AWS Partner Network (APN) Blog
Rapidly Build a Generative AI Landing Zone on AWS
By Kuldeep Singh, Global Principal Partner Development Manager, GSI – AWS
By Amit Chowdhury, Sr. Partner Solutions Architect, GSI – AWS
Organizations are eager to harness the transformative power of generative AI (GenAI) to drive innovation, enhance productivity, and create competitive advantages. They envision a future where AI capabilities are seamlessly integrated into their operations while maintaining robust security and compliance standards. Our customers and partners have asked for a framework that enables quick experimentation while providing the necessary governance guardrails to scale confidently across their enterprise. In this blog, you will learn how to implement a secure and compliant GenAI Landing Zone on AWS, with code samples and ready-to-deploy architecture.
Customer Challenge
Industry surveys consistently show that most AI pilots never reach production. Security reviews and compliance audits rank among the top blockers, and every week of delay erodes stakeholder confidence and impacts the budget. Partners tell us that their customers grapple with three recurring problems:
- Compliance drag: Legal and security teams often seek a review of every new prompt and model call, stretching “time-to-first experiment” from days to months. Lack of the right audit and security tools to meet legal and compliance needs adds to the delay.
- Pilot-to-production gap: Code that dazzles during a demo often needs extensive re-engineering for audit trails, monitoring, and cost controls.
- Limited visibility: When latency, quality, or spend data stay hidden, leadership hesitates to fund the next phase. Leadership needs tooling and processes to provide better visibility and decision making.
Working backwards from those pain points, we built a GenAI Landing Zone, a five-layer architecture that stitches governance and developers. You can deploy it today with AWS services and give customers a clear path from POC to production.
Partner-Led Solution and Customer Benefits
The GenAI Landing Zone tackles the three problems head-on:
- Guardrails enforced on every prompt. Amazon Bedrock Guardrails, AWS Identity and Access Management (IAM), and AWS Key Management Service (AWS KMS) apply topic blocking, PII redaction, encryption, and audit logging automatically.
- Same-day sandboxes. Amazon Bedrock Playground, Amazon Q Developer, and Amazon Simple Storage Service (Amazon S3) spin up inside the customer’s account within minutes, so builders can test Large Language Models (LLMs) such as Amazon Nova, Anthropic Claude, or Meta’s Llama before enthusiasm fades.
- Reusable blueprints. AWS Cloud Development Kit (CDK) and Infrastructure as Code (IaC) modules for Retrieval-Augmented Generation (RAG), fine-tuning, and agentic workflows turn weeks of infrastructure wiring into a few parameter updates.
- Built-in observability and cost tracking. Amazon CloudWatch, Amazon Bedrock traces, AWS CloudTrail Lake, and AWS Cost Explorer tags surface latency, guardrail hits, and cost in near real time.
- Continuous governance. AWS Control Tower, Service Control Policies (SCPs), and a drift-detection AWS Lambda function keep pilots and production in the same secure envelope.
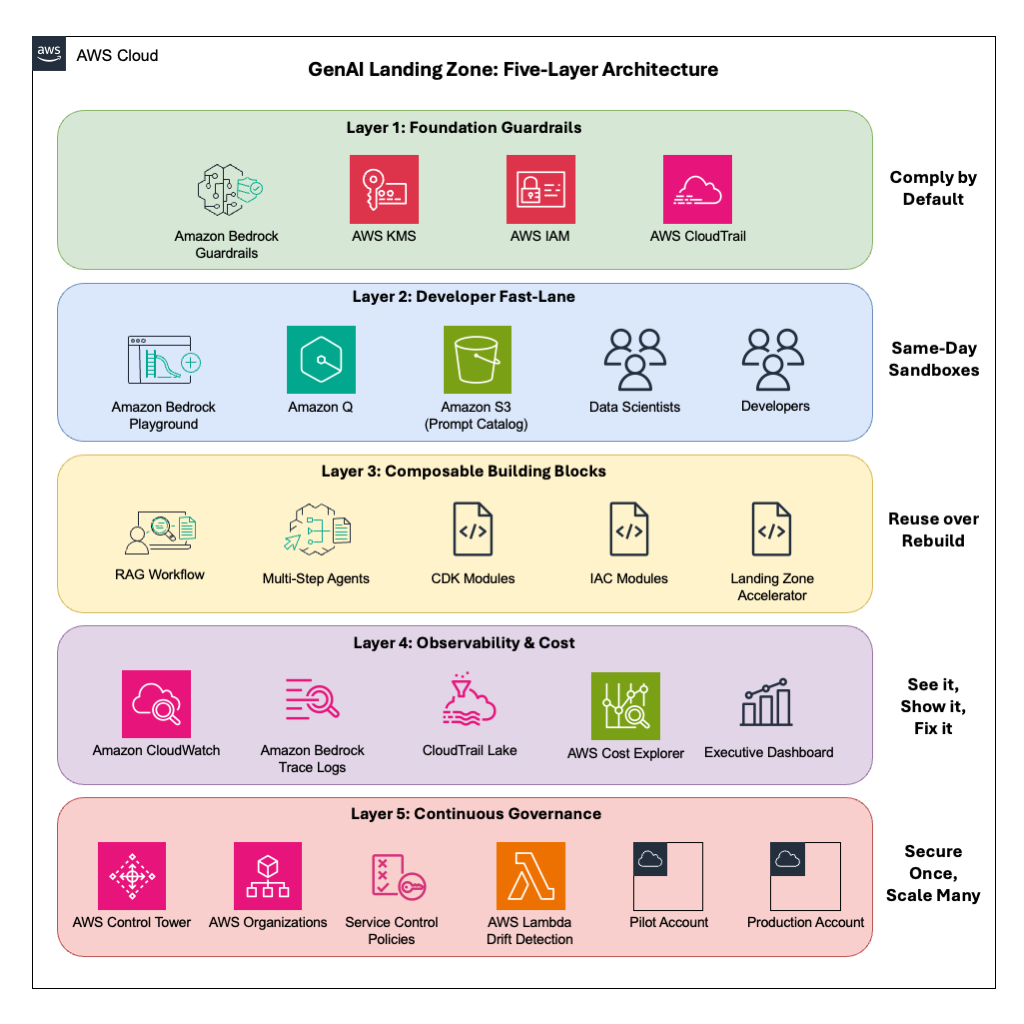
Figure 1 – GenAI Landing Zone on AWS – Five-Layer Architecture
Five Layers of the GenAI Landing Zone
Foundation Guardrails – Comply by Default
Attach an Amazon Bedrock Guardrails policy that aligns to your customer’s data-classification matrix. The policy blocks disallowed topics, strips PII (Personally Identifiable Information), and scores hallucination risk. IAM roles restrict access to approved models, KMS encrypts data, and AWS CloudTrail records an immutable audit log.
Developer Fast-Lane – Same-Day Sandboxes
Amazon Bedrock Playground launches inside the customer’s VPC in minutes, giving data scientists a secure GUI to compare models and refine prompts. Amazon Q Developer adds AI-powered code suggestions for developers, natural-language SQL for analysts, and workflow agents for project managers.
Composable Building Blocks – Reuse over Rebuild
Open-source CDK and Terraform modules ship common Generative AI patterns:
- RAG pipeline. Serverless document ingest → Amazon OpenSearch Serverless (or Amazon Aurora PostgreSQL) as the vector database → Amazon Bedrock model.
- Fine-tune workflow. Amazon SageMaker Data Wrangler → Amazon Bedrock fine-tuning or continued pre-training.
- Multi-step agents. AWS Step Functions + Lambda orchestration, with Amazon Bedrock Guardrails enforced on each model call.
Observability & Cost – See It, Show It, Fix It
Each response from an Amazon Bedrock Agent is accompanied by a trace that details the steps being orchestrated by the agent. Amazon Bedrock traces streams prompt metadata to CloudWatch Logs. A Lambda function summarizes and publishes the latency, guardrail hits, and token counts to a dashboard which executives can review for informed decision making. Cost Explorer automatically tags each Amazon Bedrock request by project and environment.
Continuous Governance – Secure Once, Scale Many
AWS Control Tower launches new accounts with the guardrail policy, IAM roles, KMS keys, and SCPs already wired in. A drift-detection Lambda scans for policy violations and rolls back non-compliant resources, then posts a report to Slack. Once your customizations are incorporated into the POC IaC stacks, it becomes easy to deploy the same stack to Production or lower environments. All services used in the solution are either AWS-managed or serverless which provide elasticity and scalability out-of-the-box.
Deploy the Landing Zone
1. Prerequisite
You’ll need an AWS account with permissions to create and manage resources, as well as the AWS CLI installed and configured with your credentials. Also install AWS CDK.
2. Ready-Made Guardrail Policies
Apply a Policy Bundle: The policy example bundle below is for financial services. A similar policy can be used for healthcare or public-sector workloads to help customers meet their specific compliance requirements.
Sample code is provided below. Treat these as starter templates which can be used to build your own or partner-specific solutions. Be sure to validate with your security, compliance, and legal teams before production use.
Bedrock Guardrails Policy (guardrail-finserv.json)
3. Deploy & Experiment: Five CDK stacks
Use the sample code below to run five CDK stacks, the entire deployment, including dashboards. Add file names for the 5 stacks (for example, LZ-Core.ts), these file names must match with the cdk deploy command in step 4 below.
LZCore – Guardrails, IAM, KMS
LZDev – Developer FastLane
LZ‑Governance – Continuous Governance
This CDK construct serves as a placeholder where you can add your own drift detection code.
4. Deploy the five stacks to build generative AI landing zone
(make sure file names match with CDK stack in step 3 above)
Guardrails, IAM, KMS: cdk deploy LZ-Core
Developer Fast-Lane: cdk deploy LZ-Dev
RAG reference architecture: cdk deploy LZ-RAG
Observability & Cost: cdk deploy LZ-Ops
Continuous Governance: cdk deploy LZ-Governance
Treat the code samples as starter templates. Review, configure and validate to ensure they align organization specific compliance requirements and risk tolerance. with your security, compliance, and legal teams before production use. Once the infrastructure is deployed, document your specific configurations and create internal guidelines to help teams across your organization utilize the GenAI Landing Zone efficiently and securely.
Conclusion
The generative AI Landing Zone offers a robust, scalable, and secure foundation for organizations looking to harness the power of generative AI on AWS. By implementing this five-layer architecture, organizations can reduce the time-to-market while maintaining strong governance and compliance standards.
Reach out to your AWS Account team to learn more about how to extend this solution.
Sample code, software libraries, command line tools, proofs of concept, templates, or other related technology are provided as AWS Content or Third-Party Content under the AWS Customer Agreement, or the relevant written agreement between you and AWS (whichever applies). You should not use this AWS Content or Third-Party Content in your production accounts, or on production or other critical data. You are responsible for testing, securing, and optimizing the AWS Content or Third-Party Content, such as sample code, as appropriate for production grade use based on your specific quality control practices and standards. Deploying AWS Content or Third-Party Content may incur AWS charges for creating or using AWS chargeable resources, such as running Amazon EC2 instances or using Amazon S3 storage.