AWS Storage Blog
Rapid monitoring of Amazon S3 bucket policy changes in AWS environments
Enterprises today manage hundreds of access policies across their expanding cloud environments. As they scale their cloud infrastructure, maintaining visibility into policy changes becomes increasingly important. Central security teams can enhance their cloud governance by implementing comprehensive monitoring of access policies. This approach supports compliance efforts while strengthening overall resource security across their environments.
Users now store data across millions of Amazon S3 buckets in hundreds of accounts, and policy modifications can happen across different accounts and environments. S3 bucket policies are an important access control mechanism and cruicial to have least-privilege permissions in place to ensure that only authorized teams can make bucket policy changes. Implementing comprehensive change tracking allows organizations to enhance their monitoring capabilities, making sure of continuous visibility, compliance, and effective risk management for any authorized or unauthorized bucket policy modifications.
In this post, we demonstrate an automated solution that uses Amazon Web Services (AWS) CloudTrail, Amazon EventBridge, and Amazon Simple Notification Service (Amazon SNS) to monitor S3 bucket policy changes on your AWS account, providing organizations with quick insights and alerting mechanisms. By monitoring bucket policy changes, organizations can quickly detect and respond to unauthorized or prohibited modifications. This approach of monitoring and alerting on bucket policy changes enhances overall security posture and helps organizations maintain better control over their S3 access policies, data protection and regulatory compliance.
Solution overview
In this solution, we leverage CloudTrail to capture all policy modification events on S3 buckets. When authorized teams update bucket policies, CloudTrail records these API actions into CloudTrail logs. EventBridge rules filter these CloudTrail logs, specifically matching on event name for PutBucketPolicy, DeleteBucketPolicy, PutBucketAcl, and PutObjectAcl operations. The EventBridge rule targets an SNS topic configured with KMS encryption for secure message delivery. When policy changes occur, the SNS topic triggers an email notification containing the IP address, AWS Region, timestamp, bucket name, and AWS account ID of the modification. This enables security teams to track policy changes across their AWS environment quickly.
At a high-level, the solution works as follows:
- AWS CloudTrail captures all S3 bucket policy API actions
- Amazon EventBridge processes these events using custom rules
- Amazon SNS delivers email notification when changes occur
Figure 1 shows the solution architecture. This architecture is an example that uses email notifications to demonstrate how organizations can monitor and respond to S3 bucket policy changes. Although this solution showcases email notifications, users can modify the approach to create internal system tickets or trigger webhooks tailored to the operational requirement.
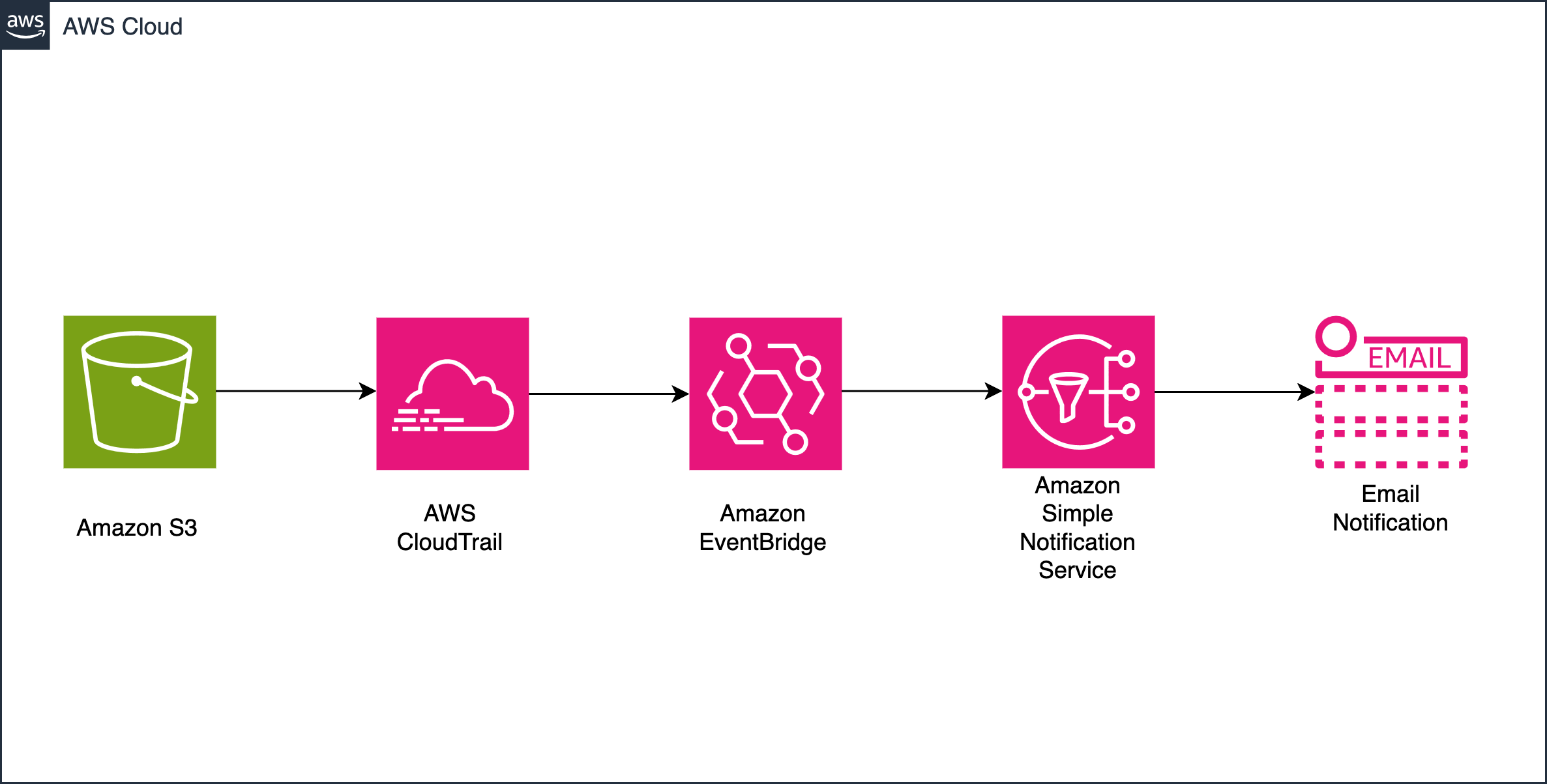
Figure 1: Rapid monitoring of Amazon S3 bucket policy changes in AWS environments with AWS CloudTrail, Amazon EventBridge, and Amazon SNS
Prerequisites
The following prerequisites are needed to complete this solution:
- AWS account
- S3 bucket
- CloudTrail is enabled
Walkthrough
The following steps walk you through this solution:
1. Deploy the CloudFormation template to create resources.
2. Confirm the SNS subscription for receiving notifications.
3. Receive policy change notifications for S3 bucket.
Step 1: Deploy the CloudFormation Template
You use this CloudFormation template to set up the solution resources. The CloudFormation stack creates an Amazon SNS topic for notifications, an AWS Key Management Service (AWS KMS) key for secure message encryption, and an EventBridge rule to track Amazon S3 policy changes on CloudTrail events.
To create, update, or delete stacks across multiple AWS accounts and Regions with a single operation, you can use CloudFormation StackSets.
1. Download the CloudFormation template (YAML)
2. On the CloudFormation console, choose the Region in which your CloudTrail is enabled to deploy this solution
3. Create a stack With new resources (standard), as shown in Figure 2.

Figure 2: Create a stack with new resources
4. Upload the YAML file, as shown in Figure 3.

Figure 3: Upload the YAML file
5. Provide a stack name and a Notification Email Address for the Amazon SNS subscription, as shown in Figure 4.

Figure 4: Provide your Stack name and email address
6. Optionally, choose an AWS Identity and Access Management (IAM) role for the stack. If no IAM role is chosen, then CloudFormation uses the credentials from the current user. Choose Next.
7. Review the Stack name and email address. Choose Submit.
The CloudFormation stack establishes a comprehensive monitoring setup for S3 bucket policy changes. CloudTrail captures detailed API activity logs, which EventBridge continuously monitors for S3 bucket policy changes. When CloudTrail logs an Amazon S3 policy modification event, EventBridge immediately triggers an SNS notification, making sure that you’re instantly alerted to S3 bucket policy changes. The following figure shows a list of resources created with the CloudFormation template.

Figure 5: CloudFormation resources and status
Step 2: Confirm the SNS Subscription
Choose the Confirm subscription link and confirm the subscription notification through the email.

Figure 6: Example email for Amazon SNS subscription confirmation
Step 3: Receive policy change Notifications
After confirming the Amazon SNS subscription, you should receive notifications for S3 bucket policy changes. To further customize notifications, you can use AWS Lambda functions with Amazon SNS notifications. Figure 7 is an example of a notification generated when an S3 bucket policy is updated. The notification provides comprehensive information to facilitate necessary action. It includes details such as the IP address, AWS Region, timestamp, bucket name, AWS account ID, and the updated policy details.

Figure 7: Example email for S3 bucket policy change notification
Cleaning up
To clean up your environment, you can delete the CloudFormation stack, which deletes the SNS topic, Amazon SNS subscription, AWS KMS key, and EventBridge rule.
Conclusion
In this post, we demonstrated an approach to monitor and alert on Amazon S3 bucket policy changes by leveraging AWS services such as CloudTrail, EventBridge, and SNS. The key steps involve configuring EventBridge rules to filter specific S3 policy events and setting up SNS topics for notifications. This solution provides a comprehensive and automated way to track policy modifications across your S3 buckets.
By thoughtfully combining these AWS capabilities, you can achieve reliable and quick detection of S3 bucket policy changes for your central security team. The core benefit is the ability to receive quick notifications containing detailed information about policy modifications, including who made the change, what was changed, and when it occurred. This allows for quick response to unauthorized changes, helps maintain a strong security posture, and supports audit trails for compliance purposes.
We encourage you to implement this S3 bucket policy monitoring solution in your AWS environment to enhance your security and governance. By taking advantage of this approach, you can improve your overall cloud security posture, ensure continuous compliance, and optimize your operational efficiency in managing S3 access controls. To get started, download the provided CloudFormation template and follow the step-by-step instructions in this post. For more information about S3 security best practices, visit the S3 User Guide.