Networking & Content Delivery
Introducing security group referencing and enhanced DNS support for AWS Cloud WAN
In this post we cover the recently launched feature of security group referencing and enhanced DNS support on AWS Cloud WAN. This new feature allows you to create inbound security rules referencing security groups defined in other Amazon Virtual Private Clouds (Amazon VPCs) attached to an AWS Cloud WAN within the same AWS Region and within a single AWS Cloud WAN Core Network Edge (CNE).
AWS Cloud WAN is designed to streamline global network management. It allows you to build, manage, and monitor a unified network that connects multiple VPCs and on-premises environments using a central policy-based automation system. AWS Cloud WAN allows you to create a global network that spans AWS Regions and streamlines routing, security, and connectivity configurations.
The new security group referencing capability allows for dynamic and scalable network security configurations. When defining security group ingress rules in a VPC attached to an AWS Cloud WAN core network, you can reference security groups defined in other VPCs within the same Region attached to the same core network, instead of hard-coding IPv4 and IPv6 address ranges. This enables rule management and supports architectures that scale across many VPCs without compromising security. This features in environments where resources are segmented by function or application but still need controlled access across boundaries. It enhances your ability to define granular network access controls while maintaining centralized visibility and management.
Another new feature we are launching is DNS support on AWS Cloud WAN, which enables the resolution of public DNS Amazon Elastic Compute Cloud (Amazon EC2) hostnames to private IP addresses when queried across VPCs attached to the same core network within the same Region.
How to use security group referencing with AWS Cloud WAN
For security group referencing to work, the feature must be enabled at the AWS Cloud WAN core network and VPC attachment levels. This two-step configuration process makes sure that you have fine-grained control over where and how security group referencing is applied.
You can enable the security group referencing support option when you create a new AWS Cloud WAN core network or by editing an existing one. Similarly, you can enable the security group referencing support option on a core network VPC attachment upon creation, or later by editing the VPC attachments. These operations can be done through the AWS Management Console, AWS Command Line Interface (AWS CLI), or AWS SDK. The security group referencing support option is enabled by default when creating new AWS Cloud WAN VPC attachments.
To enable this feature at the core network level, you must add a new statement to the core network policy, as we demonstrate in the next section. When you do that, the configuration is applied to all CNEs of that core network (and thus to all AWS Regions where that core network is configured).
Console and CLI examples
In this section, you will perform the necessary actions to enable security group cross-referencing.
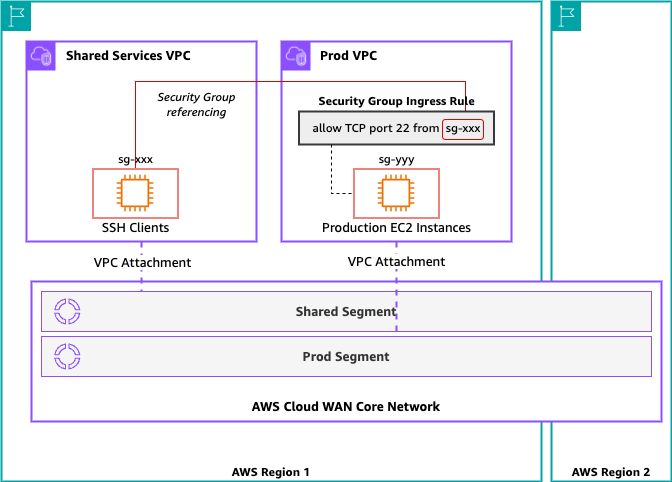
Consider the scenario shown in Figure 1. In this scenario, you have a requirement to enable several SSH Clients in the Shared Services VPC to SSH into EC2 instances in the Prod VPC. You have to allow this securely and without explicit reference to any CIDR range associated with any of the Shared Services VPC subnets. You must also assume that all the routing has been correctly configured to enable connectivity between the Shared Services and Prod VPCs.
1. Enabling security group referencing support and enhanced DNS support at the core network through the core network policy
You begin by modifying the existing network policy of the core network by adding the "security-group-referencing-support": true statement and applying the new version of the network policy. Optionally, you can enable EC2 DNS hostname resolution across VPC attachments by adding the "dns-support": true statement, as shown in the following JSON code snippet.
{
"version": "2021.12",
"core-network-configuration": {
"vpn-ecmp-support": false,
"dns-support": true, //new feature
"security-group-referencing-support": true, //new feature
"asn-ranges": [
"64512-65534"
],
"edge-locations": [
{
"location": "eu-west-1"
},
{
"location": "us-west-1"
}
]
},
[... OMITTED ...]If you prefer a more visual approach, then you can also use the console to edit the core network policy and enable the security group referencing support, as shown in Figure 2.

Figure 2. Enabling Security Group Referencing Support option at the Core Network level through the console
2. Enabling security group referencing support and enhanced DNS support through AWS CLI when adding a VPC attachment to the core network
You will now create a new core network VPC attachment for the Shared Services VPC. To do that, create a JSON file called attachment.json containing the arguments for the CLI command needed to create the VPC attachment to the Shared Services VPC. Resource IDs in the following sample need to be replaced with the IDs of the resources in your AWS account. The security group referencing support option is enabled by default when creating new attachments.
{
"CoreNetworkId": "core-network-0000000000000",
"VpcArn": "arn:aws:ec2:eu-west-1:123456789012:vpc/vpc-0000000000000", // shared-services VPC
"SubnetArns": [
"arn:aws:ec2:eu-west-1:123456789012:subnet/subnet-0000000000000",
"arn:aws:ec2:eu-west-1:123456789012:subnet/subnet-0000000000001",
"arn:aws:ec2:eu-west-1:123456789012:subnet/subnet-0000000000002"
],
"Options": {
"ApplianceModeSupport": false,
"Ipv6Support": true,
"SecurityGroupReferencingSupport": true //new feature, "true" by default
"DnsSupport": true //new feature
}
}Then, you create the attachment by issuing the following create-vpc-attachment CLI command:
aws networkmanager create-vpc-attachment --cli-input-json file://attachment.json
3. Enabling security group referencing support through the console when modifying an existing VPC attachment at the core network
You enable the security group referencing support option for the existing Prod VPC attachment by modifying the attachment through the console, as shown in Figure 3. Optionally, you can also enable EC2 DNS hostname resolution across VPC attachments by choosing DNS Support, as shown in Figure 3.

Figure 3: Enabling Security Group Referencing Support and DNS Support options at the VPC attachment level through the console
4. Referencing a security group from one VPC in a security group rule inside another VPC
In this section you can learn how use the security group referencing support option by cross referencing a security group across two VPCs attached to the same core network in the same AWS Region.
The first thing you must do is note the security group ID associated with the SSH client instances in the Shared Services VPC. In the example shown in Figure 4, the security group ID is sg-01754360f80836e07.
Then, add a new ingress rule to the security group associated with the Prod instances (sg-04462481c115ab4aa) that references the security group of the SSH client instances to allow SSH connectivity from that security group, as shown in Figure 5.

Figure 5: Adding an ingress rule to the Prod VPC security group referencing the security group of the SSH client instances
After adding the new inbound rule, you can successfully SSH to the Prod VPC instance from the Shared Services VPC instance.
[ec2-user@ip-172-16-0-10 ~]$ ssh ec2-user@10.1.0.10
, #_
~\_ ####_ Amazon Linux 2023
~~ \_#####\
~~ \###|
~~ \#/ ___ https://aws.amazon.com/linux/amazon-linux-2023
~~ V~' '->
~~~ /
~~._. _/
_/ _/
_/m/'
[ec2-user@ip-10-1-0-10 ~]$Use cases for security group referencing with AWS Cloud WAN
Some of the use cases for this new feature are the same as the security group referencing for AWS Transit Gateway in the post Introducing security group referencing for AWS Transit Gateway. They are listed here for convenience:
- Securely connect application tiers across multiple VPCs. For example, allow web servers in one VPC to communicate with database servers in another VPC without exposing specific IP addresses.
- Provide selective access to shared services such as Active Directory from isolated environments. This enables centralized communication while maintaining network segmentation and security boundaries.
- Enable cross-account access controls in shared VPC models. Organizations can implement fine-grained permissions for resources accessed by multiple AWS accounts within their AWS Cloud WAN infrastructure.
Considerations
- Make sure that the feature is enabled on both the core and attachment levels. This dual-layer configuration requirement provides granular control over security group referencing deployment.
- Routing between the VPCs where you reference the security groups to and from need to have the appropriate routing configured so that there is full reachability between all the sources and destinations of IP traffic.
- Review and clean up stale references when detaching or deleting VPCs or security groups using
describe-stale-security-groups. Regular checks prevent security rule conflicts and make sure of optimal performance. - This feature currently only supports intra-Region referencing within a single core network. Cross-Region security group references are not supported.
- Security groups can only be referenced in security group ingress rules.
- Security group referencing doesn’t work when the traffic is inspected through the native AWS Network Firewall or third-party network appliances.
Conclusion
In this post, we showed how to enable and disable security group referencing across AWS Cloud WAN and the benefits of this feature in some use cases.
The introduction of security group referencing support in AWS Cloud WAN allows users to streamline security rule management by referencing security groups across VPCs attached to the same CNE instead of relying on static IP addresses or ranges. This aligns the AWS Cloud WAN capabilities with those already available in AWS Transit Gateway, addressing a key user need—especially for large enterprises migrating from Transit Gateway to AWS Cloud WAN. Although this functionality is limited to the same AWS Region (CNE), it significantly reduces operational complexity and promotes centralized, dynamic security policy enforcement. This enhancement supports users in building more secure multi-VPC architectures using AWS Cloud WAN.
This capability is available in all AWS Regions where AWS Cloud WAN is available. To learn more about AWS Cloud WAN, refer to the AWS Cloud WAN documentation. Thank you for reading this post. If you have questions about this post, then start a new thread on AWS re:Post or contact AWS Support.