AWS Security Blog
Fall 2025 SOC 1, 2, and 3 reports are now available with 185 services in scope
Amazon Web Services (AWS) is pleased to announce that the Fall 2025 System and Organization Controls (SOC) 1, 2, and 3 reports are now available. The reports cover 185 services over the 12-month period from October 1, 2024–September 30, 2025, giving customers a full year of assurance. These reports demonstrate our continuous commitment to adhering to […]
Implementing data governance on AWS: Automation, tagging, and lifecycle strategy – Part 2
In Part 1, we explored the foundational strategy, including data classification frameworks and tagging approaches. In this post, we examine the technical implementation approach and key architectural patterns for building a governance framework. We explore governance controls across four implementation areas, building from foundational monitoring to advanced automation. Each area builds on the previous one, […]
Implementing data governance on AWS: Automation, tagging, and lifecycle strategy – Part 1
Generative AI and machine learning workloads create massive amounts of data. Organizations need data governance to manage this growth and stay compliant. While data governance isn’t a new concept, recent studies highlight a concerning gap: a Gartner study of 300 IT executives revealed that only 60% of organizations have implemented a data governance strategy, with […]
Streamline security response at scale with AWS Security Hub automation
A new version of AWS Security Hub, is now generally available, introducing new ways for organizations to manage and respond to security findings. The enhanced Security Hub helps you improve your organization’s security posture and simplify cloud security operations by centralizing security management across your Amazon Web Services (AWS) environment. The new Security Hub transforms […]
Fall 2025 PCI DSS compliance package available now
Amazon Web Services (AWS) is pleased to announce that two additional AWS services and one additional AWS Region have been added to the scope of our Payment Card Industry Data Security Standard (PCI DSS) certification: Newly added services: AWS Security Incident Response AWS Transform Newly added AWS Region: Asia Pacific (Taipei) This certification allows customers […]
AWS named Leader in the 2025 ISG report for Sovereign Cloud Infrastructure Services (EU)
For the third year in a row, Amazon Web Services (AWS) is named as a Leader in the Information Services Group (ISG) Provider LensTM Quadrant report for Sovereign Cloud Infrastructure Services (EU), published on January 9, 2026. ISG is a leading global technology research, analyst, and advisory firm that serves as a trusted business partner […]
Real-time malware defense: Leveraging AWS Network Firewall active threat defense
Cyber threats are evolving faster than traditional security defense can respond; workloads with potential security issues are discovered by threat actors within 90 seconds, with exploitation attempts beginning within 3 minutes. Threat actors are quickly evolving their attack methodologies, resulting in new malware variants, exploit techniques, and evasion tactics. They also rotate their infrastructure—IP addresses, […]
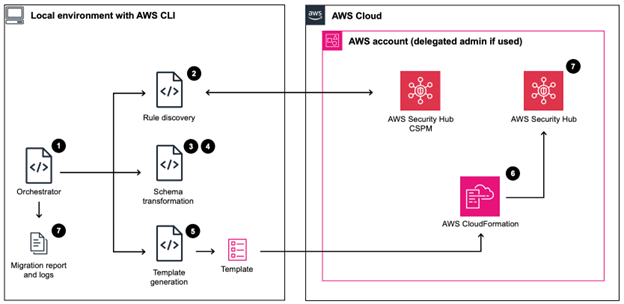
Security Hub CSPM automation rule migration to Security Hub
A new version of AWS Security Hub is now generally available with new capabilities to aggregate, correlate, and contextualize your security alerts across Amazon Web Services (AWS) accounts. The prior version is now known as AWS Security Hub CSPM and will continue to be available as a unique service focused on cloud security posture management […]
GuardDuty Extended Threat Detection uncovers cryptomining campaign on Amazon EC2 and Amazon ECS
Amazon GuardDuty and our automated security monitoring systems identified an ongoing cryptocurrency (crypto) mining campaign beginning on November 2, 2025. The operation uses compromised AWS Identity and Access Management (IAM) credentials to target Amazon Elastic Container Service (Amazon ECS) and Amazon Elastic Compute Cloud (Amazon EC2). GuardDuty Extended Threat Detection was able to correlate signals […]
What AWS Security learned from responding to recent npm supply chain threat campaigns
AWS incident response operates around the clock to protect our customers, the AWS Cloud, and the AWS global infrastructure. Through that work, we learn from a variety of issues and spot unique trends. Over the past few months, high-profile software supply chain threat campaigns involving third party software repositories have highlighted the importance of protecting […]