The Internet of Things on AWS – Official Blog
Identify misconfigured IoT policies using AWS IoT Device Defender
Introduction We are excited to announce a new AWS IoT Device Defender audit feature to identify potential misconfigurations when using wild cards in Internet of Things (IoT) policies. AWS IoT Device Defender is a fully managed IoT security service that enables you to audit and monitor your IoT device fleet and secure your IoT configurations […]
Schedule remote operations using AWS IoT Device Management Jobs
Introduction Once Internet of Things (IoT) devices are deployed in the field, on-site intervention can be challenging, expensive, and may not be feasible due to technical and logistical constraints. The ability to perform remote updates on your IoT device software is an important factor that improves your IoT application’s lifespan and operational resilience, provisions the […]
Identifying IoT device certificates with a revoked intermediate CA using AWS IoT Device Defender
Introduction Dynamically verifiable device identity is a foundational component of a Zero Trust Architecture (ZTA). Ongoing dynamic evaluation of identity and trust requires complete and timely visibility into relevant components of that identity. Active device certificates issued by a revoked intermediate Certificate Authority (CA) can pose a security threat due to the intermediate CA being […]
Tracking Assets using AWS IoT Core and Amazon Location Service
In this post, we explore the recently launched “location action” feature that connects AWS IoT Core with Amazon Location Service trackers, creating a scalable, simple, and cost effective way to track and store IoT device location updates. Tracking resources and real-world assets is a critical part of any logistics and operations workflow. Companies need a […]
Enhancing IoT device security using Hardware Security Modules and AWS IoT Device SDK
Introduction Security of operations and security of data are among the top priorities of customers dealing with sensitive information or operating in highly regulated markets. Internet of Things (IoT) customers have the additional challenge of enabling high security standards for IoT communications to their cloud platforms. Data encryption with asymmetric algorithms and cryptographic keys are […]
How to get started with the new AWS IoT Core Device Location service
Introduction The new AWS IoT Core Device Location feature allows Internet of Things (IoT) devices to retrieve and report their current location without relying on Global Positioning System (GPS) hardware. Devices and clients connected to AWS IoT Core can now use cloud-assisted Global Navigation Satellite System(GNSS), WiFi scan, cellular triangulation, and reverse IP lookup techniques […]
Generating insights from vehicle data with AWS IoT FleetWise: Introduction (Part 1)
This blog post is written by Senior IoT Specialist Solutions Architect Andrei Svirida. Automakers, fleet operators, and automotive suppliers are digitalizing their products and services, and vehicle data is fueling this digitalization in several ways. First, access to vehicle data allows evolutionary improvement of existing business processes. One example of this is faster detection of […]
Building a Digital Twin with Photogrammetry and AWS IoT TwinMaker
Introduction In this blog post, you will learn how you can use photographs taken by a drone to create a 3D model of real world environments within a digital twin. Digital twins are virtual representations of physical systems that are regularly updated with data to mimic the structure, state, and behavior of the assets they […]
Use AWS IoT Core MQTT broker with standard MQTT libraries
Introduction AWS IoT Core connects Internet of Things (IoT) devices to AWS IoT and other AWS services. Devices and clients can use the MQTT protocol to publish and subscribe to messages. MQTT libraries, such as the AWS IoT Device SDKs, include open-source libraries, developer guides with samples, and porting guides so that you can build innovative IoT […]
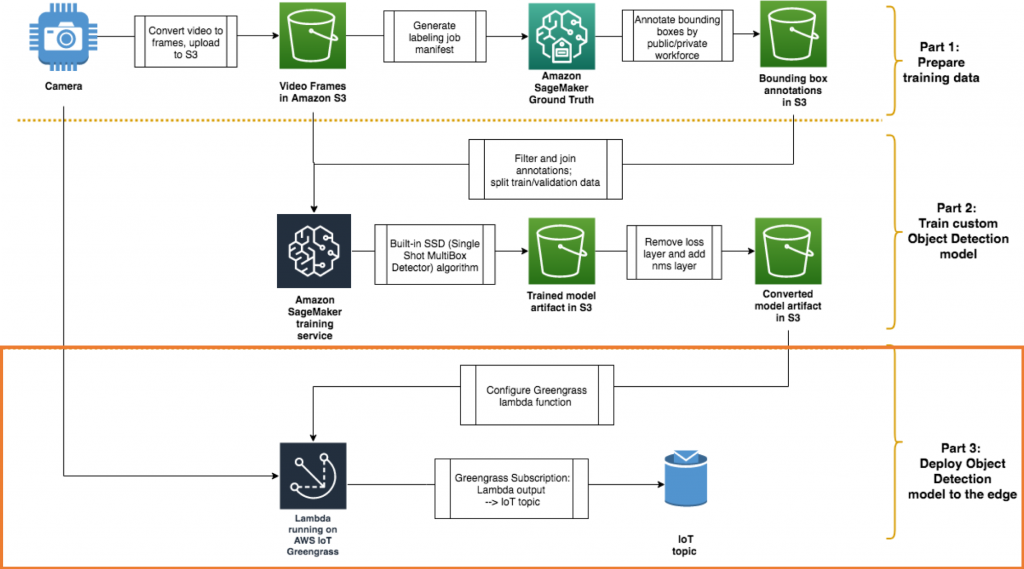
Training the Amazon SageMaker object detection model and running it on AWS IoT Greengrass – Part 3 of 3: Deploying to the edge
Post by Angela Wang and Tanner McRae, Senior Engineers on the AWS Solutions Architecture R&D and Innovation team This post is the third in a series on how to build and deploy a custom object detection model to the edge using Amazon SageMaker and AWS IoT Greengrass. In the previous 2 parts of the series, we walked […]