AWS Public Sector Blog
Secure your cloud journey with Tenable Cloud Security: Now FedRAMP authorized
The rapid adoption of cloud computing has brought unprecedented agility and scalability to organizations across all sectors. However, this transformative journey also introduces significant security complexities. Customers often face the challenge of managing a sprawling array of cloud resources, ensuring consistent security policies, and adhering to stringent compliance mandates. For organizations operating within or serving the U.S. Federal Government, or those adhering to similar rigorous standards, the need for robust and compliant cloud security solutions is paramount.
That’s why we’re excited to announce a significant milestone in our commitment to securing your cloud environments with a new Federal Risk and Authorization Management Program (FedRAMP) authorization at the Moderate impact level for Tenable Cloud Security—hosted on AWS GovCloud (US). This achievement extends from the existing FedRAMP authorized service of Tenable Government Solutions (also known as Tenable One). Both authorizations underscores Tenable’s dedication to providing best-in-class cloud security for even the most demanding cloud environments.
Understanding Tenable Cloud Security: A holistic approach to cloud protection
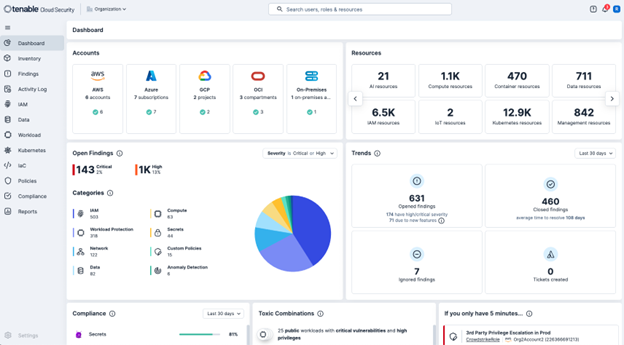
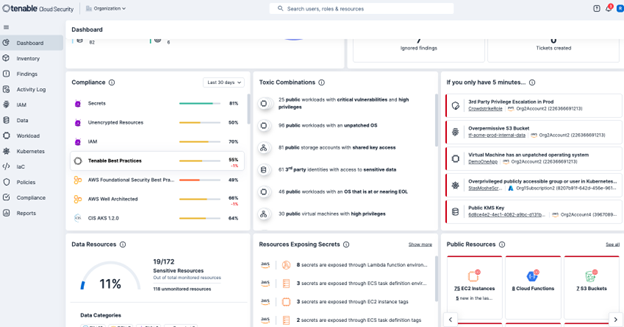
Tenable Cloud Security isn’t merely another security tool for AWS environments. It is a unified platform built to provide end-to-end protection for your cloud-based applications and infrastructure. The following screenshot shows the Tenable Cloud Security Dashboard.
As a comprehensive cloud-native application protection platform (CNAPP) available to customers, it integrates several critical security capabilities into a single, powerful solution:
- Cloud Security Posture Management (CSPM)
- Cloud Infrastructure Entitlement Management (CIEM)
- Cloud Workload Protection (CWP)
- Kubernetes Security Posture Management (KSPM)
- Infrastructure as Code (IaC) Security
- Just-In-Time Access (JIT)
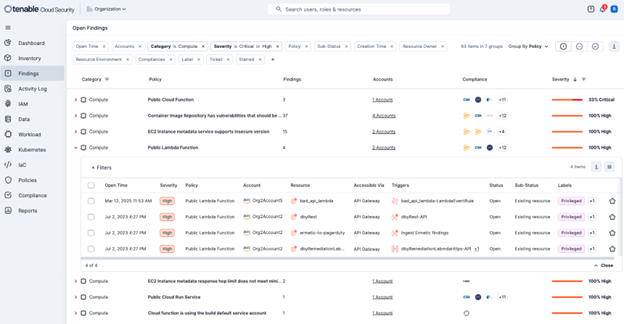
With Cloud Security Posture Management (CSPM), customers gain continuous visibility into their cloud configurations. Tenable Cloud Security proactively identifies misconfigurations, policy violations, and compliance drifts—so that your infrastructure adheres to security best practices and FedRAMP requirements. This includes real-time monitoring and automated assessments to prevent and detect configuration weaknesses that could be exploited.
Effectively manage the complex web of identities and permissions within your AWS environment with Cloud Infrastructure Entitlement Management (CIEM). Tenable CIEM provides granular visibility into who has access to what AWS resources, which means you can identify and remediate excessive or risky permissions. This “identity-first” approach is crucial for minimizing the attack surface and preventing lateral movement from elevated permissions, insider threats, or compromised accounts from causing significant damage. For FedRAMP environments, this promotes adherence to the principle of least privilege. The following screenshot shows the CIEM page.
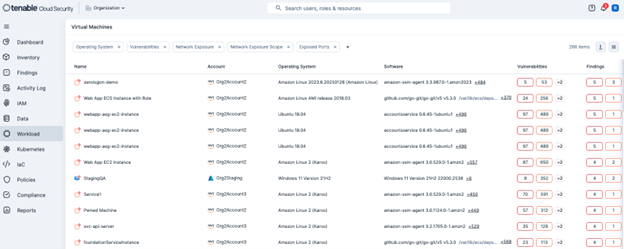
Secure your cloud workloads, including containers, serverless functions, and virtual machines using Tenable’s Cloud Workload Protection (CWP). Tenable’s CWP offers runtime protection, vulnerability management, and threat detection capabilities to safeguard your applications and data in real-time. This means that even if a misconfiguration or vulnerability exists, active threats can be identified and mitigated within your environment. The following screenshot shows the Tenable Cloud Security Virtual Machines inventory page.
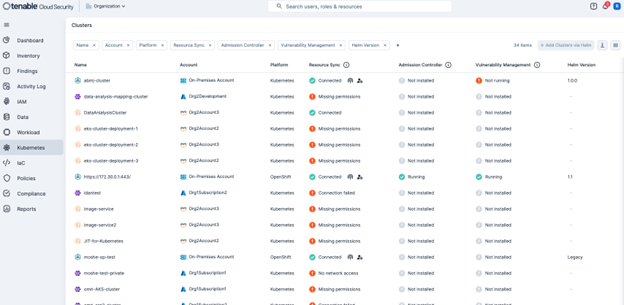
Kubernetes Security Posture Management (KSPM) is specifically designed to address the unique security challenges of Amazon Elastic Kubernetes Service (Amazon EKS) and other Kubernetes environments. Tenable’s KSPM, shown in the following screenshot, provides visibility into your Kubernetes clusters, identifies misconfigurations, and helps enforce security best practices for this increasingly popular orchestration platform. This is vital for customers using containerization in their cloud deployments.
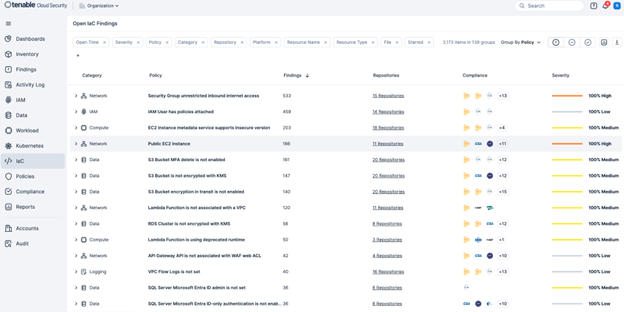
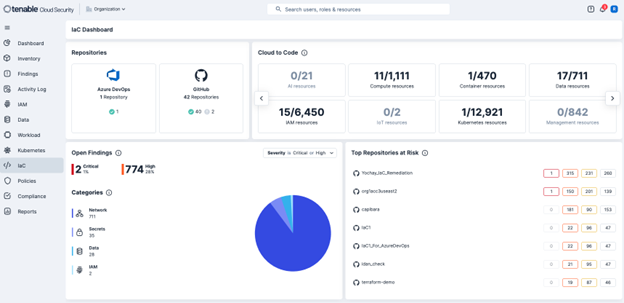
Prioritize security by analyzing your Infrastructure as Code (IaC) templates (such as Terraform and AWS CloudFormation) before resources are provisioned. Tenable’s IaC Security identifies potential security issues and compliance violations early in the development lifecycle, preventing misconfigurations from ever reaching your production environment. This proactive approach significantly reduces risk and saves valuable time and resources. The following screenshot shows the Open IaC Findings page.
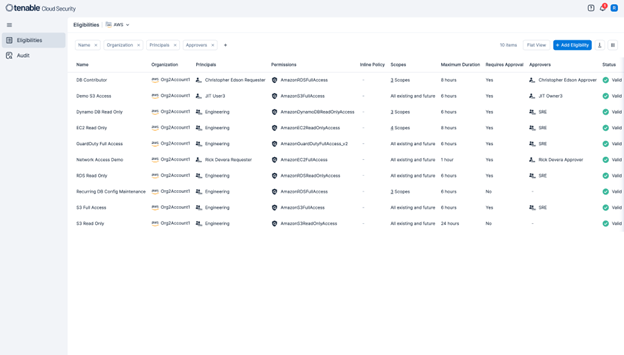
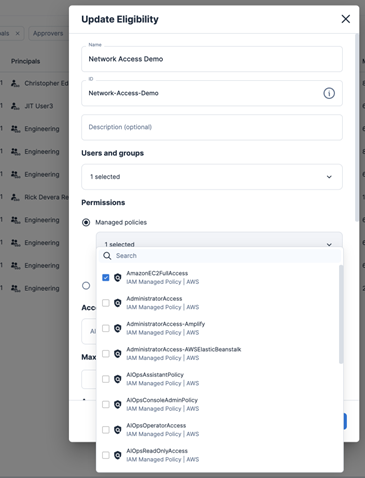
JIT access minimizes the window of opportunity for attackers by granting temporary elevated permissions only when and for as long as they’re necessary. By fully integrating with identity providers (IdP), including AWS IAM Identity Center, this capability dynamically enforces the principle of least privilege. It automatically revokes access when a designated task is complete, significantly reducing the risk of unauthorized access and privilege escalation within your cloud environment. The following screenshot shows the Eligibilities page.
The power of FedRAMP authorization
Achieving FedRAMP authorizations for Tenable Cloud Security and Tenable One signifies a commitment to meeting the stringent security and compliance requirements of the U.S. Federal Government. These authorizations provide Tenable’s customers, particularly government agencies and organizations working with the government, with the confidence that their cloud offerings have undergone rigorous testing and validation by third-party assessment organizations (3PAOs) and the FedRAMP Program Management Office (PMO). This achievement demonstrates Tenable’s ability to protect sensitive government data and adhere to the highest security standards.
Tenable One: Comprehensive exposure management platform
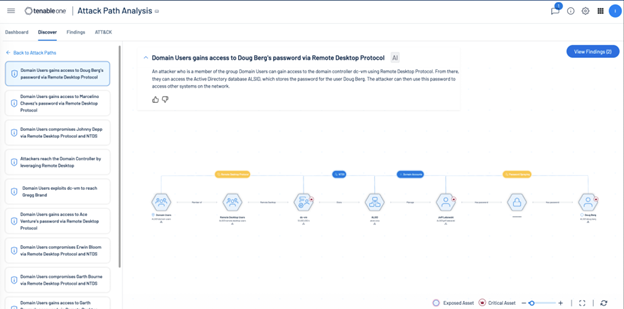
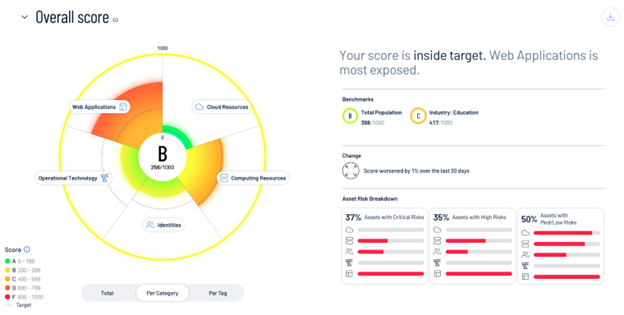
This solution helps Tenable’s customers manage and reduce cyber risk across their entire attack surface. It unifies vulnerability management, cloud security, identity security, and other crucial security functions into a single platform. By providing a holistic view of an organization’s security posture, Tenable One enables better risk prioritization, faster remediation, and improved overall security effectiveness. This allows security teams to focus on the most critical threats within their environments and efficiently manage their resources to minimize potential damage from cyberattacks. The following screenshots show the Tenable One Attack Path Analysis page and the Tenable One Overall score page.
Key features and benefits
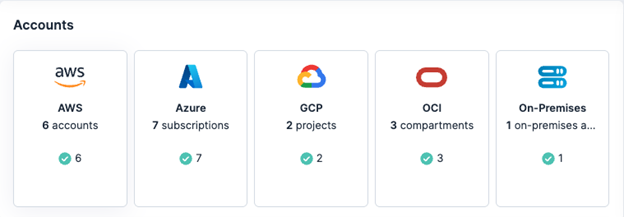
Tenable Cloud Security provides a unified view of your security posture across all your connected cloud environments, with specialized support for AWS services. This centralized visibility, shown in the following screenshot, eliminates blind spots and allows for consistent policy enforcement and risk management—crucial for complex cloud deployments and maintaining FedRAMP compliance across all assets.
Through intelligent risk analysis and prioritization, Tenable’s platform goes beyond merely identifying vulnerabilities and misconfigurations. Tenable Cloud Security correlates these findings with identity and access risks, surfacing “toxic combinations” that represent the most critical threats. This intelligent prioritization helps security teams focus their efforts on the issues that pose the greatest risk to their organization and its data, a key requirement for efficient security operations in FedRAMP environments. The following screenshot shows the Tenable Cloud Security Cloud Security Posture Management dashboard.
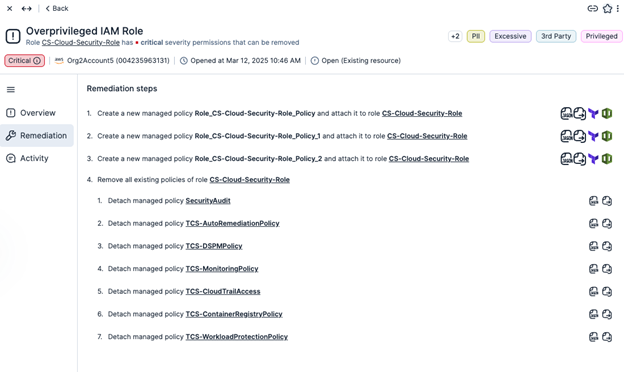
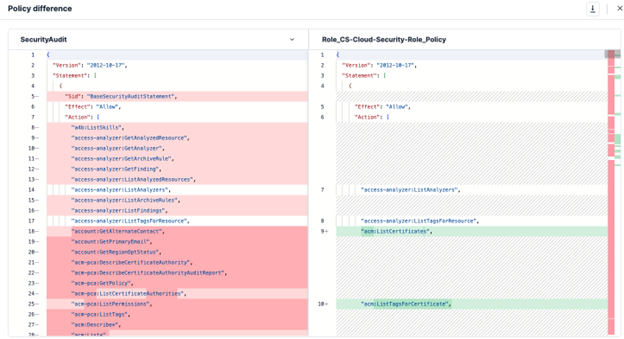
Tenable Cloud Security offers robust automation capabilities to streamline remediation efforts. From automatically applying security policies to generating remediation scripts, our platform helps security teams respond to threats and misconfigurations quickly and efficiently, reducing the window of exposure and improving overall security posture, a significant benefit for resource-constrained government agencies. The following figures show the Tenable Cloud Security automated remediation workflow.
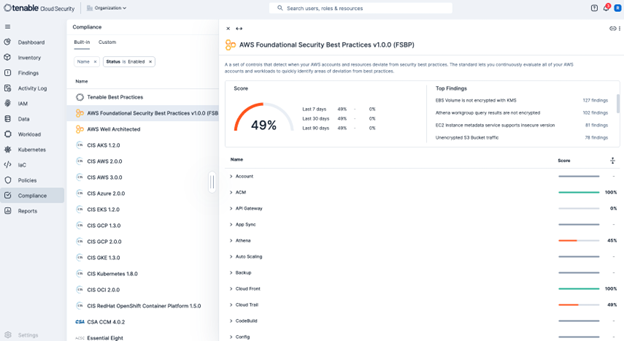
Maintaining compliance with frameworks such as FedRAMP, National Institute of Standards and Technology (NIST), AWS System and Organization Controls (SOC) 2, and Health Insurance Portability and Accountability Act (HIPAA) is simplified with Tenable Cloud Security. The platform continuously monitors your cloud environment against these standards, providing detailed reports and alerts on any deviations. This helps organizations demonstrate compliance and avoid costly penalties. The FedRAMP authorization specifically validates your ability to meet the rigorous security controls mandated by the U.S. Federal Government. The following screenshot shows the Tenable Cloud Security compliance management dashboard.
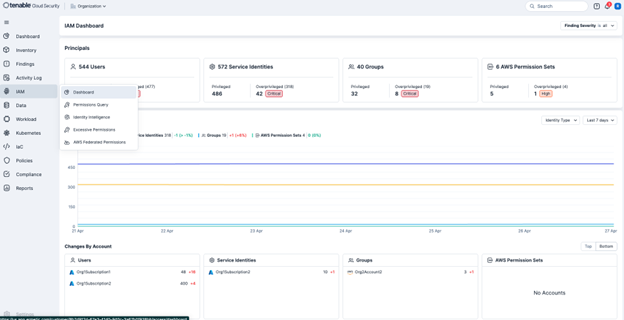
Recognizing that identities are the new perimeter, Tenable Cloud Security places a strong emphasis on managing cloud identities and entitlements. By providing granular visibility into user, role, and resource permissions, Tenable on AWS empowers organizations to enforce the principle of least privilege and prevent unauthorized access to sensitive data and resources, a cornerstone of FedRAMP security controls. The following screenshot shows the IAM Dashboard.
Recognizing that identities are the new perimeter, Tenable Cloud Security places a strong emphasis on managing cloud identities and entitlements. By providing granular visibility into user, role, and resource permissions, Tenable on AWS empowers organizations to enforce the principle of least privilege and prevent unauthorized access to sensitive data and resources, a cornerstone of FedRAMP security controls. The following screenshot shows the IAM Dashboard.
By integrating security into the early stages of the development lifecycle through IaC scanning, Tenable Cloud Security helps prevent security issues from reaching production. This proactive approach reduces the cost and complexity of remediation and fosters a more secure development pipeline, aligning with best practices for secure software development in any environment, including those requiring FedRAMP compliance. The following screenshot shows the IaC Dashboard.
How Tenable Cloud Security works: Continuous protection in action
Tenable Cloud Security operates through a continuous cycle of discovery, analysis, and remediation:
- Asset discovery – The platform automatically discovers and inventories all your cloud assets across connected environments on AWS and other cloud service providers, providing a comprehensive understanding of your cloud footprint.
- Continuous risk analysis – Tenable Cloud Security continuously monitors your cloud configurations, workloads, and identities for vulnerabilities, misconfigurations, compliance violations, and excessive permissions. This analysis is informed by Tenable’s industry-leading vulnerability intelligence and sophisticated risk scoring algorithms.
- Intelligent prioritization – By correlating various security findings, the platform prioritizes risks based on their potential impact and likelihood of exploitation, allowing security teams to focus on the most critical issues.
- Automated remediation guidance and actions – Tenable Cloud Security provides clear remediation guidance and, in many cases, offers automated remediation actions to quickly address identified risks and misconfigurations. This automation is crucial for maintaining a strong security posture and meeting the rapid pace of cloud deployments.
- Identity-first approach in practice – Tenable Cloud Security integrates with your existing identity providers (such as Okta or Ping) to gain visibility into all cloud identities and their associated permissions. This allows for continuous monitoring of identity-related risks and the enforcement of least privilege policies.
- Seamless cloud provider integration – Tenable Cloud Security is designed to seamlessly integrate with major cloud platforms, using native APIs for comprehensive data collection and action execution. This enables accurate and up-to-date visibility without adding unnecessary complexity to your cloud environment.
Real-world impact: Securing your cloud success stories
Organizations across various industries, including those with stringent regulatory requirements, are using Tenable Cloud Security to significantly enhance their cloud security posture. For example:
- A large government contractor used Tenable Cloud Security to gain comprehensive visibility into their multi-cloud environment, identify and remediate critical misconfigurations, and automate compliance checks against NIST 800-53 controls, a key component of FedRAMP. This resulted in a significant reduction in their attack surface and improved audit readiness.
- A financial services company used Tenable CIEM to identify and revoke excessive permissions, reducing their risk of data breaches and ensuring compliance with regulations such as General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA).
- A software development firm integrated Tenable IaC Security into their continuous integration and continuous delivery (CI/CD) pipeline, preventing misconfigurations from being deployed into their production environment, which saved them time and resources while improving the overall security of their applications.
With the recent FedRAMP authorization, U.S. federal agencies and organizations working with them can now confidently use Tenable Cloud Security to meet their stringent security and compliance needs, knowing that the platform has been rigorously vetted and approved for use in their environments.
Conclusion
For modern enterprises, security is not an option—it’s a fundamental requirement. Tenable Cloud Security offers customers a comprehensive and integrated platform to address the evolving challenges of cloud security, providing the visibility, risk insights, and automated remediation capabilities needed to protect critical assets in AWS environments.
With the significant achievement of FedRAMP authorization, Tenable Cloud Security stands ready to empower U.S. federal agencies and customers operating under similar high-security standards to embrace the cloud with confidence and achieve their mission-critical objectives securely.
Ready to take control of your cloud security posture with a FedRAMP authorized solution? Tenable Cloud Security and Tenable One are available for procurement in AWS Marketplace.
Visit Tenable’s website to learn more about Tenable Cloud Security and Tenable One, request a demo, or connect with your AWS team to put you in touch with Tenable’s cloud security experts. Secure your cloud journey with Tenable Cloud Security today.