Networking & Content Delivery
Streamlining RISE with SAP Connectivity using AWS Cloud WAN
Under RISE with SAP, establishing network connectivity to the RISE with SAP Amazon Virtual Private Cloud (Amazon VPC) on Amazon Web Services (AWS) is your responsibility. Traditionally, users have relied on AWS Site-to-Site VPN, AWS Direct Connect, Amazon VPC peering, or AWS Transit Gateway to connect their on-premises networks and existing AWS accounts to the SAP-managed environment. Furthermore, organizations already using AWS Cloud WAN to build, manage, and monitor their unified global network may prefer to align their RISE with SAP connectivity with their existing Cloud WAN architecture. With Cloud WAN, you can get a unified global network with consistent policy-based control enabling you to streamline management, enhance security through traffic inspection, and maintain a cohesive networking strategy across your organization.
Cloud WAN is one of the options for network connectivity for RISE with SAP that is available upon users’ request to the RISE with SAP team. Moreover, the connectivity patterns discussed in this post can also be followed with any other third-party integration following the same architecture as RISE with SAP.
Why AWS Cloud WAN?
AWS Cloud WAN is a managed wide area networking (WAN) service that enables you to build, manage, and monitor a global network that connects resources running across your cloud and on-premises environments. It provides a unified, centrally managed network, which reduces the operational cost and complexity involved with running a global network.
Although AWS offers many powerful networking connectivity services, Cloud WAN takes network management to the next level by providing a global view and consistent policy-based control across your entire network. You can get more information about the service in the posts Introducing AWS Cloud WAN (where you can understand better the key components of the service), and Simplify global security inspection with AWS Cloud WAN service insertion (to understand how Cloud WAN streamlines traffic inspection configuration).
However, the main question you may be asking yourself is: what’s the benefit of using Cloud WAN over other connectivity methods?
- Cloud WAN provides a global (multi-Region) dynamic network within AWS. This means that natively any VPC in any of your AWS Regions automatically have access to RISE with SAP in a dynamic way, regardless of the Region where the environment has been created.
- The centralized management and view streamlines the understanding of complex networks and how they interconnect to your third-party connections.
- Transit Gateway enables you to define your own routing, propagations, and how attachments map to route tables. Adding a new route table or attachment often results in a dozen or more downstream changes. Cloud WAN allows you to use attachment tags and other metadata to automatically map attachments to segments, where you define relationships between segments through policy.
- When connecting to third-party solutions through VPC attachments, we encourage you to include traffic inspection between your environment and the third-party ones. The Cloud WAN service insertion capability streamlines the configuration of the routing to create this inspection.
Architecture and deployment steps for RISE with SAP on AWS Cloud WAN
Now that we have defined AWS Cloud WAN and its benefits, we can focus on the integration with RISE with SAP. Figure 1 shows the architecture for connecting RISE with SAP using Cloud WAN in a multi-account environment. We have included an inspection layer using AWS Network Firewall to inspect traffic between the RISE with SAP VPC and the rest of the environment. This pattern also works when using any other third-party firewall appliance with Gateway Load Balancer (GWLB).
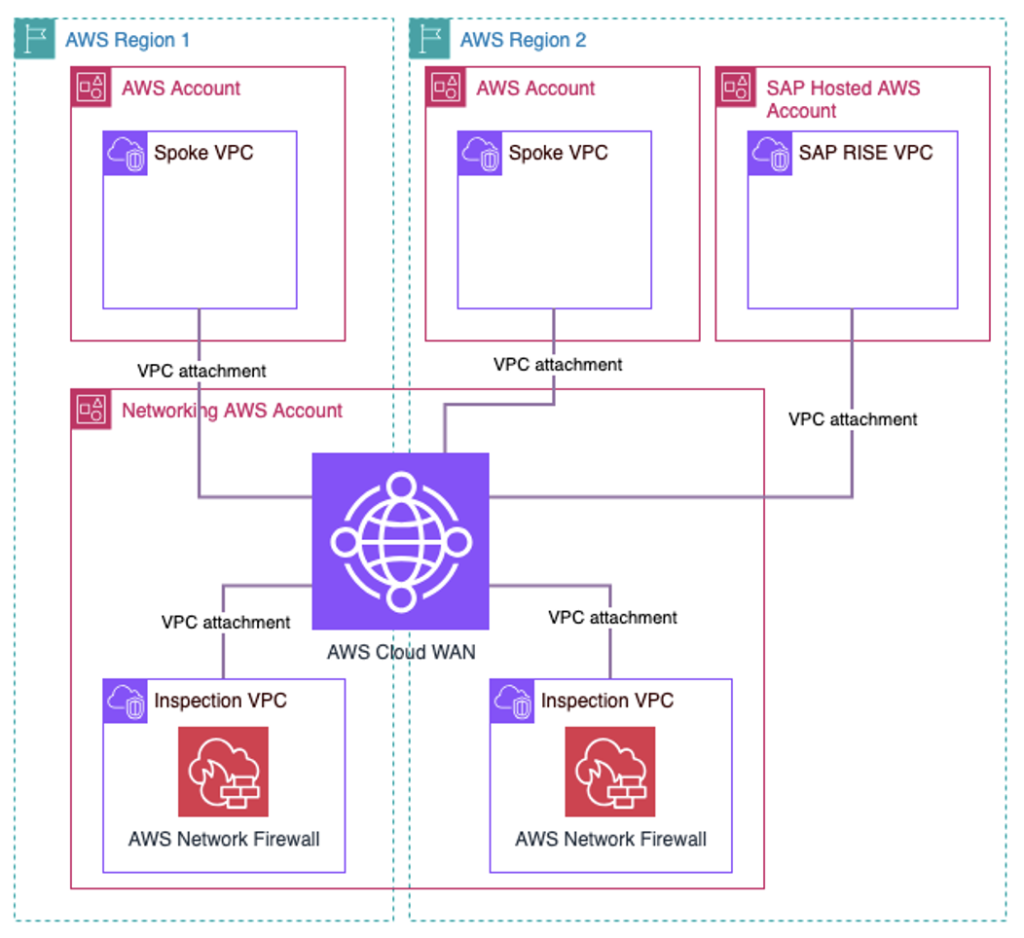
Figure 1. Multi-Region and multi-account AWS Cloud WAN high-level architecture connecting to RISE with SAP
The following steps outline the integration for your AWS network (using Cloud WAN) with RISE with SAP. In this section we focus on defining the configuration steps of the integration.
- You should have created a Global Network and Core Network with a policy document defining your network structure: AWS Regions, segments, routing actions, and attachment policies. Check the AWS documentation for more information about this setup. We recommend using a dedicated segment for RISE with SAP VPC connections. The minimal segmentation configuration in Cloud WAN—having VPCs connected to a dedicated segment—allows for better control over routing configuration (adding inspection, creating static routes or blackholes, etc.).
- To follow the best practice of including an inspection layer, you should deploy an Inspection VPC with either Network Firewall or GWLB with third-party appliances. In addition, your policy document should insert this firewall between your workload and RISE with SAP VPCs.
- Share the Core Network with the RISE with SAP account using AWS Resource Access Manager (AWS RAM). Check the documentation to understand how you can share resources using AWS RAM. The Core Network is a global resource, thus the sharing must be done from the N. Virginia (us-east-1) Region.
- Work with the RISE with SAP team to accept the shared Core Network invitation. The RISE with SAP team needs to perform the following actions:
- Accept the shared Core Network invitation.
- Configure their VPC attachments to connect to the shared Core Network.
- Add necessary private network routes in the subnet route table for seamless bi-directional communication.
This setup allows for secure network sharing and connectivity between the user’s AWS account and the RISE with SAP environment. Considerations include avoiding overlapping CIDR blocks, monitoring data transfer costs, regularly auditing firewall rules, and using AWS CloudTrail for auditing purposes.
Best practices when implementing AWS Cloud WAN for RISE with SAP
In this section we focus on the best practices when integrating RISE with SAP with your network based on AWS Cloud WAN. We do this both from the policy document configuration and the firewall rules to be implemented.
We can examine a complete policy document that is implemented in accordance with the architecture shown in Figure 2. We use this example to highlight key best practices and important sections of the policy document.
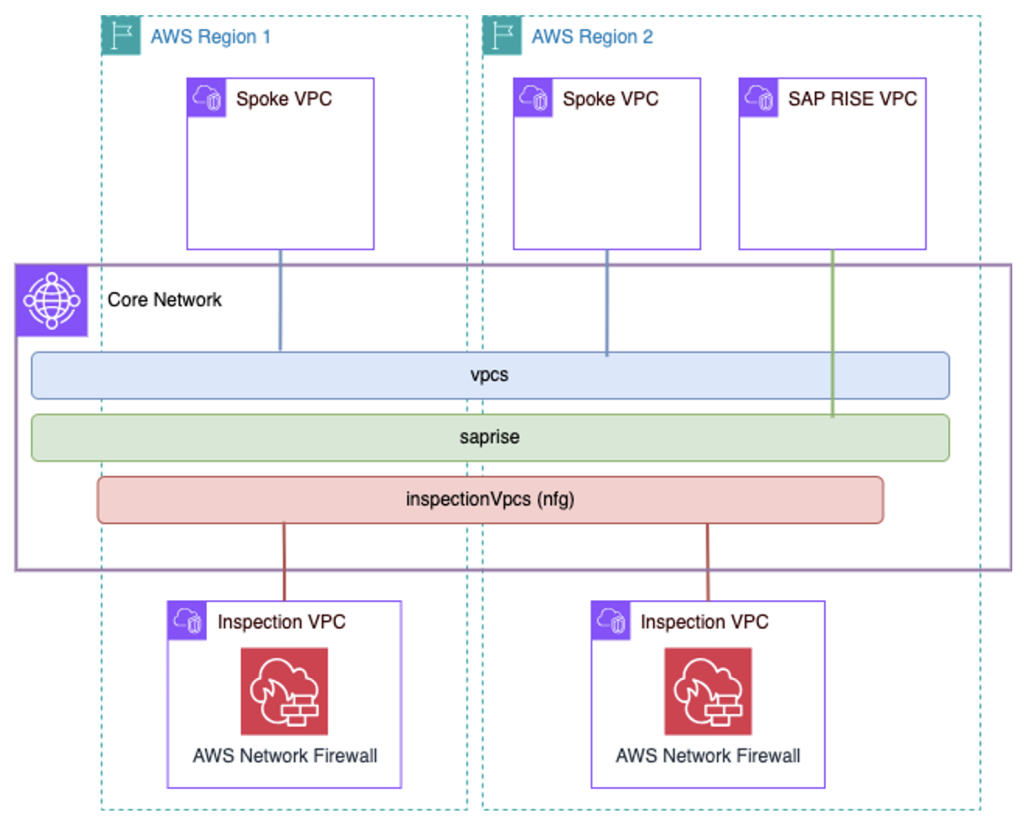
Figure 2. AWS Cloud WAN example architecture with an inspection layer between AWS workloads and RISE with SAP
{
"version": "2021.12",
"core-network-configuration": {
"vpn-ecmp-support": true,
"asn-ranges": [
"64496-64500"
],
"edge-locations": [
{
"location": "us-east-1",
"asn": 64496
},
{
"location": "eu-central-1",
"asn": 64497
}
]
},
"segments": [
{
"name": "vpcs",
"require-attachment-acceptance": false
},
{
"name": "saprise",
"require-attachment-acceptance": true,
"isolate-attachments": true
}
],
"network-function-groups": [
{
"name": "inspectionVpcs",
"require-attachment-acceptance": true
}
],
"segment-actions": [
{
"action": "send-via",
"segment": "vpcs",
"mode": "dual-hop",
"when-sent-to": {
"segments": [
"saprise"
]
},
"via": {
"network-function-groups": [
"inspectionVpcs"
]
}
}
],
"attachment-policies": [
{
"rule-number": 100,
"condition-logic": "and",
"conditions": [
{
"type": "attachment-type",
"operator": "equals",
"value": "vpc"
},
{
"type": "tag-exists",
"key": "domain"
}
],
"action": {
"association-method": "tag",
"tag-value-of-key": "domain"
}
},
{
"rule-number": 200,
"condition-logic": "and",
"conditions": [
{
"type": "attachment-type",
"operator": "equals",
"value": "vpc"
},
{
"type": "account-id",
"operator": "equals",
"value": "XXXXXXXXXXXX"
}
],
"action": {
"association-method": "constant",
"segment": "saprise"
}
},
{
"rule-number": 300,
"condition-logic": "and",
"conditions": [
{
"type": "tag-value",
"operator": "equals",
"key": "nfg",
"value": "inspectionVpcs"
}
],
"action": {
"add-to-network-function-group": "inspectionVpcs"
}
}
]
}In the following steps we break down the key components and best practices:
- Network segment definition: We recommend using a dedicated segment for RISE with SAP VPCs. This approach allows you to maintain separate routing control for these VPCs and the rest of your environment. In the case of the “saprise” segment, we configure the isolate-attachments option so that attachments within that segment cannot communicate with each other by default.
"segments": [
{
"name": "vpcs",
"require-attachment-acceptance": false
},
{
"name": "saprise",
"require-attachment-acceptance": true,
"isolate-attachments": true
}
],- Traffic inspection and the Cloud WAN service insertion: After setting up your network segments, consider the following recommendations to enhance your Cloud WAN configuration for RISE with SAP:
- Implement the firewall layer to protect traffic between RISE with SAP VPCs and your other Cloud WAN-connected workloads. To achieve this, create a Network Function Group (NFG) to use the service insertion functionality.
"network-function-groups": [
{
"name": "inspectionVpcs",
"require-attachment-acceptance": true
}
],-
- The service insertion routing action to inspect traffic between segments is called send-via. In our example, the dual-hop option inspects cross-Region traffic in the two Regions that the traffic is traversing. Another option is using the single-hop option to only inspect in one of them (you can also choose which AWS Region is used). Go to the AWS documentation to learn more about how it works.
"segment-actions": [
{
"action": "send-via",
"segment": "vpcs",
"mode": "dual-hop",
"when-sent-to": {
"segments": [
"saprise"
]
},
"via": {
"network-function-groups": [
"inspectionVpcs"
]
}
}
],- Configure attachment policies: New attachments in Cloud WAN are automatically associated to a segment or NFG by using attachment-policies in the policy document. From the attachments you can obtain metadata (tags, attachment type, AWS account, or AWS Region) to define granular policies and indicate how a new attachment should be associated to a segment in the network. We can focus on the rule number 200 as an example to dive deep in this capability.
- For the case of RISE with SAP VPCs, the recommendation is to use the SAP Account ID as metadata to automate the attachment association. In the following code, you should replace the “XXXXXXXXXXXX” placeholder with the Account ID.
- Furthermore, use the require acceptance flag to add an extra manual control when creating the association.
{
"rule-number": 200,
"condition-logic": "and",
"conditions": [
{
"type": "attachment-type",
"operator": "equals",
"value": "vpc"
},
{
"type": "account-id",
"operator": "equals",
"value": "XXXXXXXXXXXX"
}
],
"action": {
"association-method": "constant",
"segment": "saprise"
}
}
Other considerations
- When configuring the firewall rules, consider the RISE with SAP-specific ports to allow communication from your workloads to the RISE with SAP VPC. For more details around which firewalls you can implement, refer to the Securing SAP with AWS Network Firewall part-2 managed rules post.
- RFC Connections (BAPI and IDoc): Ports 33xx (where xx is your instance number)
- HTTPS for OData and REST/SOAP: Ports 443, 44300
- ODBC/JDBC for SAP HANA connections: Ports 3xx15 (where xx is your instance number)
- Some more necessary ports:
- 44301-44302: Client and SAP AS connections
- 3201-3202: Client and SAP AS connections
- 8001-8002: Client and SAP AS connections
- 3600: If using load balancing with message server
- 3299: SAProuter service
- 3200-3299: SAP Connector
- 3300-3399: SAPGUI
- Use AWS Network Manager to monitor and manage your Core Network:
- Set up alerts for network issues and policy violations
- Configure dashboards for network visibility
- Enable logging for troubleshooting and compliance
- Implement regular maintenance procedures for:
- Periodic reviews of firewall rules
- Network policy updates
- Configuration changes as needed
Conclusion
AWS Cloud WAN provides a streamlined approach to connect your environments with RISE with SAP on AWS. A unified global network with consistent policy-based control enables you to streamline management, enhance security through traffic inspection, and maintain a cohesive networking strategy across your organization.
This setup allows for secure network sharing and connectivity between your AWS account and the RISE with SAP environment with your existing or new Cloud WAN setup.
To learn more about Cloud WAN and RISE with SAP connectivity options, visit the AWS Cloud WAN documentation and RISE with SAP on AWS documentation.


