AWS Security Blog
Category: Amazon EC2
How to Protect Data at Rest with Amazon EC2 Instance Store Encryption
April 25, 2023: We’ve updated this blog post to include more security learning resources. Note: By default, an instance type that includes an NVMe instance store encrypts data at rest using an XTS-AES-256 block cipher. See this FAQ about NVMe-supported instance types. If you’re using an NVMw instance type, then data at rest is encrypted […]
How to Monitor AWS Account Configuration Changes and API Calls to Amazon EC2 Security Groups
You can use AWS security controls to detect and mitigate risks to your AWS resources. The purpose of each security control is defined by its control objective. For example, the control objective of an Amazon VPC security group is to permit only designated traffic to enter or leave a network interface. Let’s say you have […]
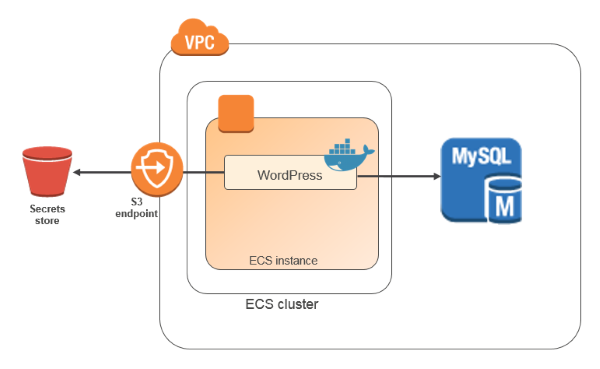
How to Manage Secrets for Amazon EC2 Container Service–Based Applications by Using Amazon S3 and Docker
Docker enables you to package, ship, and run applications as containers. This approach provides a comprehensive abstraction layer that allows developers to “containerize” or “package” any application and have it run on any infrastructure. Docker containers are analogous to shipping containers in that they provide a standard and consistent way of shipping almost anything. One […]
How to Automatically Tag Amazon EC2 Resources in Response to API Events
Note: As of March 28, 2017, Amazon EC2 supports tagging on creation, enforced tag usage, AWS Identity and Access Management (IAM) resource-level permissions, and enforced volume encryption. See New – Tag EC2 Instances & EBS Volumes on Creation on the AWS Blog for more information. Access to manage Amazon EC2 instances can be controlled using […]
How to Configure Your EC2 Instances to Automatically Join a Microsoft Active Directory Domain
Seamlessly joining Windows EC2 instances in AWS to a Microsoft Active Directory domain is a common scenario, especially for enterprises building a hybrid cloud architecture. With AWS Directory Service, you can target an Active Directory domain managed on-premises or within AWS. How to Connect Your On-Premises Active Directory to AWS Using AD Connector takes you […]
How to Help Lock Down a User’s Amazon EC2 Capabilities to a Single VPC
As a cloud support engineer, I am frequently asked this question: “How can I lock down my user’s Amazon EC2 access to a single VPC?” This blog post will answer the question and explain how you can help control this level of access through the use of AWS Identity and Access Management (IAM) policies and […]
Granting Permission to Launch EC2 Instances with IAM Roles (PassRole Permission)
When you launch an Amazon EC2 instance, you can associate an AWS IAM role with the instance to give applications or CLI commands that run on the instance permissions that are defined by the role. When a role is associated with an instance, EC2 obtains temporary security credentials for the role you associated with the […]
Granting Users Permission to Work in the Amazon EC2 Console
This week, Kati Paizee, a technical writer on the Amazon EC2 team, takes an in-depth look at the permissions you need to give your users so that they can administer EC2 using the console. The Amazon EC2 console provides an easy-to-use interface that allows your users to carry out compute-based tasks without asking them to […]
Demystifying EC2 Resource-Level Permissions
Note: As of March 28, 2017, Amazon EC2 supports tagging on creation, enforced tag usage, AWS Identity and Access Management (IAM) resource-level permissions, and enforced volume encryption. See New – Tag EC2 Instances & EBS Volumes on Creation on the AWS Blog for more information. AWS announced initial support for Amazon EC2 resource-level permissions in July of […]
Analyzing OS-Related Security Events on EC2 with SplunkStorm
September 3, 2021: This blog post was updated to clarify that the S3 bucket name DOC-EXAMPLE-BUCKET is a placeholder name that readers should replace with their own S3 bucket name. An important objective of analyzing OS-generated data is to detect, correlate, and report on potential security events. Several partner solutions available in AWS Marketplace provide this functionality, […]