Networking & Content Delivery
Amazon VPC Lattice support for RDS Multi-AZ
In this post we review how Amazon VPC Lattice can provide simple and secure access to an Amazon RDS Multi-AZ deployment using Amazon Resource Names (ARNs).
Prerequisites
We assume you are familiar with Amazon Virtual Private Cloud (VPC), and VPC Lattice concepts and capabilities. If you are unfamiliar with VPC Lattice please review Amazon VPC Lattice: modernize and simplify your enterprise network architectures before starting.
Amazon RDS Multi-AZ cluster resource
We have provisioned a Multi-AZ MySQL database cluster in a VPC called “rds-vpc”. In this hypothetical use case we want to provide access to the Multi-AZ MySQL database from a pods running on Amazon Elastic Kubernetes Service (Amazon EKS) in the “eks-cluster-vpc” VPC. Amazon RDS, and EKS configuration information can be found at Multi-AZ DB cluster deployments for Amazon RDS, and Create an Amazon EKS cluster.
We will be use an existing “dev” service network,
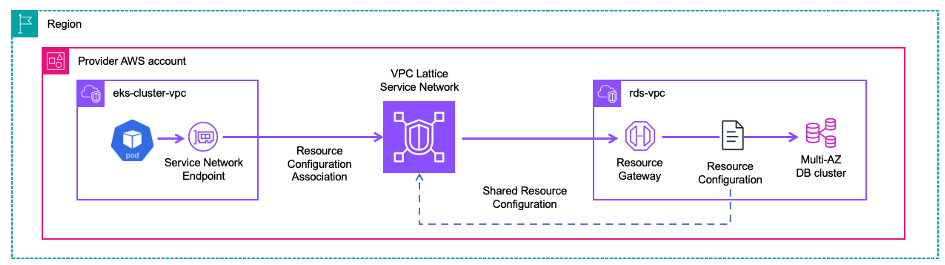
Figure 1 shows a high-level architecture
Figure 1: Use case: RDS Multi-AZ cluster resource
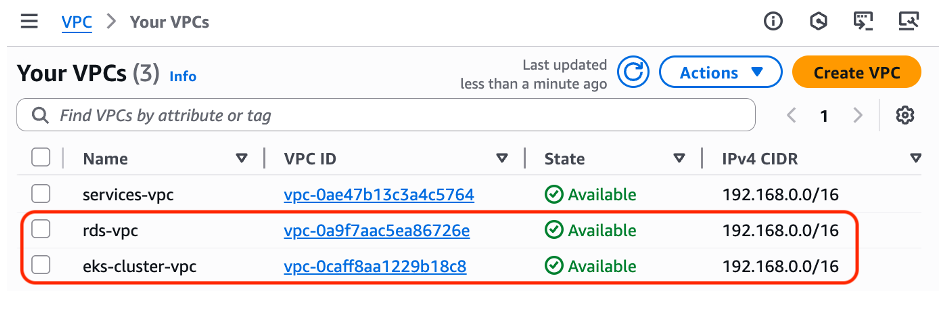
Figure 2 shows the VPCs
Figure 2: “rds-vpc” and “eks-cluster-vpc” VPCs
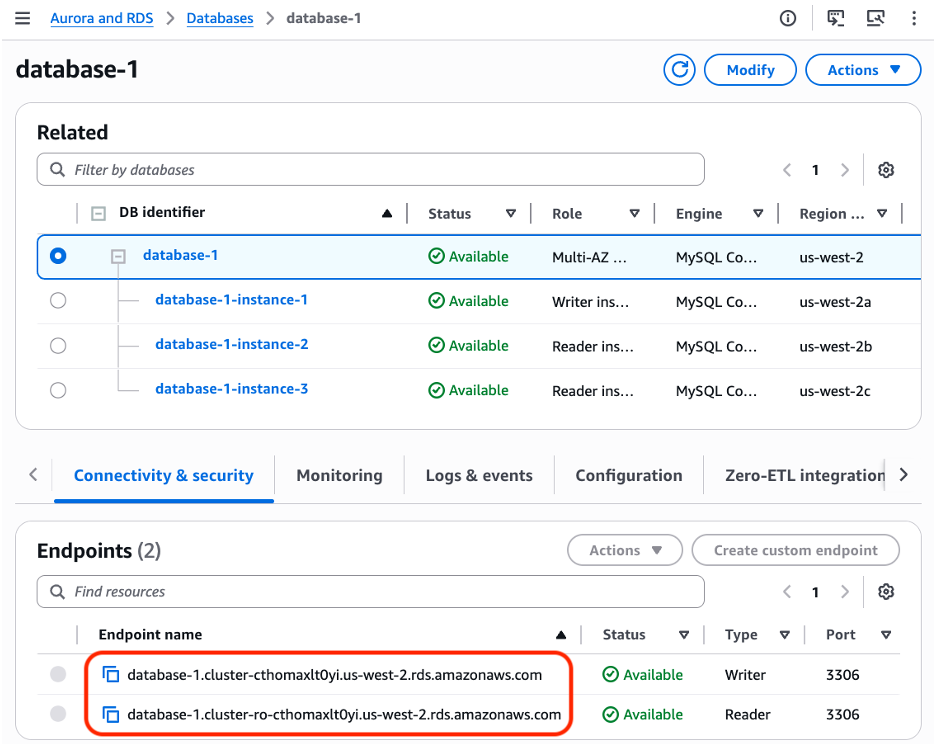
Figure 3 displays the Amazon RDS nodes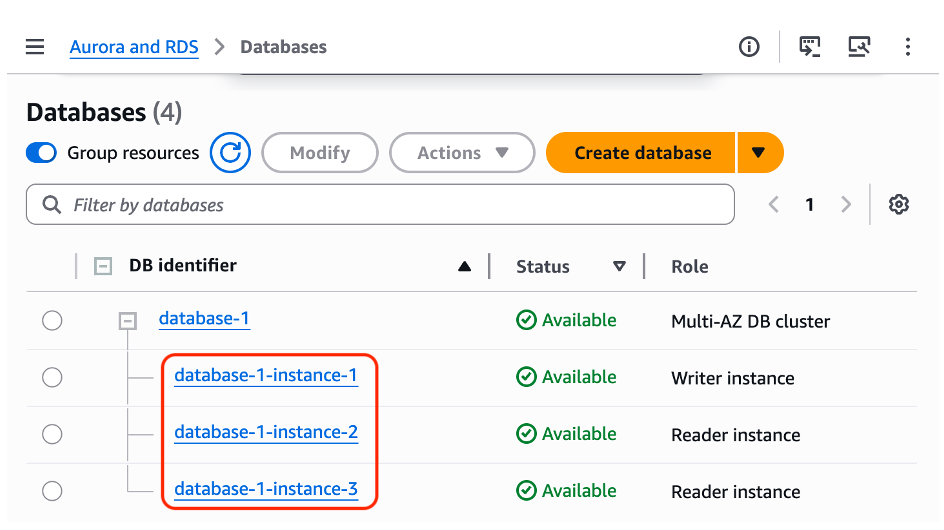
Figure 3: Amazon RDS console showing Amazon RDS MySQL Multi-AZ cluster
These are the step we will follow to provision VPC Lattice:
1. Create Resource Gateway for “rds-vpc” VPC
2. Create Resource group configuration assigned to Resource Gateway
3. Add Resource configuration to Service network
4. Create an endpoint in the “eks-cluster-vpc” VPC
5. DNS validation
6. Connect to Amazon RDS cluster over VPC Lattice from test Pod
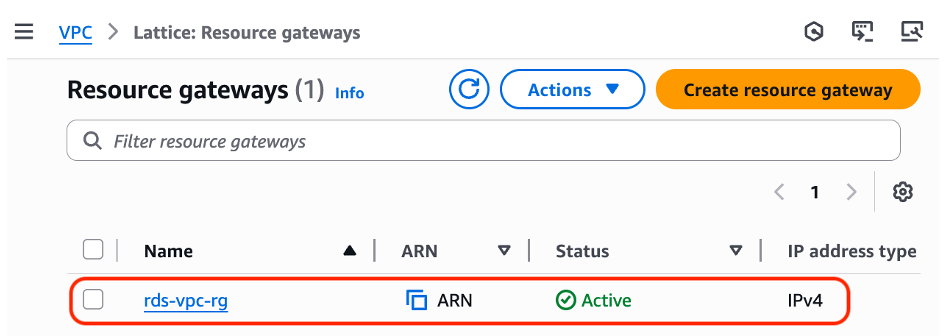
Step 1: Create Resource Gateway for “rds-vpc” VPC
- Open the Amazon VPC console.
- In the navigation pane under PrivateLink and Lattice choose Resource gateways.
- Choose Create resource gateway.
- Provide Resource gateway name.
- Choose IP address type [IPv4/IPv6/Dualstack].
- Choose VPC.
- Choose Availability Zones and Subnets.
- Choose Security groups.
- Choose Create resource gateway.
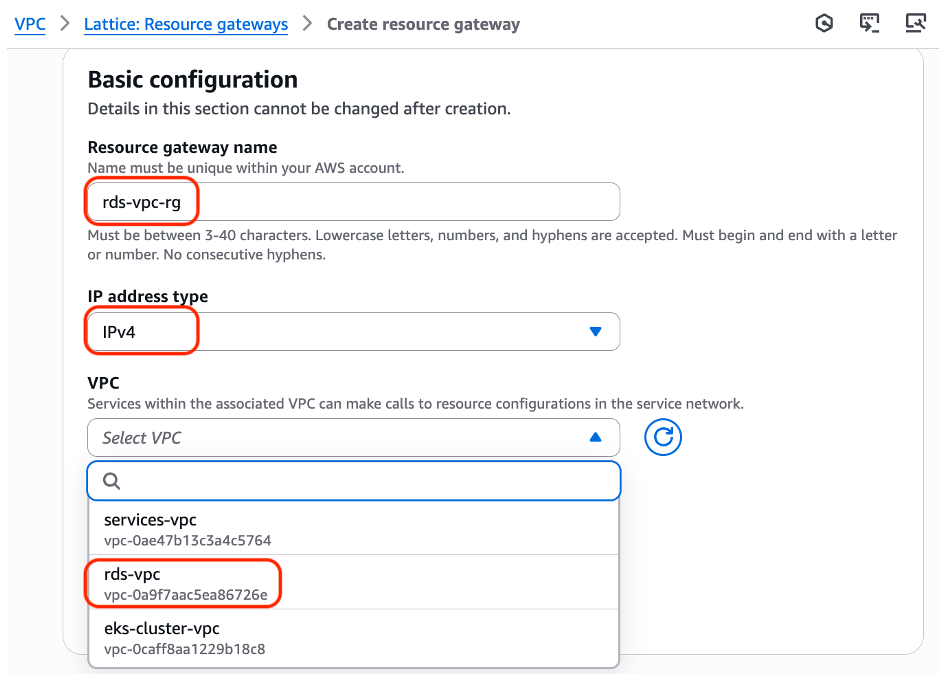
Figure 4: Create a new Resource Gateway in the “rds-vpc”
Figure 5: Created the Resource Gateway
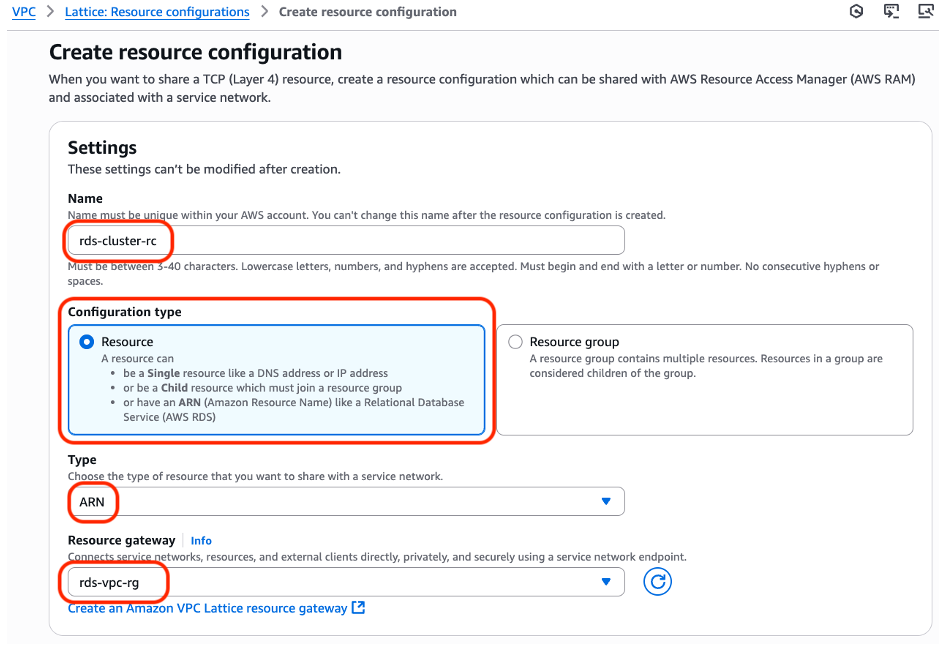
Step 2: Create Resource configuration assigned to Resource Gateway
- Open the Amazon VPC console.
- In the navigation pane under PrivateLink and Lattice choose Resource configurations.
- Choose Create Resource configuration.
- Provide Name.
- Check the Resource group option.
- Choose Resource gateway created in step 1. from the menu.
- Edit Port ranges appropriate for supported application.
- Choose Create resource configuration.
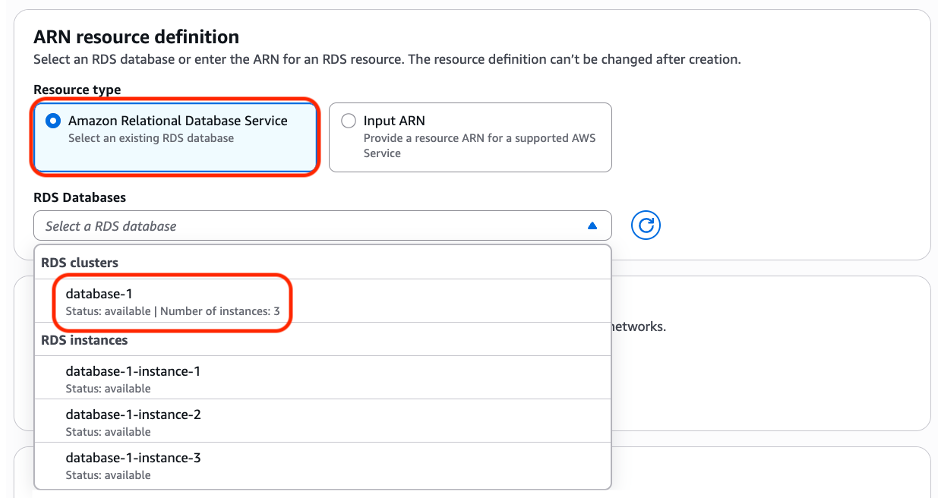
Figure 6: Choose the ARN Type for Resource Configuration creation
Figure 7: Resource type Amazon Relation Database Service, then add the Amazon RDS cluster
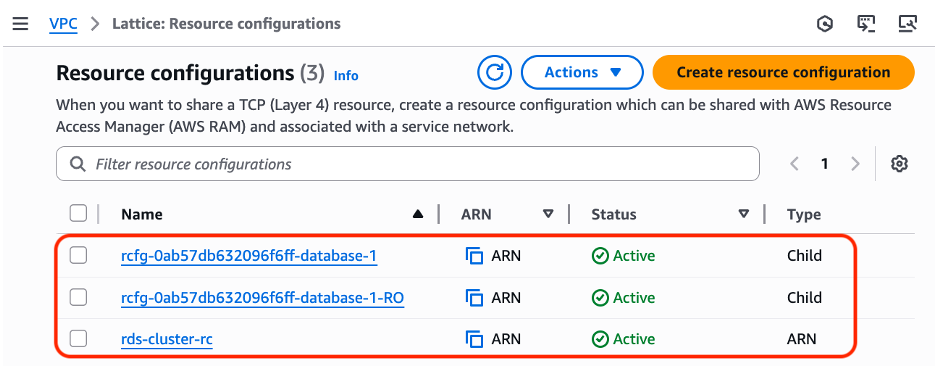
Figure 8: Check the Resource configurations have been added for the Amazon RDS nodes
Step 3: Add Resource configuration to Service network
- Open the Amazon VPC console.
- In the navigation pane under PrivateLink and Lattice choose Service networks.
- Choose the Resource configuration associations tab.
- Choose Create configuration.
- Choose Save changes.
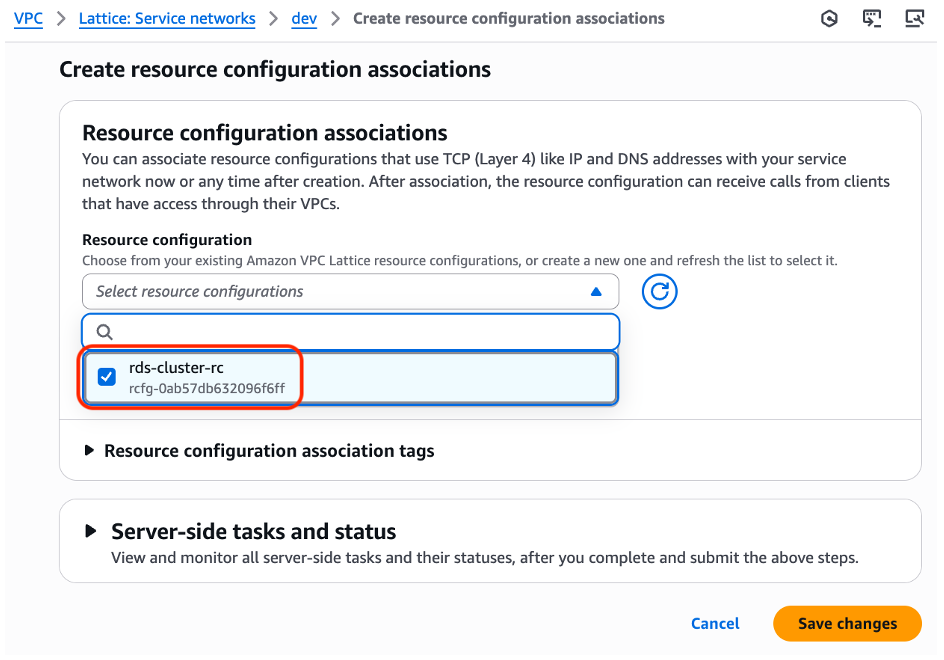
Figure 9: Creating Resource configuration association
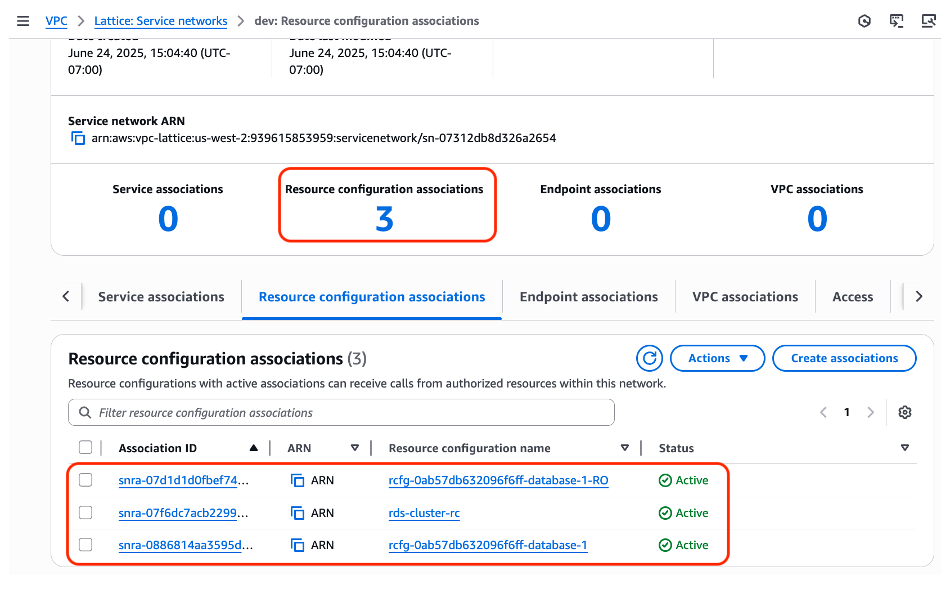
Figure 10: Checking the resource configuration associations for the Service network
Resource associations exist for read/write (RW) and read only (RO) nodes of the Amazon RDS cluster. You can access these nodes in the Consumer VPC and over VPC Lattice, using the same DNS names as in the VPC where the Amazon RDS cluster has been deployed. Your application must identify which nodes are RW and which are RO.
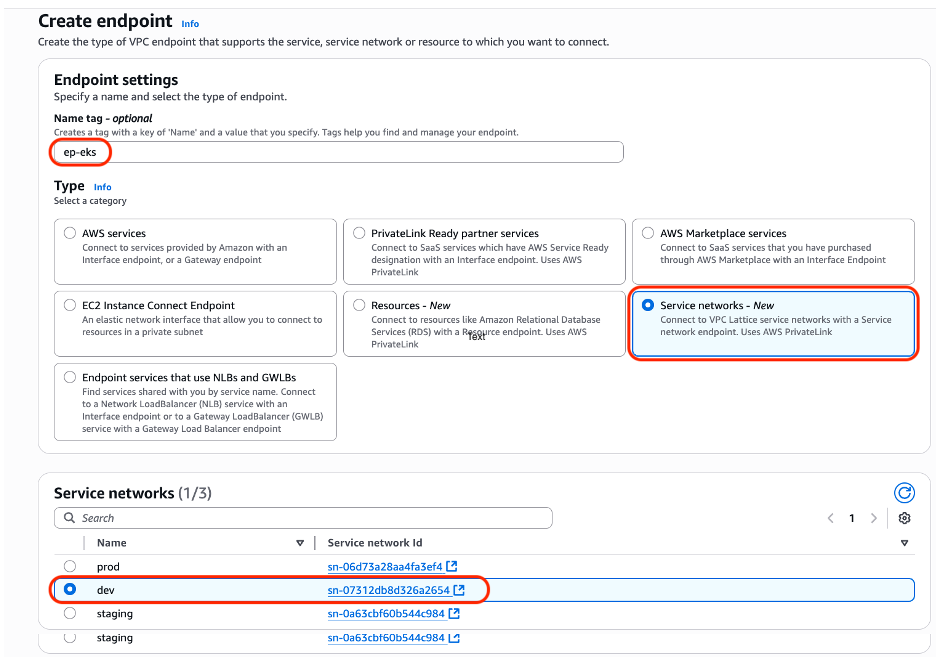
Step 4: Create an endpoint in the “eks-cluster-vpc” VPC
- Open the Amazon VPC console.
- In the navigation pane under PrivateLink and Lattice choose Endpoints.
- Choose Create endpoint.
- Enter Name tag.
- Choose Service networks.
- Choose Service network.
- Specify VPC.
- Choose Availability Zone and Subnet ID where you’d like to add endpoints.
Figure 11: Creating endpoint, specifying Service network, and “eks-cluster-vpc” VPC
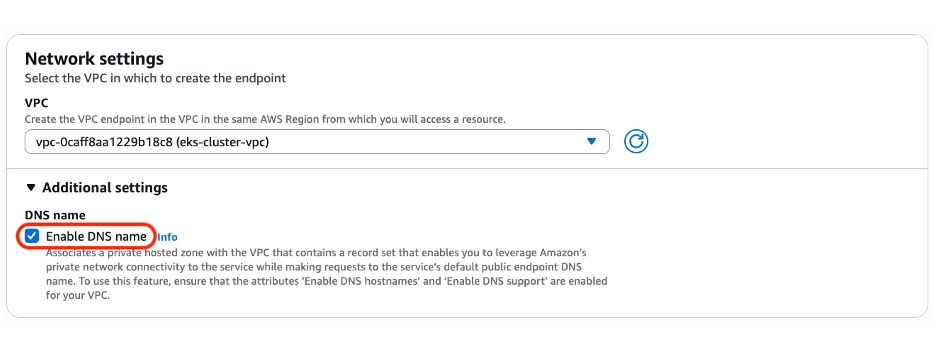
Figure 12: IMPORTANT: check Enable DNS name box
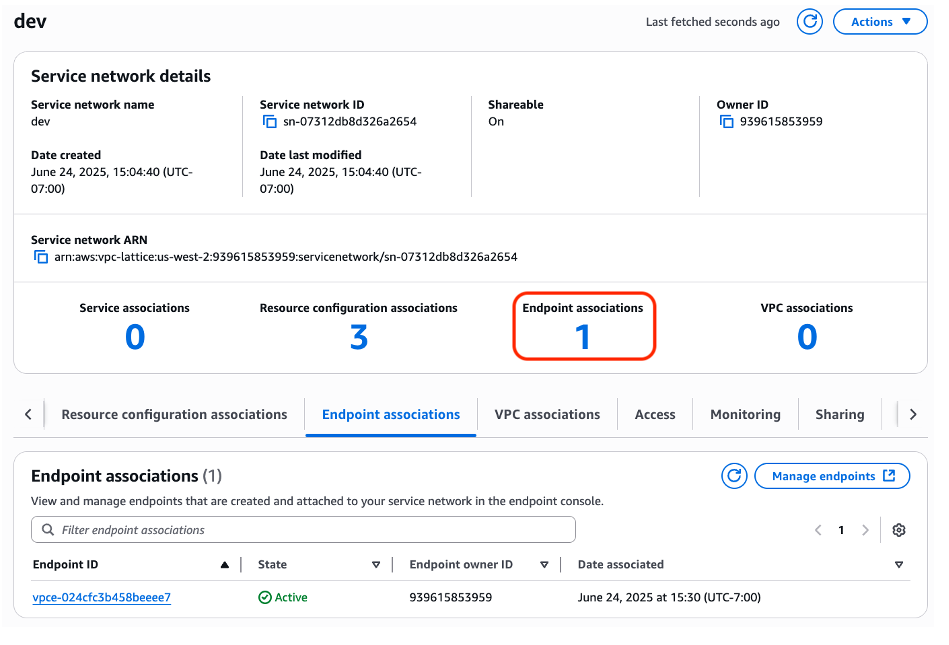
Figure 13: Service network displaying additional Endpoint association
Step 5: DNS validation
We checked the Enable DNS name box, as shown in Figure 12, thus the DNS is automated, creating DNS in the Consumer VPC that map to the TCP resource being shared. Figure 14 shows the Amazon RDS clusters’ DNS entries for Writer, and Reader (RO). Figures 15 and 16 demonstrate the resolution of the Reader endpoint in both the “rds-vpc”, and “eks-cluster-vpc” VPCs.
Figure 14: DNS for the RW node, highlighted, and RO Amazon RDS nodes
You can validate the DNS lookup for RW’s URL in both the rds-vpc and eks-cluster-vpc VPCs using the dig command (Figure 15 and Figure 16).
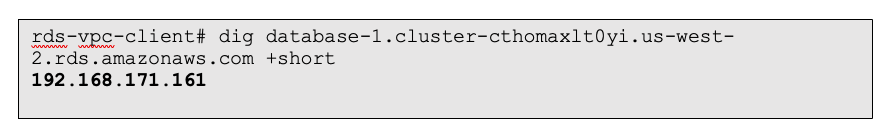
Figure 15: DNS resolution from a client in the “rds-vpc” VPC
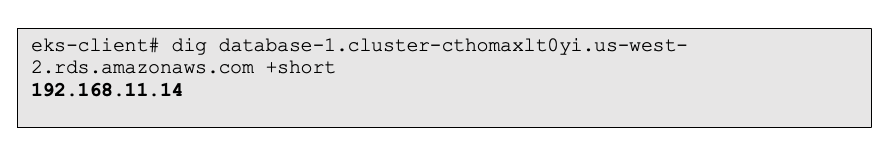
Figure 16: DNS resolution from a client in the “eks-cluster-vpc” VPC, resolving to the SN-E address
Step 6: Connect to Amazon RDS cluster over VPC Lattice from test Pod
- Open the console with kubectl and access the test cluster in the eks-cluster-vpc VPC.
- Run a test pod with MySQL client. mysql -u admin -p -h database-1.cluster-cthomaxlt0yi.us-west-2.rds.amazonaws.com
- Access the RW node using MySQL command and the DNS entry for the Amazon RDS endpoint.
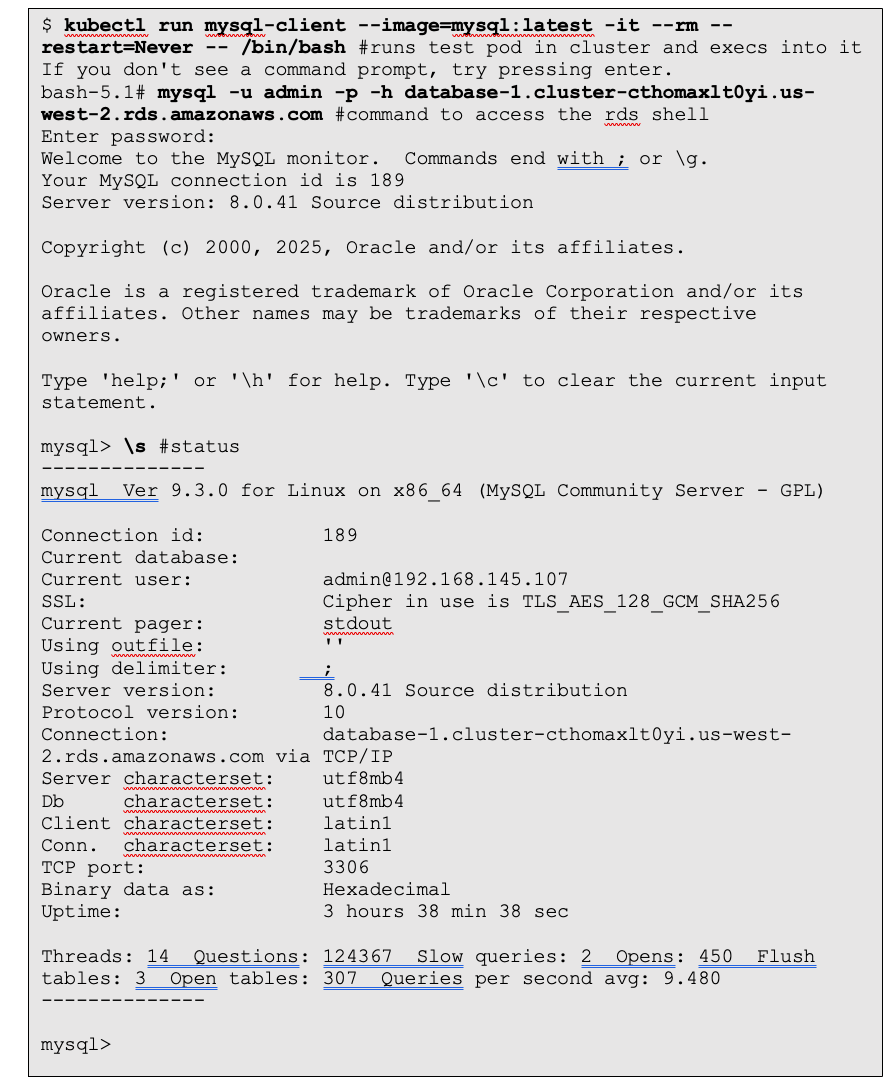
- Connectivity is established when you see the mysql> prompt, as shown in Figure 36.
- Exit to terminate pod.
Figure 17: Running test pod to access MySQL over VPC Lattice
Cleaning up
To avoid unnecessary costs ensure you:
Delete:
- Endpoint in the “eks-cluster-vpc” VPC
- Resource configuration associations in the service network
- Resource group configuration assigned to Resource Gateway
- Resource Gateway
- Any Security Groups created
If you created the database, cluster, and VPCs for this test please ensure they are deleted:
- Amazon RDS cluster
- Amazon EKS cluster
- VPCs
Conclusion
This post demonstrates how Amazon VPC Lattice provides simple, secure, access to a Multi-AZ RDS Cluster, using the same VPC Lattice environment that you are familiar with for your application APIs. It reduces IP address management, and avoids the need to configure and manage routing, allowing you to focus on application development. We encourage you to test VPC Lattice in your own environment to see how VPC Lattice can help simplify your application networking. If you have questions about this post, then start a new thread on AWS re:Post or contact AWS Support.