AWS Architecture Blog
Category: Security, Identity, & Compliance
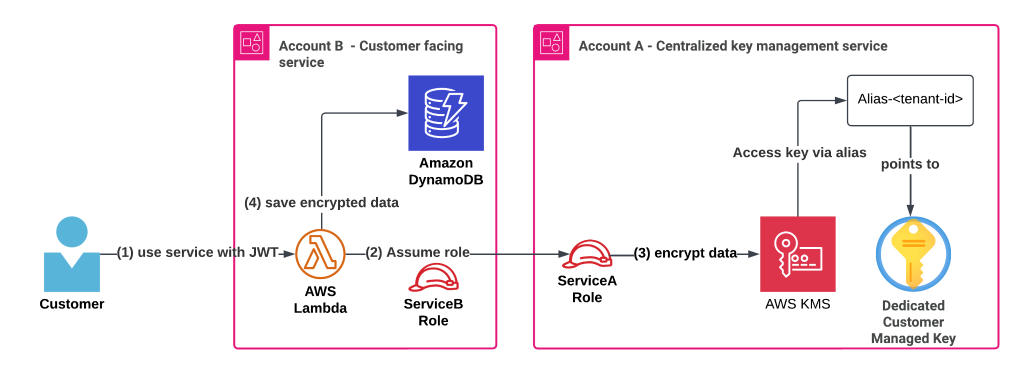
Simplify multi-tenant encryption with a cost-conscious AWS KMS key strategy
In this post, we explore an efficient approach to managing encryption keys in a multi-tenant SaaS environment through centralization, addressing challenges like key proliferation, rising costs, and operational complexity across multiple AWS accounts and services. We demonstrate how implementing a centralized key management strategy using a single AWS KMS key per tenant can maintain security and compliance while reducing operational overhead as organizations scale.
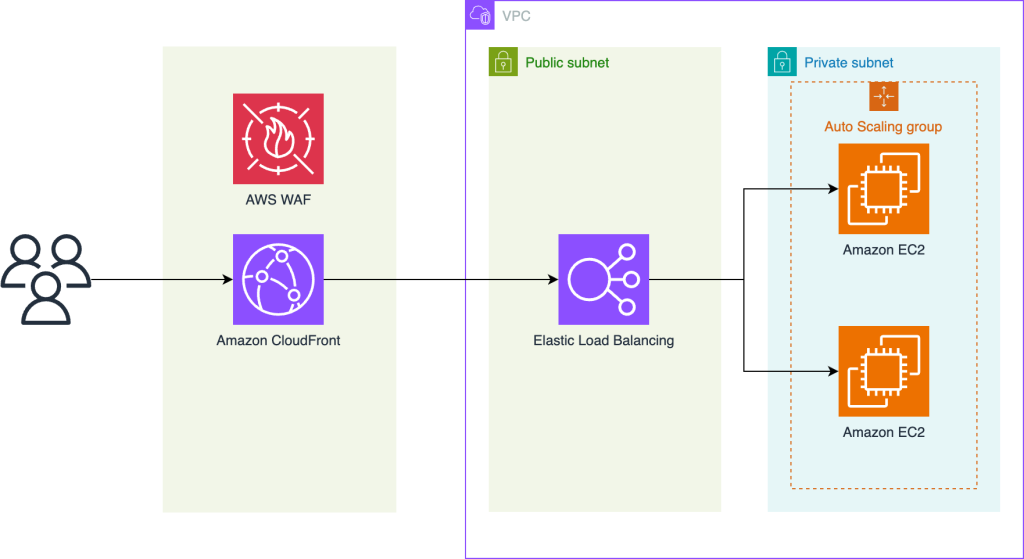
How Scale to Win uses AWS WAF to block DDoS events
In this post, you’ll learn how Scale to Win configured their network topology and AWS WAF to protect against DDoS events that reached peaks of over 2 million requests per second during the 2024 US presidential election campaign season. The post details how they implemented comprehensive DDoS protection by segmenting human and machine traffic, using tiered rate limits with CAPTCHA, and preventing CAPTCHA token reuse through AWS WAF Bot Control.
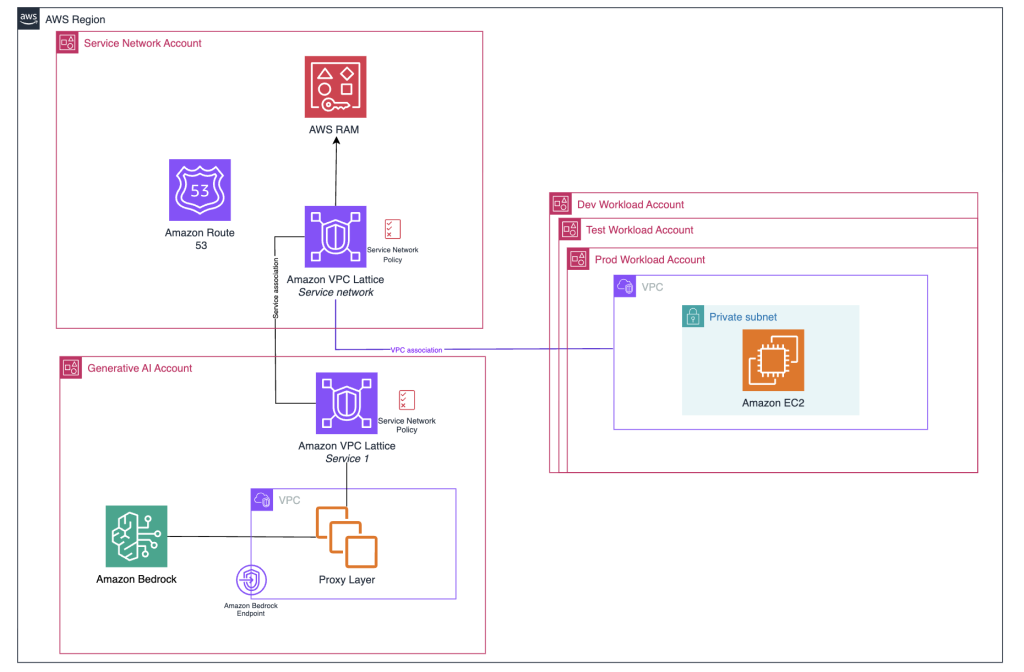
Amazon Bedrock baseline architecture in an AWS landing zone
In this post, we explore the Amazon Bedrock baseline architecture and how you can secure and control network access to your various Amazon Bedrock capabilities within AWS network services and tools. We discuss key design considerations, such as using Amazon VPC Lattice auth policies, Amazon Virtual Private Cloud (Amazon VPC) endpoints, and AWS Identity and Access Management (IAM) to restrict and monitor access to your Amazon Bedrock capabilities.
How UNiDAYS achieved AWS Region expansion in 3 weeks
In this post, we share how UNiDAYS achieved AWS Region expansion in just 3 weeks using AWS services.
From virtual machine to Kubernetes to serverless: How dacadoo saved 78% on cloud costs and automated operations
In this post, we walk you step-by-step through dacadoo’s journey of embracing managed services, highlighting their architectural decisions as we go.
Converting stateful application to stateless using AWS services
Designing a system to be either stateful or stateless is an important choice with tradeoffs regarding its performance and scalability. In a stateful system, data from one session is carried over to the next. A stateless system doesn’t preserve data between sessions and depends on external entities such as databases or cache to manage state. […]
Operating models for Web App Security Governance in AWS
For most organizations, protecting their high value assets is a top priority. AWS Web Application Firewall (AWS WAF) is an industry leading solution that protects web applications from the evolving threat landscape, which includes common web exploits and bots. These threats affect availability, compromise security, or can consume excessive resources. Though AWS WAF is a […]
Let’s Architect! Security in software architectures
Security is fundamental for each product and service you are building with. Whether you are working on the back-end or the data and machine learning components of a system, the solution should be securely built. In 2022, we discussed security in our post Let’s Architect! Architecting for Security. Today, we take a closer look at […]
How Thomson Reuters monitors and tracks AWS Health alerts at scale
Thomson Reuters Corporation is a leading provider of business information services. The company’s products include highly specialized information-enabled software and tools for legal, tax, accounting and compliance professionals combined with the world’s most trusted global news service: Reuters. Thomson Reuters is committed to a cloud first strategy on AWS, with thousands of applications hosted on AWS […]
dApp authentication with Amazon Cognito and Web3 proxy with Amazon API Gateway
If your decentralized application (dApp) must interact directly with AWS services like Amazon S3 or Amazon API Gateway, you must authorize your users by granting them temporary AWS credentials. This solution uses Amazon Cognito in combination with your users’ digital wallet to obtain valid Amazon Cognito identities and temporary AWS credentials for your users. It […]