Desktop and Application Streaming
Connecting Amazon WorkSpaces Personal with AWS PrivateLink
Customers frequently ask how to leverage AWS PrivateLink to connect to Amazon WorkSpaces Personal. PrivateLink offers a seamless way to establish secure, private connections without the need for traditional networking components such as internet gateways, NAT devices, or VPN configurations. This approach not only simplifies network architecture but also enhances security by significantly reducing the attack surface and keeping all data traffic securely within the AWS network. In this blog, we will guide you step by step through the process of integrating PrivateLink with WorkSpaces, helping you unlock these benefits in your own environment.
Prerequisites and Limitations:
PrivateLink for WorkSpaces currently is supported for streaming traffic. Review the Admin Guide for details on the prerequisites and limitations with WorkSpaces. In order to setup PrivateLink you will first need to setup a security group, create the VPC Endpoint, and then finally configure the WorkSpace directory to use the VPC Endpoint.
Step 1: Create the security group
In this step, you create a security group that lets WorkSpaces clients communicate with VPC endpoint you’ll be creating.
- In the navigation pane of the Amazon EC2 console, go to Network & Security, then Security Groups.
- Select Create security group.
- Under Basic details, enter the following:
For Security group name – Enter a unique name that identifies the security group.
For Description – Enter some text that describes the purpose of the security group.
For VPC – Choose the VPC that your VPC endpoint is in. - Go to Inbound rules and select Add rule to create inbound rules for TCP traffic.
- Enter the following:
For Type – Choose Custom TCP.
For Port range – Enter the following port numbers: 443, 4195.
For Source type – Choose Custom.
For Source – Enter the private IP CIDR range or other Security Group IDs from which your users connect to the VPC endpoint. Make sure to allow inbound traffic from IPv4 address source only. - Repeat steps 4 and 5 for each CIDR range or Security Group.
- Go to Inbound rules, select Add rule to create inbound rules for UDP traffic.
- Enter the following:
For Type – Choose Custom UDP.
For Port range – Enter the following port numbers: 443, 4195.
For Source type – Choose Custom.
For Source – Enter the same private IP CIDR range or Security Group IDs entered in Step 5. - Repeat steps 7 and 8 for each custom UDP.
- Select Create security group.
Step 2: Create the VPC endpoint
In Amazon VPC, a VPC endpoint lets you connect your VPC to supported AWS services. In this example, you configure Amazon VPC so that your WorkSpaces users can stream from WorkSpaces.
- Open the Amazon VPC console.
- In the navigation pane, go to Endpoints, then Create Endpoint.
- Select Create Endpoint.
- Ensure the following:
Service category – Make sure that AWS services is selected.
Service Name – Choose com.amazonaws.Region.prod.highlander.
VPC – Choose a VPC in which to create the interface endpoint. You can choose a different VPC than the VPC with WorkSpaces resources as long as the network routes traffic to the VPC endpoint.
Enable Private DNS Name – The check box is selected. If your users use a network proxy to access streaming instances, disable any proxy caching on the domain and DNS names that are associated with the private endpoint. The VPC endpoint DNS name should be allowed through the proxy.
DNS record IP type – Choose IPv4. Dualstack and IPv6 DNS record IP type are currently not supported. If Dualstack or IPv6 is selected, you won’t be able to stream from WorkSpaces using the VPC endpoint.
Subnets – Choose the subnets (Availability Zones) to create the VPC endpoint. It is recommended that you choose at least two subnets.
IP address type – Choose IPv4.
Security groups panel – Select the security group you created earlier.
(Optional) In the Tags panel, you can create one or more tags. - Select Create endpoint.
- When the endpoint is ready to use, the value in the Status column changes to Available.
Step 3: Configure WorkSpaces directory to use the VPC endpoint
You need to configure the WorkSpaces directory to use the VPC endpoint that you created for streaming.
- Open the WorkSpaces console in the same AWS Region as the VPC endpoint.
- In the Navigation pane, select Directories, and then .
- Select the directory that you want to use.
- Go to the VPC Endpoints section, then Edit.
- In the Edit VPC Endpoint dialog box, under Streaming Endpoint, select the VPC endpoint you created.
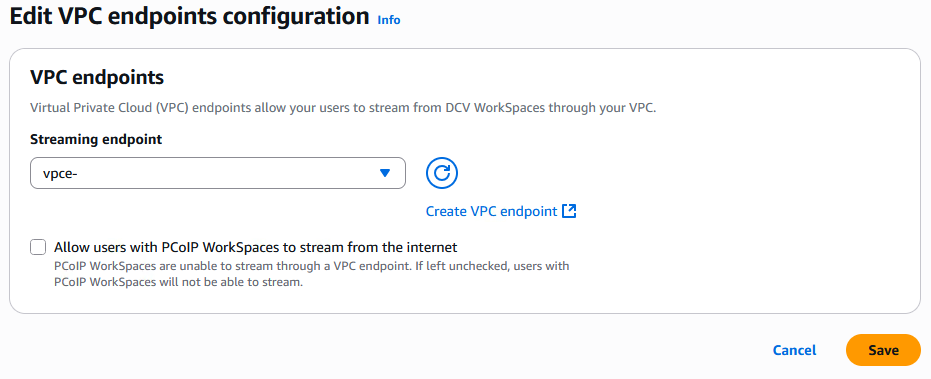
- Optionally, you can enable Allow users with PCoIP WorkSpaces to stream from the internet.
When enabled, your users are able to stream from their PCoIP WorkSpaces through public internet. Otherwise, the PCoIP WorkSpaces in the directory will become unreachable since PCoIP WorkSpaces do not support using a VPC endpoint for streaming. - Select Save.
Traffic for new streaming sessions will be routed through this VPC endpoint. However, traffic for current streaming sessions continues to be routed through the previously specified endpoint.
Conclusion
In this post, we discussed how to set up Amazon WorkSpaces Personal with PrivateLink. For additional information on PrivateLink checkout the product page. If you have any questions, please reach out to your AWS support team. For the latest on new features for End User Compute check out the Whats New with AWS and be sure check out our YouTube playlist.
 |
Dave Jaskie is a Senior AWS End User Compute Solutions Architect, bringing 15 years of experience in the end-user computing space. Outside of work, Dave enjoys traveling and hiking with his wife and 4 kids. |
 |
Aamir Khan, a seasoned Senior Technical Program Manager within the End User Computing Product team, boasts 12 years of industry expertise. Guided by a customer-first approach, his work methodology sets a standard. Beyond the professional realm, Aamir finds joy in family moments and indulges in occasional off-road escapades on his LC-100 series, exploring the wonders of the Pacific Northwest. |
 |
Anshu Prabhat is a Software Development Engineer III at AWS in the Secure Work Enablement Organization with over 12 years of experience in secure cloud computing and scalable services at Amazon. Anshu likes to learn and explore the world of GenAI and tries to automate mundane personal tasks using Agents. |
 |
Gekai Zou is Sr. Product Manager Technical in AWS End User Computing. Gekai has been with AWS since 2019. Outside of work, Gekai enjoys camping and skiing with his family. |