AWS Partner Network (APN) Blog
Reduce Vulnerabilities on AWS with Orca Security’s Reachability Analysis
By Merin Eralil, ISV Security Partner Solutions Architect – AWS
By Jason Patterson, WW Security Partner Solutions Architect – AWS
By Todd Stansfield, Product Marketing Manager – Orca Security
 |
| Orca Security |
 |
According to the 2025 Verizon Data Breach Investigations Report, vulnerability exploitation has increased by 34% year over year. Meanwhile, VulnCheck’s 1H-2025 Exploit Intelligence Report found that nearly one-third of all exploits now occur before or on the day of Critical Vulnerability Exploit (CVE) disclosure. These findings reflect a troubling trend: threat actors are moving faster than ever, dramatically reducing the window for defenders to respond. Reachability Analysis offers an effective alternative to traditional vulnerability management approaches, helping security teams focus on vulnerabilities that are actually exploitable in their environment. This not only improves remediation efficiency, but also reduces noise and alert fatigue. In this article, we define what Reachability Analysis is, why it matters, and how Orca Security’s Solution can help organizations secure their AWS environments.
What is Reachability Analysis?
Reachability Analysis is a technique to understand which vulnerable software components are being used when an application runs. In cloud-native development, applications often include a wide range of third-party packages, some of which are essential for runtime, while others are included automatically during the build process but are never used once the application is deployed.
For example, container images frequently contain packages that are installed as transitive dependencies of other tools, but they are rarely invoked by the application itself. If a vulnerability is found in one of these unused components, it may pose little to no practical risk, yet traditional scanners may qualify it as critical.
Reachability Analysis helps security teams distinguish between vulnerabilities in components that are executed at runtime and those that are not. This context allows teams to focus their limited resources on exploitable risks, reduce alert fatigue, and improve overall cloud security posture.
Why is Reachability Analysis Important?
An analysis by the Orca Research Pod found that many security practitioners receive more than 500 alerts daily and miss critical risks on a daily or weekly basis. This alert fatigue is often caused by security tools that generate extensive findings without prioritizing them effectively.
Traditional Software Composition Analysis (SCA) tools, while useful for identifying open-source vulnerabilities in codebases, lack runtime visibility. They don’t reveal whether a vulnerable software component is invoked in production, meaning teams may waste valuable remediation effort on a risk attackers can’t exploit.
Orca Security addresses this with two advanced techniques: Agentless Reachability Analysis and Dynamic Reachability Analysis. Both help determine which vulnerabilities are reachable, enabling teams to focus only on those that pose real risk.
- Agentless Reachability Analysis performs deep static inspection without deploying agents, identifying which packages are installed and actually used by analyzing code paths and configurations.
- Dynamic Reachability Analysis complements this by capturing runtime telemetry to determine which vulnerable components are executed during application operation.
This dual approach reduces alert volume and remediation effort by eliminating noise and highlighting what truly matters.
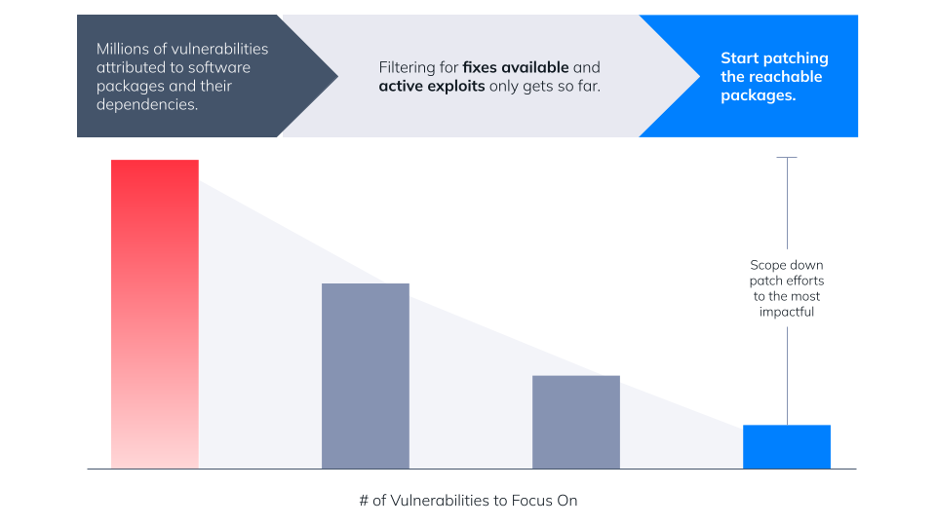
Figure 1: Reachability Analysis prioritizes vulnerability patching efforts
How Does Reachability Analysis Work?
Orca Security’s Agentless and Dynamic Reachability Analysis offer two complementary, yet distinct and innovative methods to deliver high-confidence vulnerability prioritization.
Agentless Reachability Analysis
Using its patented SideScanning™ technology, Orca Security performs deep static analysis on workloads without requiring agents. After a one-time integration into your AWS environment using read-only permissions, Orca begins scanning your cloud infrastructure including asset configurations, data storage, IAM roles and policies, network topology, and security settings.
It then performs reachability analysis by tracing execution paths from defined entry points—such as a container’s entry script or an application’s main function—using a combination of code analysis, symbolic execution, and configuration inspection.
- Code analysis generates control flow graphs to identify which functions, libraries, and packages are directly or indirectly referenced in the application code.
- Symbolic execution simulates how data moves through different paths in the program, helping determine how and when certain components might be executed under real-world conditions.
- Configuration analysis inspects files (e.g., uWSGI ini, Node’s package.json) that define how the runtime environment is set up, identifying packages that may be dynamically loaded during execution.
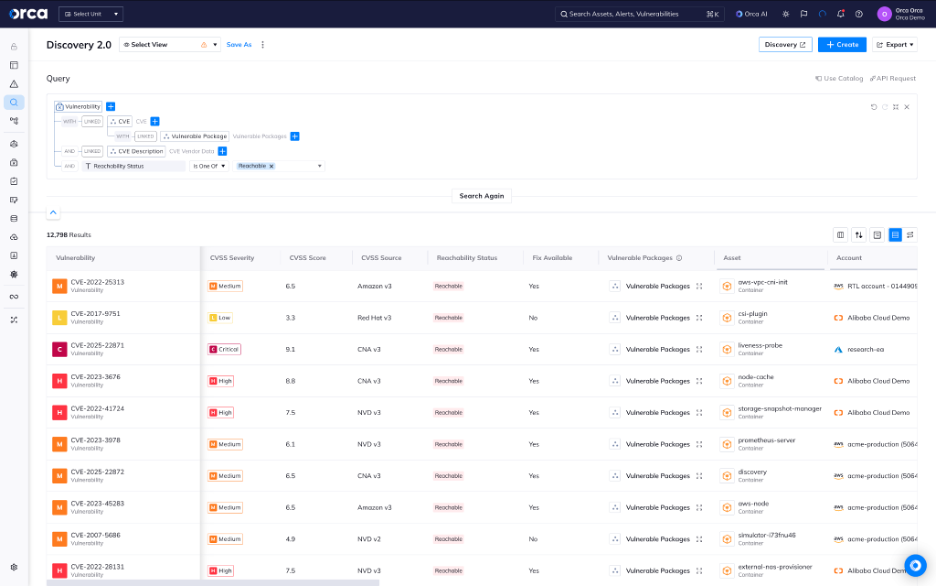
Figure 2 is an example of how this comprehensive approach enables Orca to determine which vulnerabilities exist in packages that could be executed at runtime, giving security teams high-confidence signals for prioritization.
Figure 2: Reachable vulnerable software packages detected by agentless Orca Platform
Dynamic Reachability Analysis
To supplement agentless analysis, Orca incorporates runtime telemetry using Orca Sensor, a lightweight, extended Berkeley Packet Filter (eBPF) based sensor. Each sensor gathers live runtime context, such as which components are loaded into memory and executed. Importantly, these sensors are designed for minimal overhead and are not required for agentless scanning.
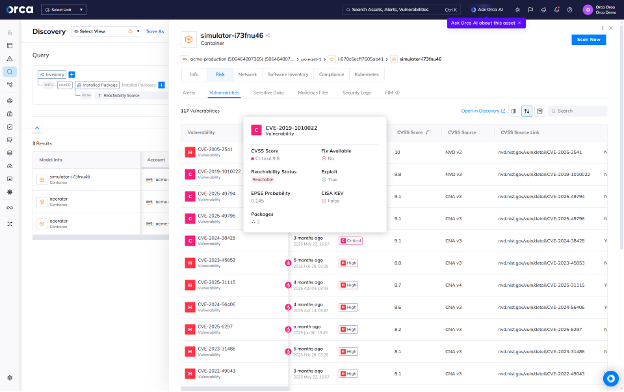
In Figure 3, security analysts can see a list of reachable and unreachable vulnerabilities found on a running container. Dynamic Reachability Analysis enables Orca to assess if a vulnerability is exercised in production, providing a clear signal for prioritization. It also detects vulnerabilities that static analysis may miss, such as those introduced via dynamic loading or at runtime.
Figure 3: List of reachable and unreachable vulnerabilities found on a running container through Orca Sensor
About Orca Agentless and Dynamic Reachability Analysis on AWS
The Orca Cloud Security Platform delivers agentless-first visibility across AWS environments, helping teams focus on vulnerabilities that are truly exploitable.
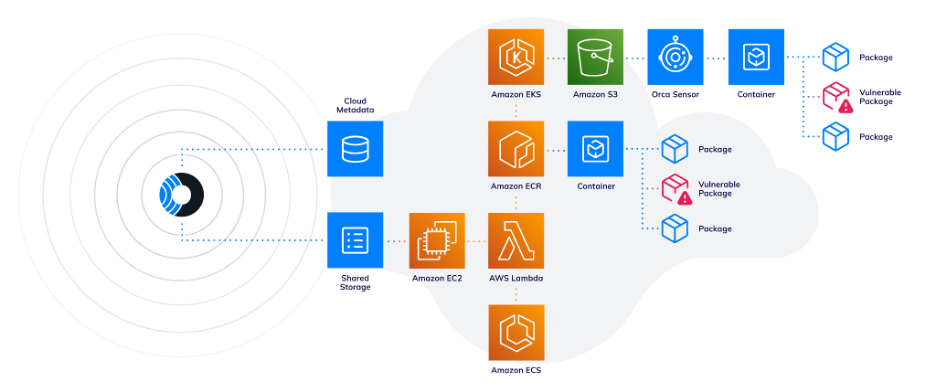
Agentless Reachability Analysis performs deep static inspection of workloads and applications hosted in AWS. For example, Orca scans container images in Amazon Elastic Container Registry (Amazon ECR), inspects workloads on Amazon Elastic Compute Cloud (Amazon EC2), analyzes deployed functions in AWS Lambda and containerized workloads in Amazon Elastic Container Service (Amazon ECS). This out-of-band analysis identifies which packages are present and could be executed at runtime without deploying agents or impacting performance.
Dynamic Reachability Analysis adds runtime visibility by collecting telemetry from live AWS workloads. For instance, Orca Sensor can run in Amazon Elastic Kubernetes Service (Amazon EKS) clusters to detect which packages and functions are actually executed during operation, with telemetry securely stored in Amazon Simple Storage Service (Amazon S3) for processing. This helps capture risks that static analysis may miss, such as vulnerabilities in dynamically loaded code or short-lived containers.
By combining static and runtime insights, Orca on AWS give customers high-confidence vulnerability prioritization, reducing noise and enabling faster, more targeted remediation.
Figure 4: Orca supports multiple AWS services for Agentless and Dynamic Reachability Analysis
Conclusion
Cloud security teams are overwhelmed by alerts, and traditional vulnerability management approaches fail to provide the context needed for effective prioritization. Tools based on Common Vulnerability Scoring System (CVSS) scores or those that utilize heavy weight legacy agents frequently miss the mark, leaving organizations at risk.
Orca Security is redefining vulnerability management on AWS with Agentless and Dynamic Reachability Analysis. By helping teams focus on the vulnerabilities that are actually exploitable in production, this combined approach can provide 90% reduction in exploitable vulnerabilities, accelerates remediation, and improves security outcomes.
To learn more, schedule a demo or try Orca for free on AWS Marketplace.
.
Orca Security – AWS Partner Spotlight
Orca Security is an AWS Specialization Partner that provides cloud-wide, workload-deep, context-aware security and compliance for AWS without the gaps in coverage, alert fatigue, and operational costs of agent-based solutions.