Platform
The BeyondTrust Pathfinder Platform delivers identity security through AWS-hosted Software-as-a-Service (SaaS). The platform helps organizations address cloud and hybrid security challenges through these capabilities:
- Centralized visibility into identity risks across endpoints, servers, Identity Providers (IdPs), and cloud environments, with prioritized findings
- Management of credentials for both human and workloads
- JIT access control that provides:
- Least-privilege permissions for cloud and SaaS resources
- Time-bound, granular self-service remote access
- Enhanced security features for employees, vendors, and workloads
- CIEM that combines JIT least-privilege controls with remote and credential access in a single interface
- ITDR and Identity Security Posture Management (ISPM) to help you address critical security risks across AWS and on-premises environments
Figure 2: The BeyondTrust Pathfinder Platform – a modern, unified solution for identity security
With BeyondTrust Pathfinder, organizations can also leverage AI/ML and key integrations to find, manage, and protect the Paths to Privilege™, supporting enhanced access controls in cloud environments.
The Pathfinder platform delivers additional capabilities that help organizations to reduce identity-based risks and prioritize the most impactful remediations, all in one place. This includes:
True Privilege™ Graph and Continuous Risk Assessment:
Provides visual privilege mapping and dynamic analysis of access pathways across environments.
“BeyondTrust’s solution has impacted our business by giving us peace of mind around the security of our customers’ data and also giving us a very robust audit trail to ensure the integrity of that at all times and allowing us to put in the appropriate safeguards to ensure we’re always in front of any potential security vulnerabilities.”
– Shane Carden, CIO, Behavox
Pragmatic AI-Powered Security:
The Pathfinder platform simplifies identity security implementation with automated detection and efficient risk remediation.
“Our workflows were highly inefficient and there was a lot of friction and frustration. But BeyondTrust changed that with Identity Security Insights, and we can tailor our alert settings. This way, it significantly reduces unnecessary alerts. There’s more accurate threat detection which reduces our false positive rate and Insights, powered by AI and Machine Learning, adapts to my inputs. It learns from how I process detections and recommendations. It’s continuously evolving alongside my business.”
– Anna Essex, Sr. Security Analyst, Polsinelli
Adaptive Just-in-Time (JIT) Access:
The Pathfinder platform manages privileges across the entire identity estate using identity risk context for dynamic access decisions.
“Employees do the maximum using minimum permissions. [Billie] has embraced JIT access as a standard practice and now experiences a notable reduction in standing permissions. The task of reviewing user access has become manageable, thanks to Entitles system which efficiently supports a modern tech stack on a large scale.”
– BeyondTrust Customer at Billie
AWS & BeyondTrust: Security at Scale
AWS and AWS Partner BeyondTrust offer solutions designed to help customers:
- Implement identity security controls aligned with AWS best practices
- Streamline compliance reporting through automation
- Deploy identity management features that integrate with AWS services
Conclusion
Organizations looking to address identity-based security challenges can benefit from technologies designed to help manage modern IT security risks. The AWS and BeyondTrust partnership provide solutions that support cloud innovation while helping to enhance identity-related security controls.
To license BeyondTrust solutions from AWS, please visit the AWS Marketplace.
Learn more
 .
.
BeyondTrust – AWS Partner Spotlight
BeyondTrust is an AWS Advanced Technology Partner and AWS Security ISV Competency Partner BeyondTrust provides identity security solutions that help organizations protect privileged access in their AWS environments. They focus on preventing unauthorized access, detecting potential threats, and automating security controls. Their platform help customers manage identity security risks while maintaining operational efficiency. Their solutions serve 20,000 organizations globally, including most Fortune 100 companies, delivering comprehensive identity protection through AWS integration.