AWS Security Blog
Tag: Security Blog
Amazon Elastic Kubernetes Service gets independent affirmation of its zero operator access design
Today, we’re excited to announce the independent affirmation of our Amazon Elastic Kubernetes Service (Amazon EKS) zero operator access posture. Because security is our top priority at Amazon Web Services (AWS), we designed an operational architecture to meet the data privacy posture our regulated and most stringent customers want in a managed Kubernetes service, giving […]
Amazon discovers APT exploiting Cisco and Citrix zero-days
The Amazon threat intelligence teams have identified an advanced threat actor exploiting previously undisclosed zero-day vulnerabilities in Cisco Identity Service Engine (ISE) and Citrix systems. The campaign used custom malware and demonstrated access to multiple undisclosed vulnerabilities. This discovery highlights the trend of threat actors focusing on critical identity and network access control infrastructure—the systems […]
2025 H1 IRAP report is now available on AWS Artifact for Australian customers
Amazon Web Services (AWS) is excited to announce that the latest version of Information Security Registered Assessors Program (IRAP) report (2025 H1) is now available through AWS Artifact. An independent Australian Signals Directorate (ASD) certified IRAP assessor completed the IRAP assessment of AWS in September 2025. The new IRAP report includes four additional AWS services that are now assessed at […]
Introducing the Overview of the AWS European Sovereign Cloud whitepaper
Amazon Web Services (AWS) recently released a new whitepaper, Overview of the AWS European Sovereign Cloud, available in English, German, and French, detailing the planned design and goals of this new infrastructure. The AWS European Sovereign Cloud is a new, independent cloud for Europe, designed to help public sector organizations and customers in highly regulated […]
Migrating from Open Policy Agent to Amazon Verified Permissions
Application authorization is a critical component of modern software systems, determining what actions users can perform on specific resources. Many organizations have adopted Open Policy Agent (OPA) with its Rego policy language to implement fine-grained authorization controls across their applications and infrastructure. While OPA has proven effective for policy-as-code implementations, organizations are increasingly looking for […]
The attendee guide to digital sovereignty sessions at AWS re:Invent 2025
AWS re:Invent 2025, the premier cloud computing conference hosted by Amazon Web Services (AWS), returns to Las Vegas, Nevada, from December 1–5, 2025. This flagship event brings together the global cloud community for an immersive week of learning, collaboration, and innovation across multiple venues. Whether you’re a cloud expert, business leader, or technology enthusiast, re:Invent […]
Should I use managed login or create a custom UI in Amazon Cognito?
October 8, 2025: This blog post has been updated to include the Amazon Cognito managed login experience. The managed login experience has an updated look, additional features, and enhanced customization options. September 8, 2023: It’s important to know that if you activate user sign-up in your user pool, anyone on the internet can sign up […]
Defending against supply chain attacks like Chalk/Debug and the Shai-Hulud worm
Building on top of open source packages can help accelerate development. By using common libraries and modules from npm, PyPI, Maven Central, NuGet, and others, teams can focus on writing code that is unique to their situation. These open source package registries host millions of packages that are integrated into thousands of programs daily. Unfortunately, […]
Defending LLM applications against Unicode character smuggling
When interacting with AI applications, even seemingly innocent elements—such as Unicode characters—can have significant implications for security and data integrity. At Amazon Web Services (AWS), we continuously evaluate and address emerging threats across aspects of AI systems. In this blog post, we explore Unicode tag blocks, a specific range of characters spanning from U+E0000 to […]
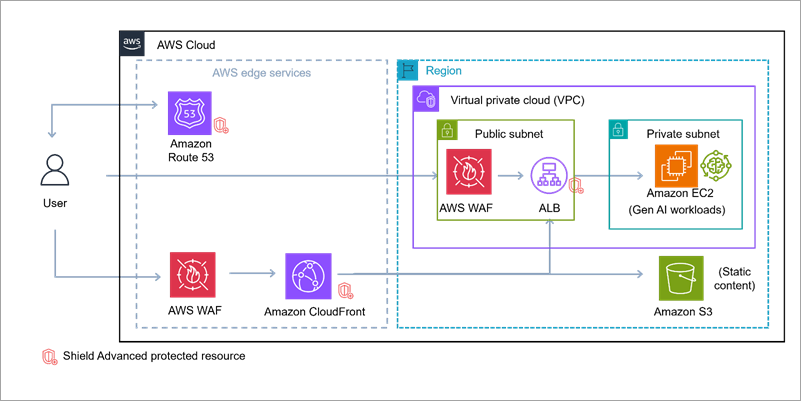
Build secure network architectures for generative AI applications using AWS services
As generative AI becomes foundational across industries—powering everything from conversational agents to real-time media synthesis—it simultaneously creates new opportunities for bad actors to exploit. The complex architectures behind generative AI applications expose a large surface area including public-facing APIs, inference services, custom web applications, and integrations with cloud infrastructure. These systems are not immune to […]