AWS Storage Blog
Improve recovery resilience with AWS Backup support for Multi-party approval
Organizations must safeguard their backup infrastructure against evolving cyber threats. A comprehensive backup and recovery strategy needs three fundamental pillars: immutability with isolation to prevent tampering and ensure separation, integrity validation to ensure backup reliability, and predictable availability when needed. These pillars form the foundation of effective data protection. Immutability with isolation ensures that backups remain unchanged, indelible, and separated from production infrastructure, preserving their original state. Integrity validation confirms that backups are uncorrupted and restorable, providing confidence in their usability. Accessibility ensures predictable retrieval of backups when recovery becomes necessary, ensuring business continuity in critical situations. Together, these elements create a robust framework for safeguarding an organization’s most valuable asset—its data—against a wide range of potential threats and scenarios.
AWS Backup provides the foundation for a robust data resilience strategy, offering 99.999999999% (11 nines) durability by resiliently and redundantly storing backups across multiple Availability Zones (AZs). AWS Backup Vault Lock ensures immutability by prohibiting backup tampering, while AWS Backup restore testing validates backup integrity and seamlessly integrates with partner solutions to extend forensic analysis capabilities. AWS Backup maintains at least the same level of resilience and durability as the underlying AWS services being backed up, providing a strong foundation for your data protection strategy.
However, ensuring backup accessibility during critical security incidents requires additional controls beyond these native capabilities. When backup systems share authentication boundaries with production environments, a single compromised credential can impact both environments. This allows threat actors to encrypt production data, and block access to recovery mechanisms, potentially undermining the entire backup and recovery strategy.
In this two-part series, we start by exploring the threat vectors driving the need for a more robust approach, introduce the newly launched Multi-party approval integration with AWS Backup logically air-gapped vault and provide detailed steps to configure it in your AWS environment. In Part 2, we’ll provide detailed implementation guidance for configuring Multi-party approval workflows in your AWS environment, including best practices and practical examples.
Understanding the cascading risks in traditional recovery architectures
Existing backup and recovery strategies present an important architectural consideration: they commonly share the same authentication boundaries with the production environment that they’re meant to protect. Although access to data is governed by a properly implemented identity strategy, defining distinct authentication boundaries between production and backup systems makes sure of resilient recovery capabilities. However, this crucial separation is frequently overlooked. When backup systems are tightly coupled to source account credentials, a compromise of the production environment can cascade into the backup infrastructure. This creates a potential threat in AWS Organizations, where cross-account access patterns and shared authentication dependencies can amplify the blast radius of a security incident.
Consider a threat actor who gains elevated privileges in a production account. They could encrypt production data, and block access to the recovery mechanisms designed to restore operations. This challenge becomes even more critical as organizations scale, where a single credential compromise could impact business continuity across multiple accounts and workloads. The traditional approach of maintaining backup systems within the same trust boundary as production systems creates a single point of failure that evolving threat actors can exploit, turning what should be your last line of defense into a vulnerable target.
AWS security framework: building blocks for data protection
Serving as the foundation for scalable security, AWS Organizations allows businesses to deploy and manage multiple, interconnected defense-in-depth controls across their entire organization, creating a synergistic security posture. Service Control Policies (SCPs) act as guardrails to restrict permissions across accounts, while Resource Control Policies (RCPs) provide coarse-grained control over specific resources. AWS Identity and Access Management (IAM) permission boundaries constrain the permissions of IAM principals to ensure they align with the principle of least privilege and do not exceed what was originally intended. For security, AWS Key Management Service (AWS KMS) allows encryption with customer-managed keys to protect data for security, and cross-account copies ensure physical separation of backups for added resilience. However, while these controls are powerful, they still operate within a traditional single-approval framework—where individual administrators via an insider-attack or compromised credentials could potentially circumvent these protections.
Introducing Multi-party approval for AWS Backup logically air-gapped vault
To address this challenge, AWS Backup now supports Multi-party approval for AWS Backup logically air-gapped vault, enhancing security without compromising operational agility. Consider the following scenario. You’ve created immutable backups protected by AWS Backup Vault Lock and isolated them through service-owned encryption in an AWS backup logically air-gapped vault. During a ransomware incident, a threat actor gains root access to your backup account or the management account of your organization. While your backups remain safely stored, you will need to engage AWS Support to be able to regain access to the accounts.
Multi-party approval creates an independent access path to your backups requiring multiple approvers for critical operations, preventing unilateral changes through a distributed decision-making process, as shown in Figure 1. Using this native AWS functionality, you can associate an approval team or teams—consisting of highly trusted individuals—with your AWS Backup logically air-gapped vault. If your AWS accounts become inaccessible due to malicious actions, then these approval teams can authorize vault sharing requests from one or many recovery accounts, even one outside your current AWS Organizations. This improves your Recovery Time Objective (RTO) by removing immediate AWS Support engagement for gaining access to your backups needed for recovery.
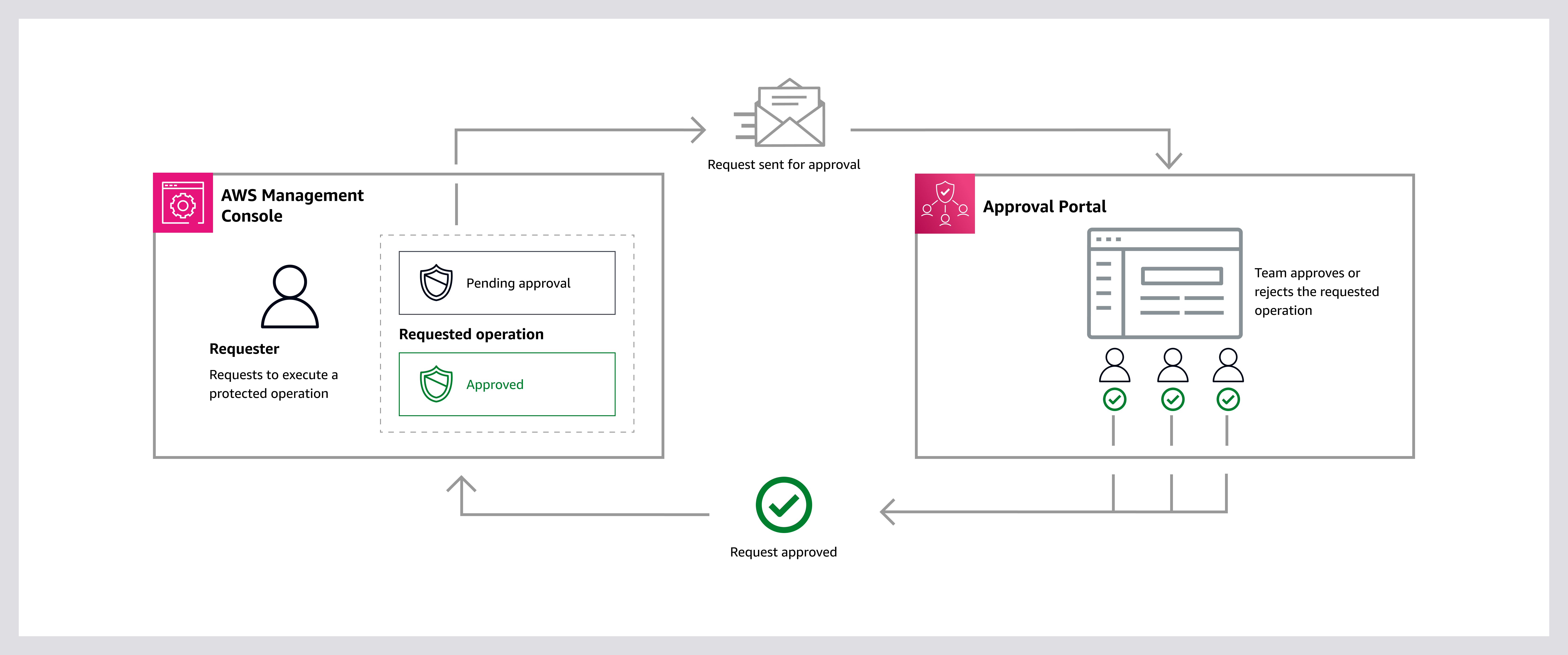
Figure 1: Multi-party approval workflow
Strategic use cases and deployment patterns
The integration of Multi-party approval with AWS Backup logically air-gapped vault creates a robust framework for data protection. Organizations subject to standards like Sheltered Harbor require their data vaults to maintain immutability, provide isolation from production infrastructure, and enable forensic validation of backup data integrity. AWS Backup logically air-gapped vault addresses these fundamental requirements through three key capabilities: it maintains backup immutability using a compliance mode lock, provides isolation from production infrastructure through logical air-gapping, and enables forensic validation of backup data integrity through seamless integration with AWS Backup restore testing. This architecture is particularly valuable for financial institutions and other regulated entities that must maintain secure, survivable data vaults that are fully separated from their primary infrastructure.
In the following sections we explore how organizations can strategically implement this capability across different scenarios. In particular, we dive deep into two critical use cases:
- AWS Account recovery: We examine how Multi-party approval enables recovery when a single AWS account hosting a logically air-gapped vault becomes inaccessible, making sure of business continuity even during critical security incidents.
- AWS Organizations recovery: We explore the more complex scenario of an entire Organizations structure becoming compromised, and how Multi-party approval provides a lifeline for recovery using an entirely separate identity framework.
AWS Account recovery
Consider a scenario where your primary AWS account hosting an AWS Backup logically air-gapped vault becomes completely inaccessible due to a security incident or credential compromise. Traditional recovery methods would need engagement with AWS Support, extending your business disruption. However, Multi-party approval workflows allow you to implement a predefined recovery strategy, as shown in the following figure.
The process begins with a proactive setup of a centrally managed Multi-party approval teams:
- Create a Multi-party approval team comprising trusted individuals from your organization.
- Share the approval team with your AWS Backup logically air-gapped vault during initial configuration.
- Associate the Multi-party approval team with the relevant AWS Backup logically air-gapped vault.
When an accessibility compromise occurs:
- Share the approval team with one or many recovery accounts using AWS Resource Access Manager (RAM).
- Designated recovery team members initiate vault sharing requests from one or many recovery accounts.
- The Multi-party approval workflow triggers, notifying approvers of a pending request to access the logically air-gapped vault.
- The approvers within the designated Multi-party approval team respond to the approval request, authorizing sharing.
- Upon receiving the required number of approvals from the approval team, the logically air-gapped vault becomes accessible in the recovery account.
- Recovery operations can now proceed using the backups in the logically air-gapped vault, independent of the compromised owning account.
This mechanism makes sure of business continuity while maintaining robust security controls, because no single individual can unilaterally access the backup data. The entire process uses native AWS interfaces, eliminating dependencies on the compromised account’s authentication systems and significantly reducing RTOs.
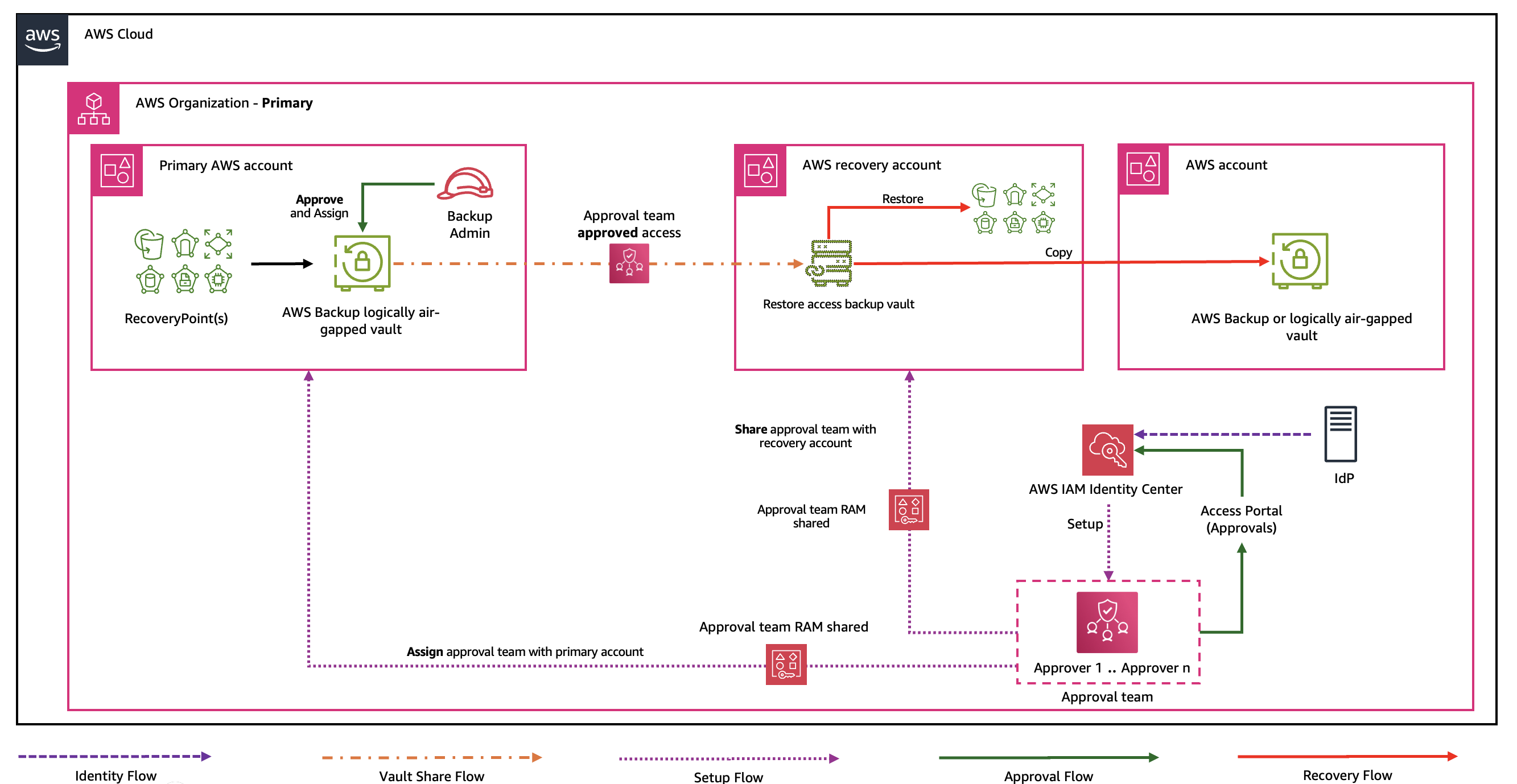
Figure 2: AWS cross-account Multi-party approval workflow
Implementing this architecture allows you to create a trusted recovery path that operates independently of your potentially compromised infrastructure. This provides a resilient solution for even the most critical security incidents.
AWS Organization recovery
Although the previous scenario addressed individual account compromise, organizations must also prepare for a situation where the entire AWS Organizations structure becomes inaccessible. This could occur due to a large-scale compromise, critical misconfigurations, compromise of the management account, or a malicious insider activity. In these cases, the recovery process needs an even more robust and independent trust model.
The process begins with a proactive setup of centrally-managed Multi-party approval teams, also shown in the following figure:
- Establish a recovery AWS Organizations separate from your primary infrastructure.
- Setup an independent Identity provider (IdP) in this recovery organization and associate it with Multi-party approval.
- Create a Multi-party approval team using this as a separate IdP, comprised of trusted individuals from your organization.
- Share this Multi-party approval team with your AWS Backup logically air-gapped vault account using AWS RAM.
- Associate the Multi-party approval team with the relevant AWS Backup logically air-gapped vault.
When an accessibility compromise occurs:
- Share the approval team with one or many recovery accounts using AWS Resource Access Manager (RAM).
- Designated recovery team members initiate vault sharing requests from one or many recovery accounts.
- The Multi-party approval workflow triggers, notifying team members of a pending request to access the logically air-gapped vault.
- The approvers within the designated Multi-party approval team respond to the approval request, authorizing sharing.
- Upon receiving the required number of approvals from the approval team, the logically air-gapped vault becomes accessible in the recovery account.
- Recovery operations can now proceed using the backups in the logically air-gapped vault, independent of the compromised owning account.
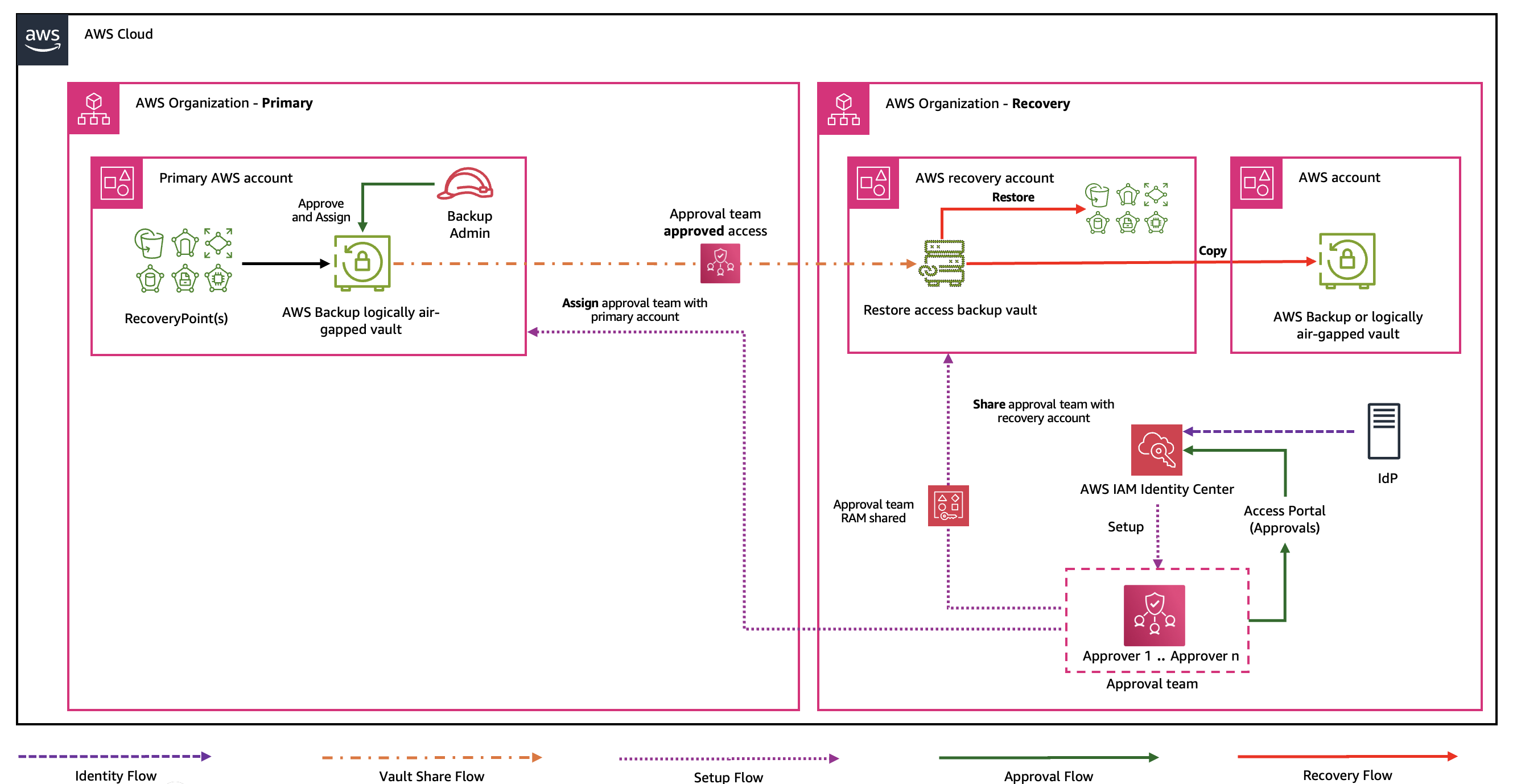
Figure 3: Cross-Organization Multi-party approval workflow
This cross-Organization architecture creates an independent recovery path that maintains access to critical backup data even when an entire Organization becomes inaccessible. Combining least privilege principles with separate identity controls allows it to provide the highest level of resilience for your most stringent compliance, regulatory, and security recovery scenarios.
High level reference architecture
The reference architecture for a robust AWS Backup implementation involves multiple layers of protection and validation, as shown in the following figure. In the primary workload account, production systems are backed up to a local AWS Backup vault. From there, a copy of these backups is sent to an AWS Backup logically air-gapped vault within the same account, providing another layer of isolation. To make sure of data integrity, this logically air-gapped vault is shared with a dedicated forensics account using the default sharing option through AWS Resource Access Manager (AWS RAM). In the forensics account, AWS Backup restore testing is conducted alongside third-party solutions to verify the integrity and recoverability of the backup data. This continuous validation process makes sure that backups remain uncorrupted and reliable.
For recovery scenarios, two paths are available. First, the default sharing through AWS RAM allows authorized users in the forensics account to access and validate backups under normal circumstances or for faster data loss recovery. Second, for situations where the primary account or entire Organization becomes inaccessible, Multi-party approval enables you to securely gain access to critical backups. This dual-path approach provides both day-to-day operational flexibility and a robust crisis recovery mechanism, making sure that critical data remains accessible and verifiably intact, regardless of the scale of a potential security incident.
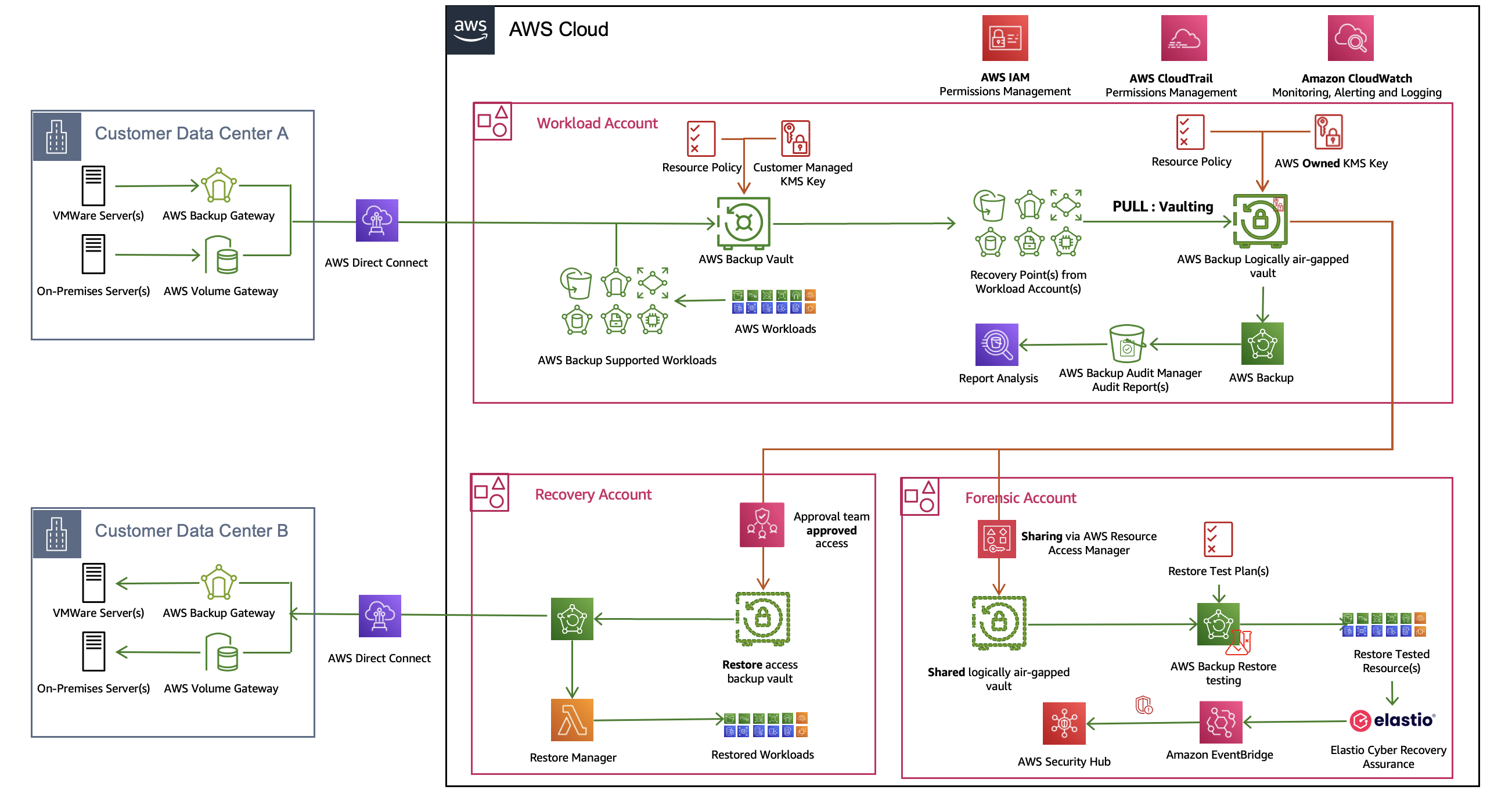
Figure 4: Reference architecture for AWS Backup
Conclusion
Effective recovery strategies need three critical pillars: immutability with isolation to prevent tampering and ensure separation, integrity validation to make sure of reliability, and predictable availability. AWS Backup delivers these through logically air-gapped vault with vault lock for immutability and isolation, AWS Backup restore testing for integrity validation, and now Multi-party approval workflows for making sure of reliable access to backups even during critical security incidents. Multi-party approval transforms your recovery strategy by enabling backup access whether recovering from a single-account incident or an organization-wide event. Its minimum necessary approvals-based decision flows and separate identity infrastructure make sure that your recovery paths remain viable when traditional authentication methods fail.
Consider integrating Multi-party approval into your existing recovery plans today to make sure that your organization maintains access to critical backup data during any scenario. Implementing these recovery patterns with clear separation of duties and independent identity mechanisms strengthens your organization’s ability to recover from any cyber incident. Always remember: your recovery strategy is only as strong as your ability to execute it when needed.